MacDownloader
A cross-platform trojan which according to original publication is related to an Iranian Cyber Security Group attacking Windows and macOS users. The malware is distributed via a spear phishing website impersonating “United Technologies” aerospace firm. The page will show an error claiming in French that flash plugin has security flaws:
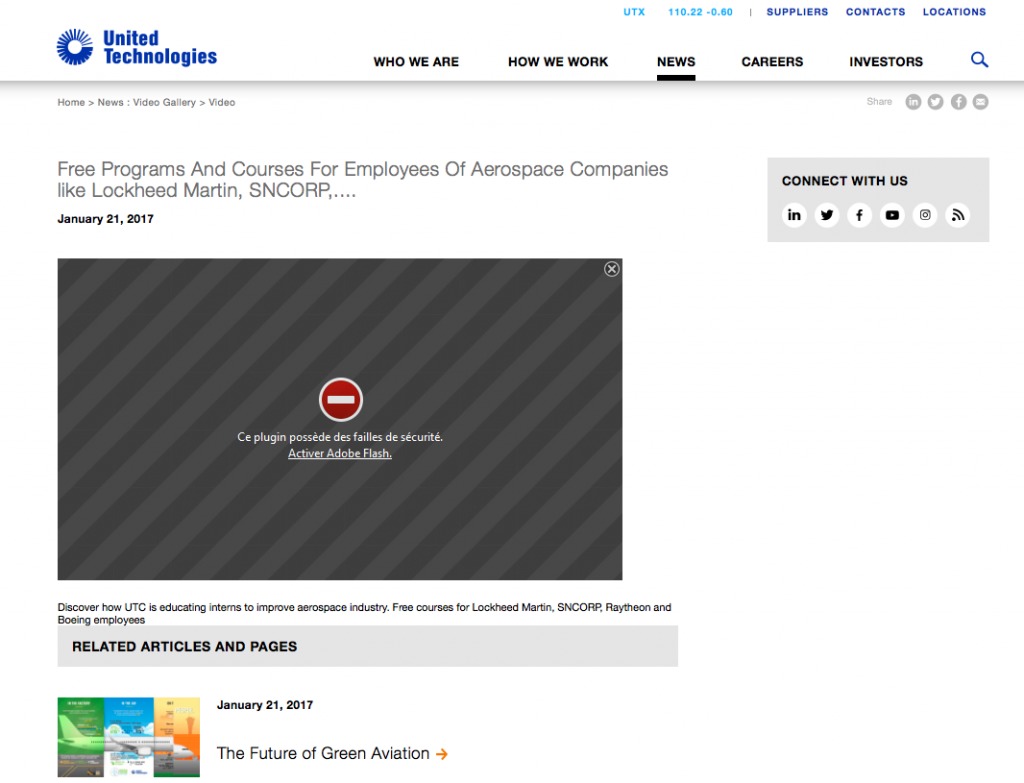
Source: IRAN THREATS
To fix the issue the user will bait to download “Bitdefender Adware Removal Tool”, after the user will click on the update button, a window claiming an adware has been found on the system, and right after credentials windows asks the user for their password in order to fix the problem:
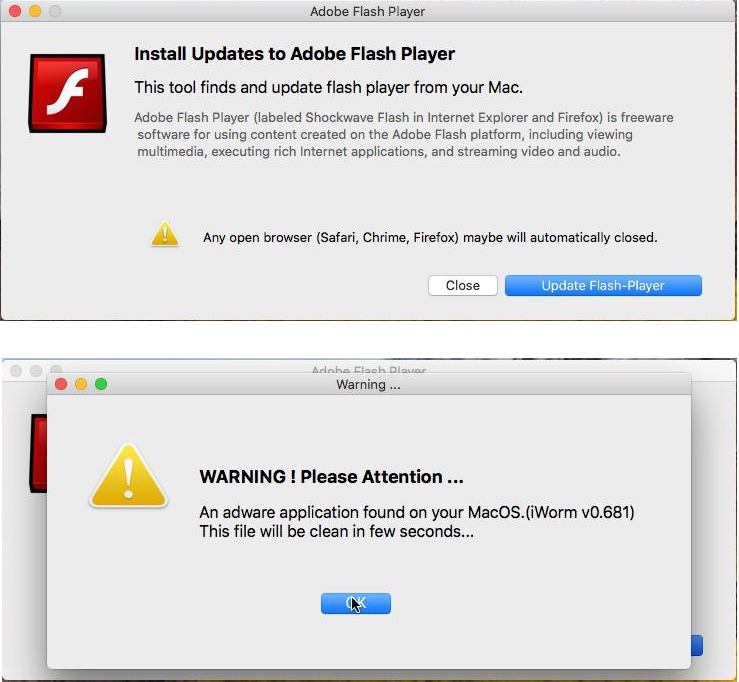
Source: CheckPoint
After gaining the root password, the malware will be able to steal sensitive information from the keychain. It will collects information from the infected machine such as osVersion, user password, keychain files, application and processes list and will store in “/private/tmp/applist.txt”:
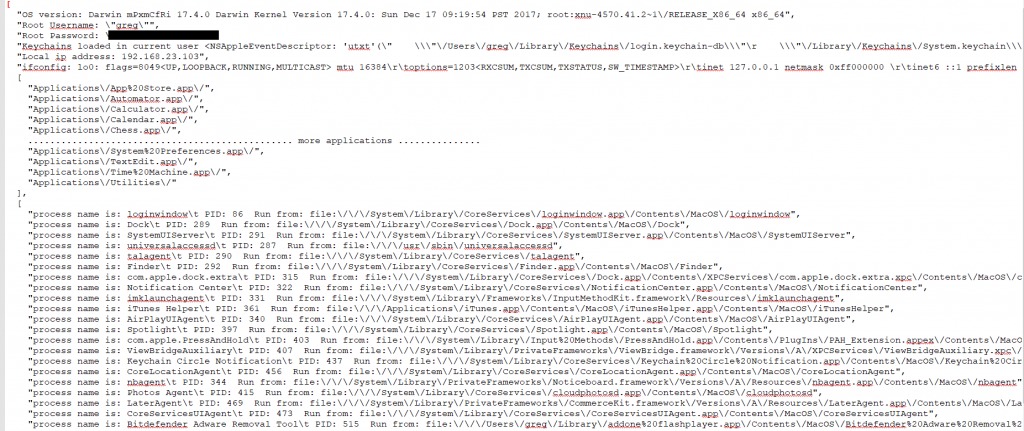
Source: CheckPoint
The malware application bundle contains the file “checkadr.txt” in its Resources folder which contains the C&C address that will be used to send the data collected from the system with a zip file contains keychain files.
Links:
Samples:
52efcfe30f96a85c9c068880c20663db64f0e08346e0f3b59c2e5bbcb41ba73c