Coldroot
Coldroot was first published as an open source RAT for macOS on Github on 2016, but no real malware was discovered until 2018. The malware is weaponized with a wide range of commands such as:- File/Folders control (move, reanme, delete) – Remote Desktop – Download, upload and executes files – Process control (list, execute, kill) – Taking screen shots – Gain accessibility rights by modifying TCC.db – KeyloggingThe malicious application arrives with a normal “document” icon, so a user might think he is opening a document rather than a malicious application.
Source: Digita Security
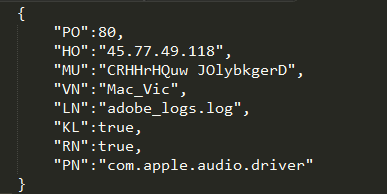
Once executed, the malware will try to get root access via popping a window asking the user for credentials. It will create a LaunchDaemon in order to persist system reboot (“/Library/LaunchDaemons/com.apple.audio.driver.plist”). The malware keep its configuration within a file in its application bundle (“MacOS/conx.wol”). We can see below its content:
Source: Digita Security
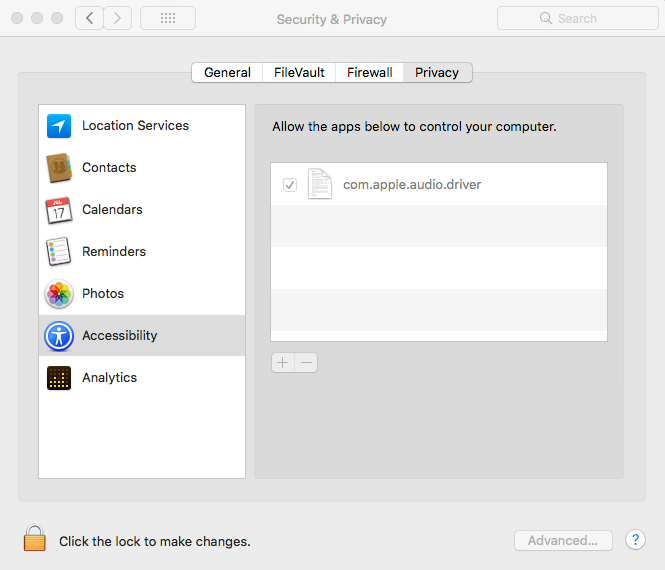
In addition it will modify the system security database file TCC.db to add itself as Accessibility application, meaning it will then have the ability to control the computer.
Source: Digita Security
Links:
Samples:
7e60c8ae77e20fbd7699187d0baf9ed0477e72f3