MacRansom
MacRansom is the first macOS ransomware offered RaaS (Ransomware as a Service). The malware discovered in 2017 by Fortinet, after the service was published on TOR network.
Source: Fortinet
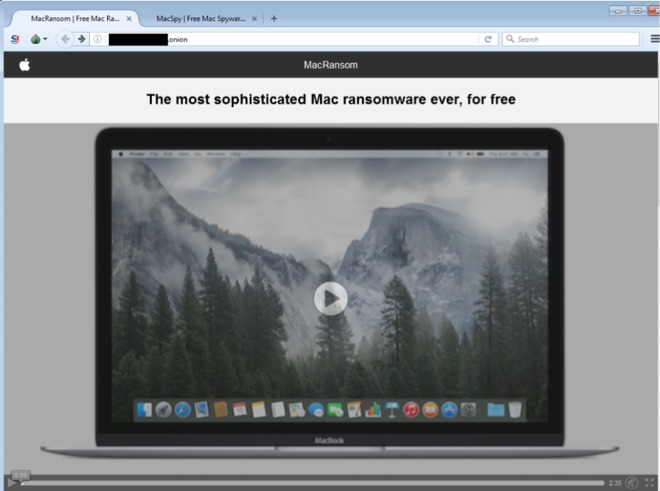
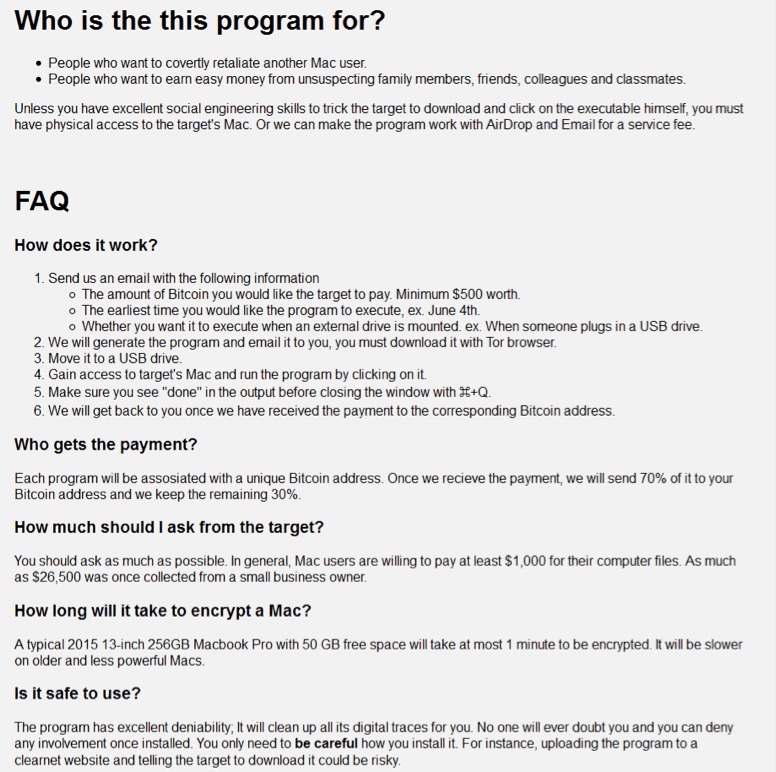
On its web site, the malware explains how the service will work. One who wants to use the service will send details to the authors such as: amount of money they want infected people to pay, initial attack date for the ransom to start encrypting files and more. The MacRansom authors will include in each file a different bitcoin address which will be used to receive ransom payments. The authors will keep 30% from all received ransom BTC payments and will send the remaining 70% to those who are using the service to infect the users.
Source: Fortinet
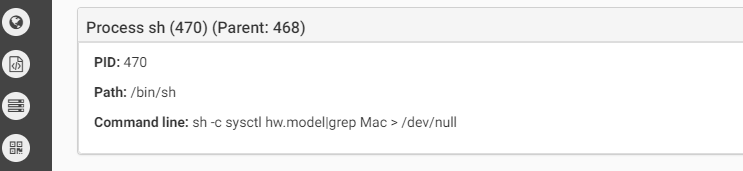
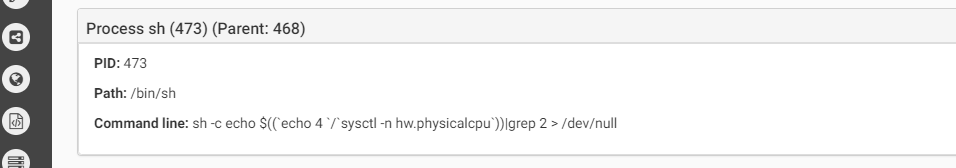
The malware contains anti-debug and anti-vm techniques to make it more difficult for analysis. Below we can see the anti-vm tricks it uses:
Source: CheckPoint
Source: CheckPoint
The first one checks the hardware model. On a real macOS machine the return value will include the word “Mac” (such as “Macmini” or “MacBookPro”) while in the VM the result value will be the name of the VM version such as “VMware”). In the second anti-vm trick, the malware checks the number of processors. In both cases, if the malware does not receive the right answer it will quit.The malware will copy itself as “~/Library/.FS_Store” and will persist by creating the LaunchAgent “~/Library/LaunchAgents/com.apple.finder.plist” to start automatically at system load.The malware will wait for the time it was configured for to start the encryption.It will execute the command below to find all files in the /Volumes folder which have read attribute and are bigger than 8 bytes. all files that will be cought be this command will be executed as parameter for the malware to encrypt.
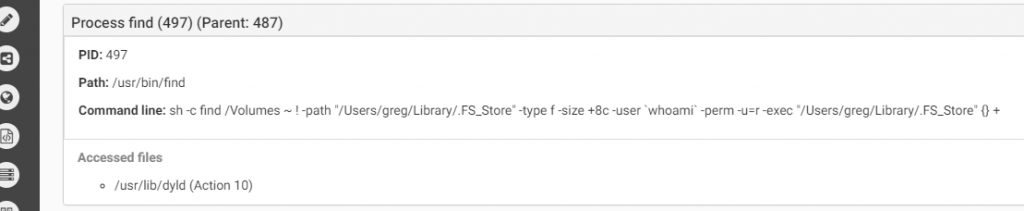
Source: CheckPoint
The malware uses a symmetric key for encryption, however for each file the key is permuted with a random generated number, and since this random number is not saved anywhere, it will be impossible to decrypt them.
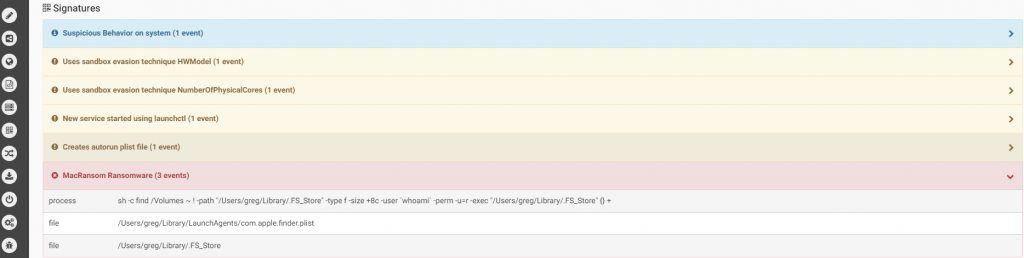
Source: CheckPoint
Links:
- MacRansom: Offered as Ransomware as a Service
- OSX/MacRansom - analyzing the latest ransomware to target macs
Samples:
617f7301fd67e8b5d8ad42d4e94e02cb313fe5ad51770ef93323c6115e52fe98