Keydnap
Keydnap is a malware which opens a backdoor to infected machines and steals content of keychain which holds sensitive information such as passwords.The malware uses cunning techniques to trick the user to click on the malicious executable file – it adds an jpg file extensions but with the addition of spaces or other characters, such as “.jpg ” or “.jpg|” so in this way the user might think the file is an image file and will be tempted to click on it, however the OS recognizes the file as executable and once click it will be executed.
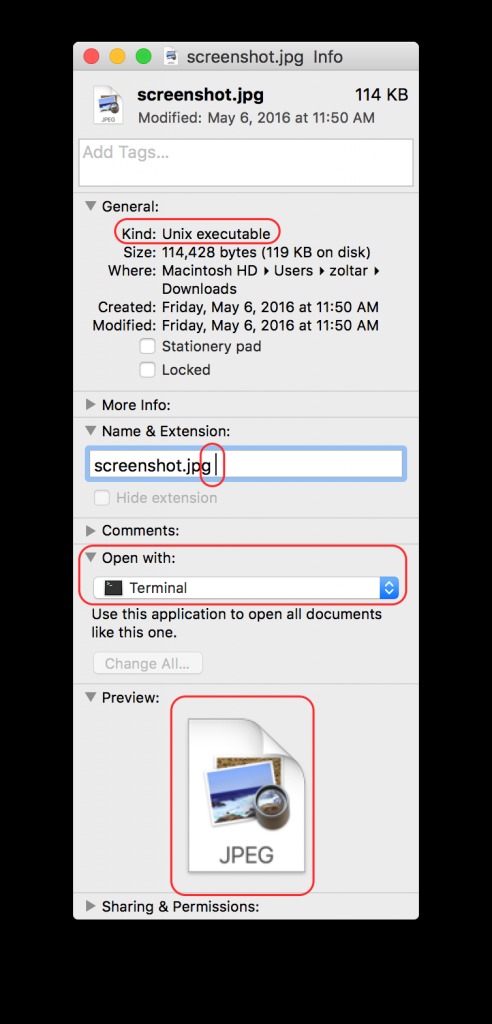
Source: ESET
The malware will drop the file ‘icloudsyncd’ which is the backdoor. It will then create LaunchAgent to start the backdoor in order to survive a reboot.To exfiltrate the passwords stored within the keychain, Keydnap uses an open source POC (proof of concept) project “Keychiandump”.To communicate with its C&C the malware uses onion.to which is a Tor2Web proxy to domains in the dark web, and it uses RC4 encryption in order to encrypt the data it sends to its Command and Control.
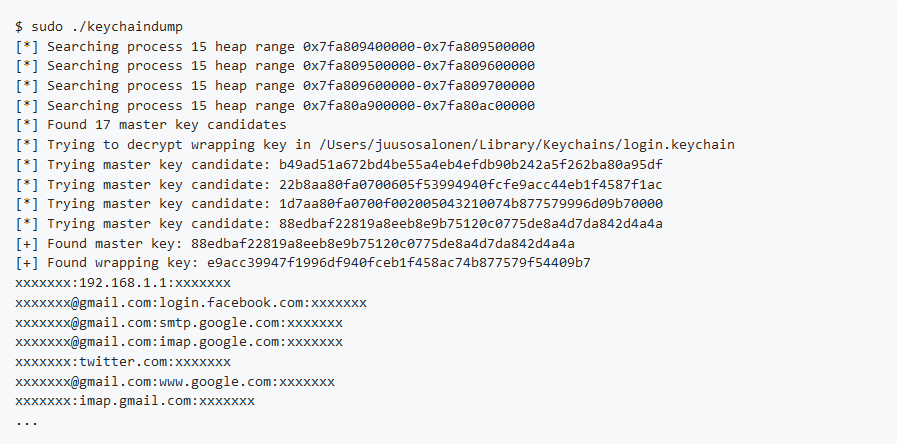
Source: ESET
The backdoor can receive several commands such as an update itself, download and execute additional files, execute a command and send the output to the C2 and more:
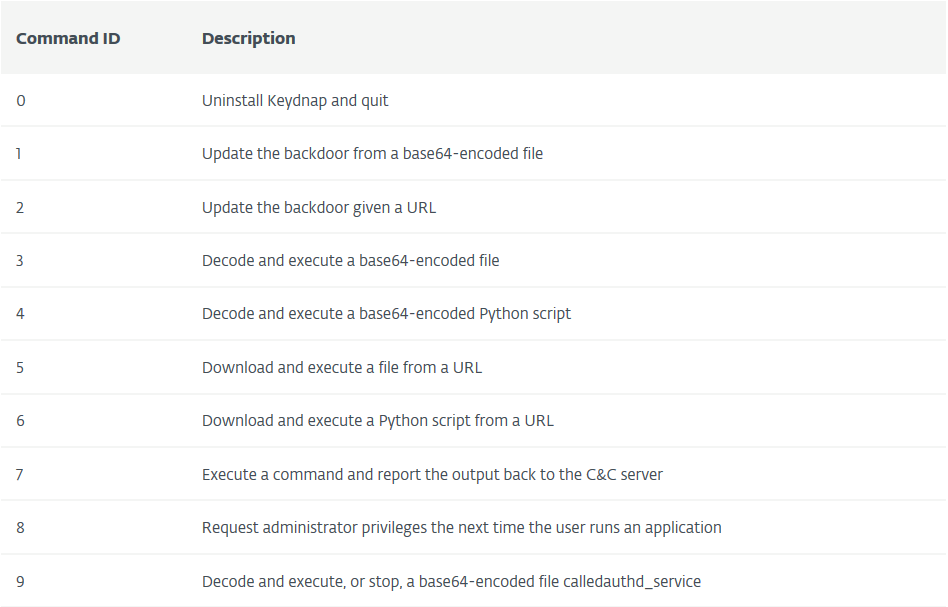
Source: ESET
Another interesting thing about this malware is the way it will try to achieve root permissions if it doesn’t have it. The malware will monitor the number of processes and if two processes will be created in a short time one after the other then the malware will pop a window asking for root privileges to hope the use will fall for this trick.
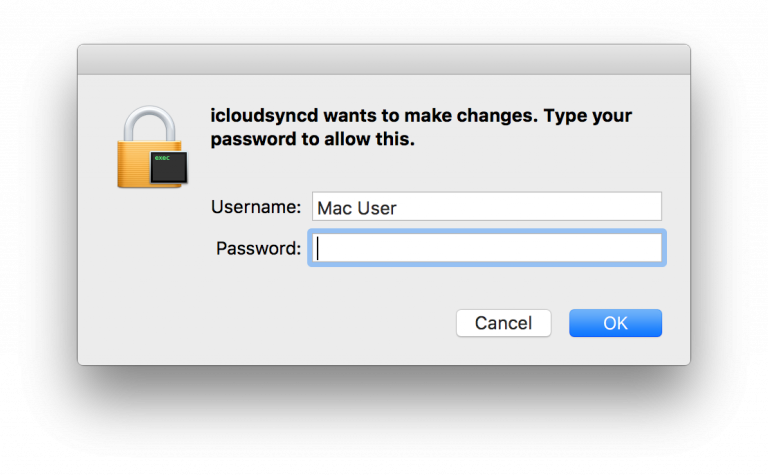
Source: ESET
Links:
Samples:
773a82343367b3d09965f6f09cc9887e7f8f01bf
07cd177f5baf8c1bdbbae22f1e8f03f22dfdb148