Eleanor
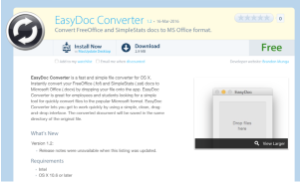
Eleanor is a bundle of several open source applications and scripts. Eleanor acts as an “EasyDoc Converter” app which purports to convert file formats into Microsoft Word files, but actually this malware opens a back door into Mac OS X systems via the Tor network. Its main purpose is to give an attacker a full control over infected machine, so the attacker could browse user files, execute applications, capture photos and gain access to webcams and remote code execution.Discovered in July 2016 by Bitdefender. The malware disributed as “EasyDoc Converter” that migrates documents from Windows to OS X. In fact, this “EasyDoc Converter” contains malicious functionality which tries to gain full control over the victim machine.Eleanor could be found on web sites that offer Mac applications, such as MacUpdate. Using free Pastebin account, after each infection the victim host name will be uploaded to Pastebin.It took three months until Eleanor was discovered, as the first infection was at April 2016.
Infection Vector
A user will be infected after downloading and installing “EasyDoc Converter”. Since the application is not signed with any certificate belongs to an Apple developer ID, it is more difficult to open it. By default, Mac OS X will not open unsigned apps.
Source: CheckPoint
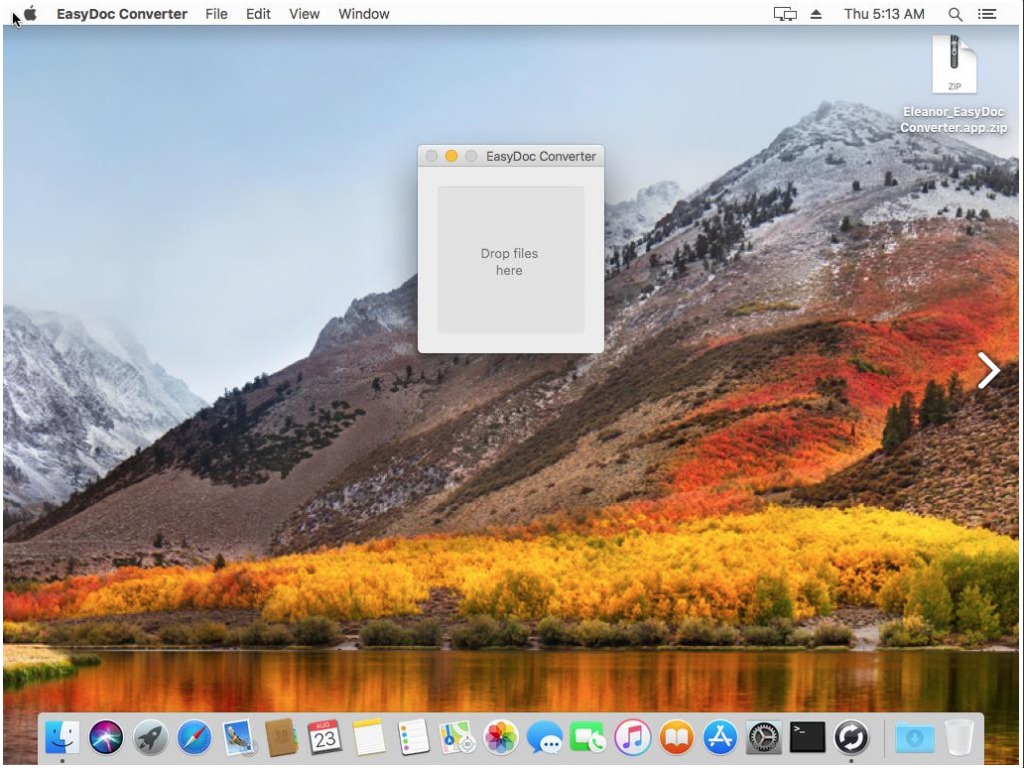
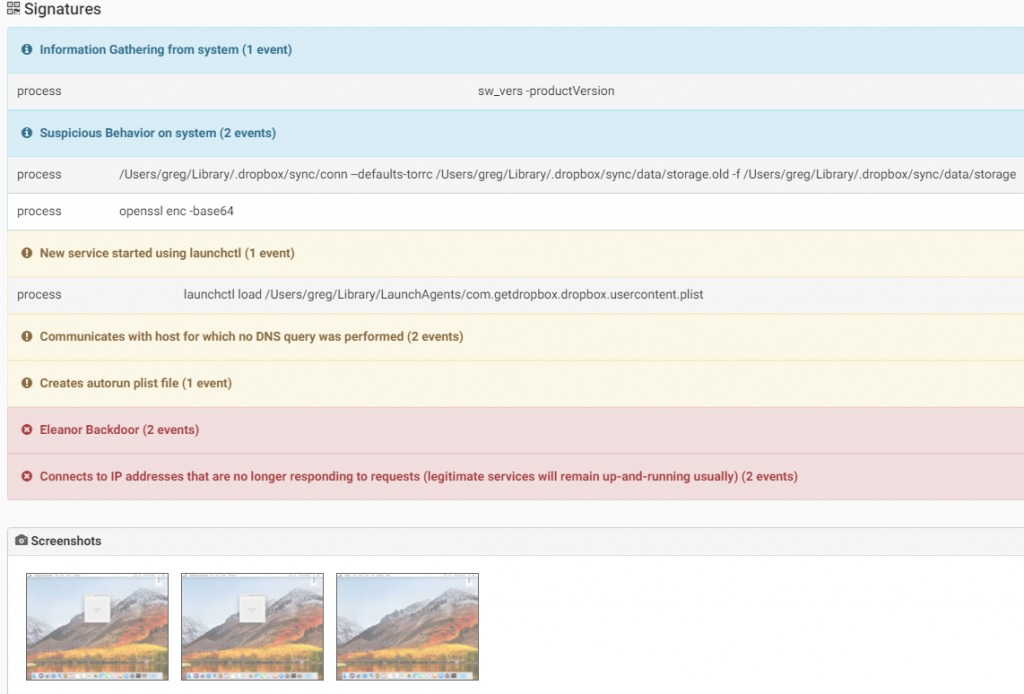
Once the infection is made, the malware installs several hidden services which give the attacker anonymous access to the infected machine via TOR network. The attacker then has the ability to access and modify files, execute shell commands, capture images and videos and more.First, the malware checks for the presence of Little Snitch (A 3rd party security product for mac). If Little Snitch is present, the malware will not infect the machine.The malware creates a hidden folder .dropbox and copies its components to this directory. Later, the malware shows a message that the current system is not supported by the application (so the user will not suspect about the malware).Eleanor creates three deamons:
-
Tor Hidden Service – creates a Tor hidden service which will give access to the second backdoor on the infected machine – the Web Service. It generates a Tor address in the format XXXpaceinbeg3yci.onion. The location of the service is: /Users/%CURRENT_USER%/Library/.dropbox/sync/connWhen Tor starts, it creates the HiddenServiceDir, and a public/private key pair. This hidden service gives access to two local services – a Web Service 127.0.0.1:9991 and SSH service 127.0.0.1:9992.
-
Web Service(PHP) – This daemon provides the attacker control over the infected machine. It can be accessed through the Tor-generated address described above.
The main page of the web service requires a password which should match a hardcoded string:$GLOBALS[‘pass’] = “15bd408e435dc1a1509911cfd8c312f46ed54226”; // sha1(md5(pass))After authentication is done the main control panel will be displayed. The control panel has the following abilities:File manager (view, edit, rename, delete, upload, download, archiver, etc)Command executionScript execution (php, perl, python, ruby, java, c)Shell via bind/reverse shell connectSimple packet crafterConnect to DBMS (mysql, sqlite, pdo)Process list/Task managerSend mail with attachment (you can attach local file on server)String conversionOther part of the web service is WebCam Control Panel. It has the ability to capture images and videos from user’s webcams using a tool it copies to ~/Library/.dropbox/utilities/wacaw.
- PasteBin Agent – after creating a unique Tor address, this daemon encrypts & uploads the address to Pastebin. The location of this daemon is /Users/%CURRENT_USER%/Library/.dropbox/check_hostname. It uses an RSA key contained in the application bundle, and encodes it with base64 before uploading it to Pastebin, so the attacker could know the victim address.
The malware creates a service on the victim computer over TOR network in order to open a backdoor to the attacker, so all incoming traffic communication will pass through it.Once infected, the machine posts its encrypted TOR address into Pastebin using the PasteBin Agent mentioned above.
Source: CheckPoint
Links:
Samples:
fe2796b17c3553b37ba9e2a72b0a2c507418d588