FileCoder
Even though a first version was found in 2014, which was an unfinished piece of malware that encrypted only its own files (and also that with specific system requirement), a first working version was found in the wild by ESET on 2017.The malware was distributed via BitTorrent, and to disguise its malicious intention, it pretends to be a patcher of applications such as Adobe Premiere Pro or Microsoft office for Mac.It will only infect macOS versions 10.11 (El Capitan) and above, older versions were not infected.Upon execution, the malware generates 25 random character strings, which will be the key that will be used for encryption.The malware uses ZIP command line in order to encrypt files using the 25 chars string it generated.
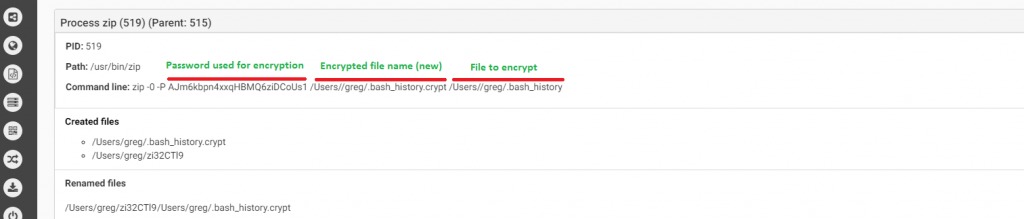
Source: CheckPoint
We can see in the picture above how the malware executes the zip command with the -P command (password protected) to generate new files with a “.crypt” extension and right after that the original file will be deleted.The malware will leave a ransom note asking for 0.25 BTC, even though the malware does not communicate with a C&C, meanig the randomly generated password will not be sent to the attacker, hence it won’t be possible for a victim to decrypt its files back, even if he will pay the ransom.Below we can see the result of FileCoder ransomware after it encrypts the victim’s files, leaving the ransom notes which ask for 0.25 BTC in order to decrypt files:
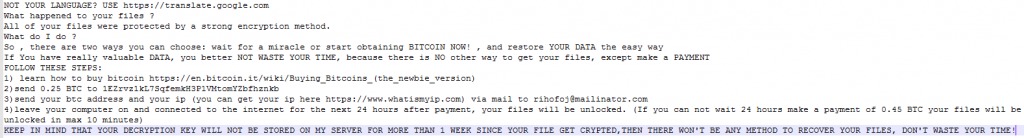
Source: CheckPoint
Links:
Samples:
1b7380d283ceebcabb683464ba0bb6dd73d6e886
a91a529f89b1ab8792c345f823e101b55d656a08
e55fe159e6e3a8459e9363401fcc864335fee321
3820b23c1057f8c3522c47737f25183a3c15e4db