Linker
Discovered by Intego, Linker is the first malware to exploit a vulnerability in macOS GateKeeper (which is already [disclosed] (https://www.fcvl.net/vulnerabilities/macosx-gatekeeper-bypass){:target=”_blank”})., that enabled adding a symbolic link to remote application located on attacker machine within a legitimate application, and by that bypass the scan of Gatekeeper and XProtect. A video demostrating the attack is [available] (https://www.youtube.com/watch?time_continue=13&v=m74cpadIPZY){:target=”_blank”}.
An attacker could add a symbolic link either to a zip file or .dmg file (Apple Disk Image Format). Intego point that one of the samples was signed with the same Apple Developer ID (“Mastura Fenny”) as the OSX/Surfbuyer adware.
On installation the malware will show itself as Adobe Flash Player, a common thing among macOS malwares.
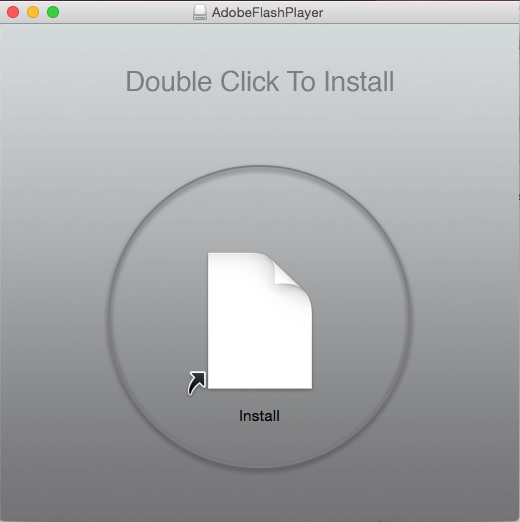
Source: CheckPoint
Althou the remote application was already removed, a research name Adam Thomas has found a PCAP on VirusTotal which contains the remote application that was downloaded when the original application was installed, which at that time was only a bash script that created a temporary file, But since its located on a remote machine it could change any second for testing and place back a malicioius application.
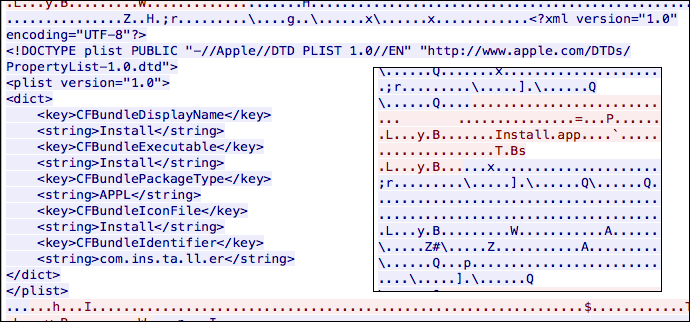
Source: Intego
Links:
Samples:
d53ebf9fe70bce05a00fb6dded971f49b070ed8e10beb0e40d48e3495b274a23
f6bf5b8bb2400aad4ac844f2b94a4e556907f35b44c5ff462fb4e70c0208c9de