Komplex
Komplex is a malware developed by Sofacy group (APT28) to attack individuals using macOS. It’s able to downlaod and execute additional files, execute and delete files, directly interacting with the system shell.The malware contains several components:Binder:Responsible for saving another payload and a decoy pdf document that will be shown on the screen after the malware is executed by using “Preview” application. This is to shift user attention from the malicious activity behind the scene. The pdf file is writing in Russian and might applies to the target users being attack of the malware.The binder will drop an executable file “/tmp/content” which is the second stage of the infection.
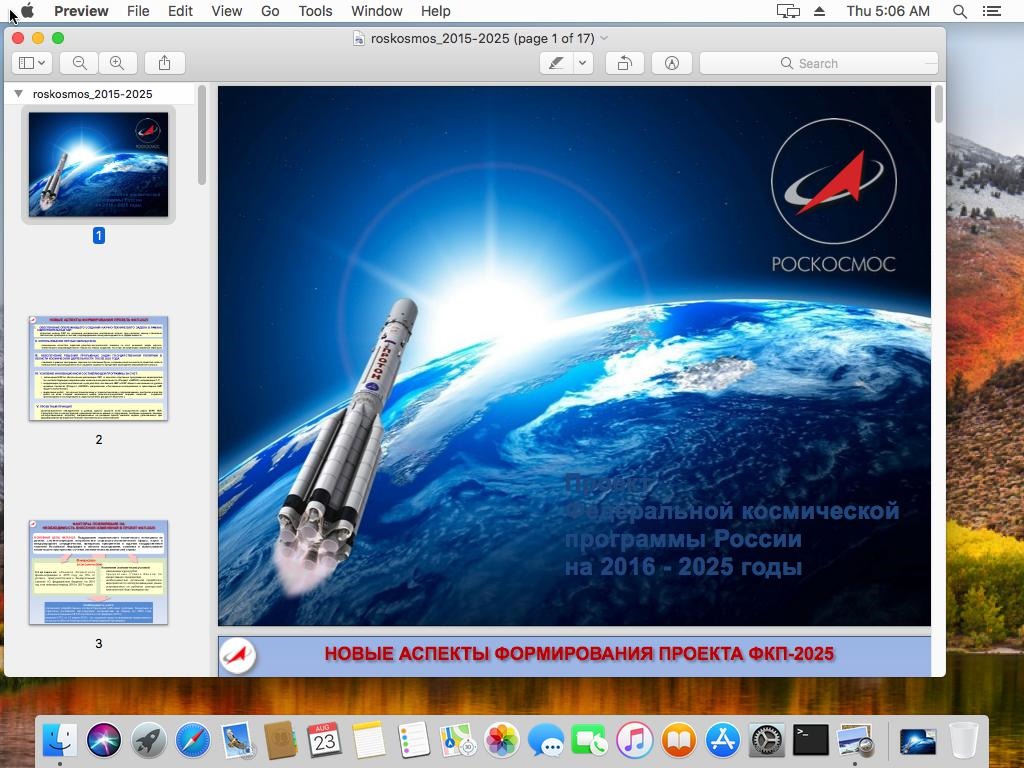
Source: PaloAlto
Dropper: The dropper is responsible to drop the third stage of the malware infection and to achieve persistence on the system. Komplex’s actual payload will be saved as “/Useres/Shared/.local/kextd”.It will create a LaunchAgent at “~/Library/LaunchAgents/com.apple.updates.plist” and will start it using “launchctl”. This is to ensure that the malware survives a system reboot.
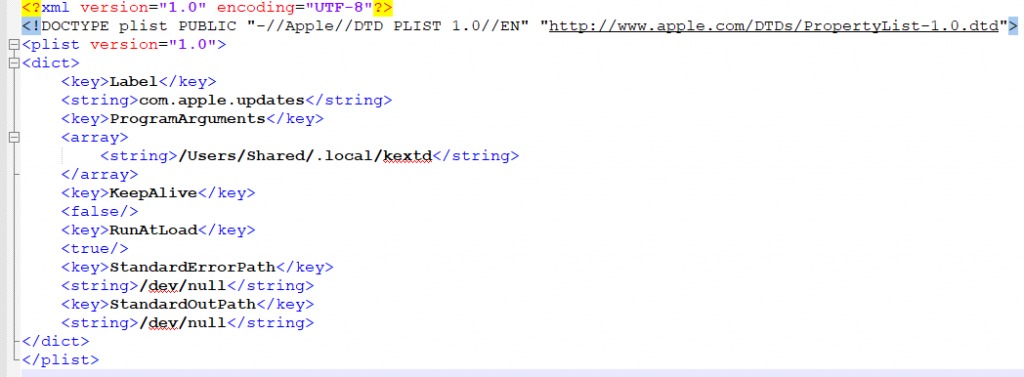
Payload: When executed, the payload first does some anti-debug checks as well as connectivity checks by testing a get request to “google.com”. If those tests pass, it then decrypts its configuration file, which contains the C&C servers as well as a token that will be part of communication encryption between the infected machine and the C&C.It will collect information from the system such as system version, username and process list and send it to the C&C. In return the C2 will send additional command for the malware to execute.Some of the C&C domains were used by other malwares by Sofacy group. Another interesting thing is that there is some code/flow similarity between Komplex and Carberp, a malware targeting Windows users also by Sofacy group.
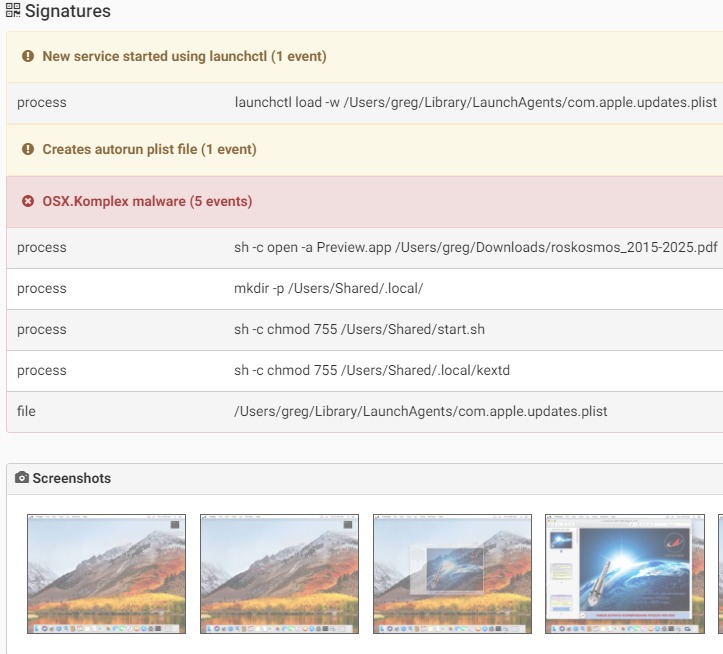
Source: CheckPoint
Links:
Samples:
c7199fb8c605f4b76093cc88f1d80a59fac64ae2
9e73b0457d28b0296befed65e2517ed7a9c1e61d