FairyTale
FairyTale is an adware that uses malware techniques in order to avoid detection. FairyTale’s application bundle arrived as signed with a legitimate Apple Developer ID, which has since been revoked:
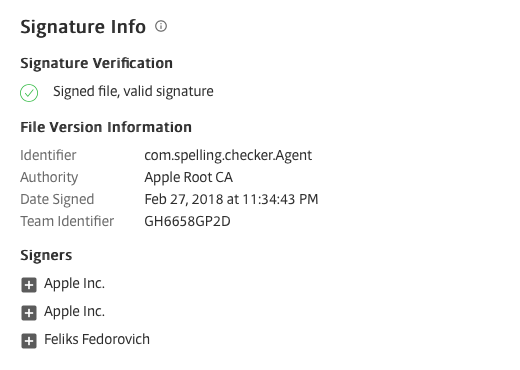
Source: SentinalOne
When executed, the adware will use the xattr command in order to remove its quarantine attribute which is used to identify files that were downloaded from the internet. XProtect, the built in macOS anti-malware only scans files with a quarantine attribute, so that it might download additional files and modify the attributes to avoid XProtect detection.
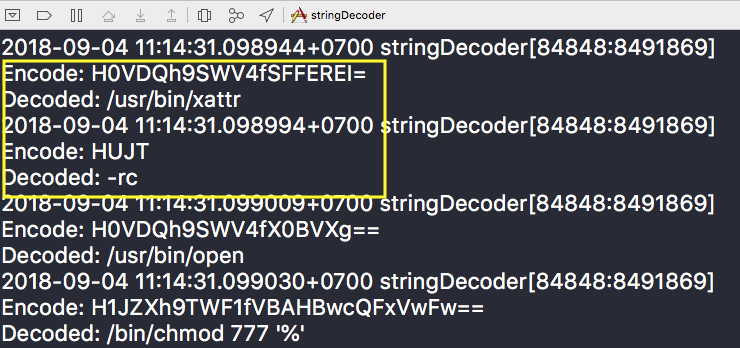
Source: SentinalOne
In addition it will check if its not executed within a virtual machine and if there is any anti-malware product installed on the machine:
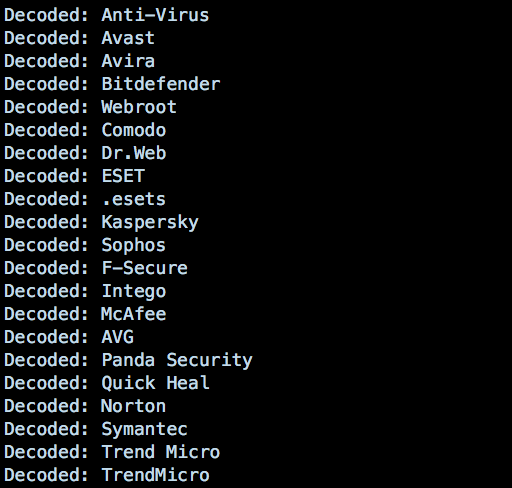
Source: SentinalOne
To survive a system reboot, the malware will create the LaunchAgent “~/Library/LaunchAgents/com.sysd.launchserviced.plist”.FairyTale will modify the default home page and redirect the browser through several pages.
Links: