Mami
OSX/MaMi is a DNS hijacking malware with additional dangerous functionalities in its code, such as taking Screenshots, simulating mouse events, downloading & uploading files, executing additional commands and more.The malware modifies the system’s default DNS setting, so all the DNS requests will be sent to the attacker machines, which can use it to send wrong DNS response. In this way an attacker could send the victim to fake websites and not the intended ones.
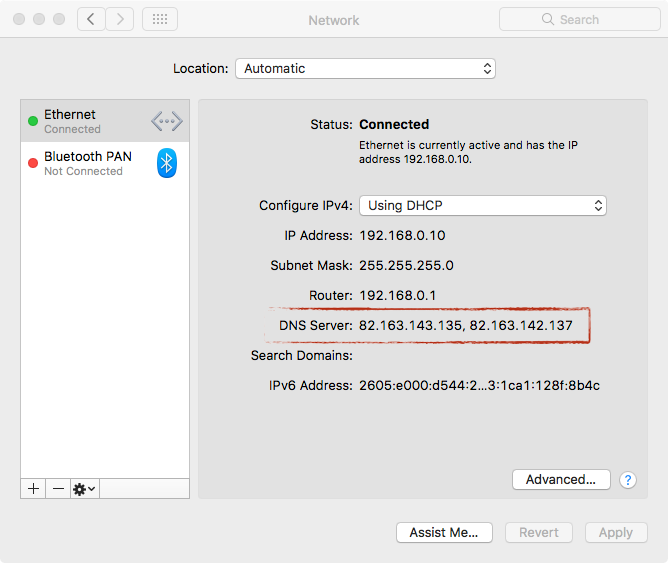
Source: Objective-See
The attacker can also perform a Man In The Middle attack (MiTM) since he controls the actual web address the user will be redirected to. To achieve full control over that, view also secure (https) traffic, the malware adds a fake certificate as a root certificate to the System keychain:
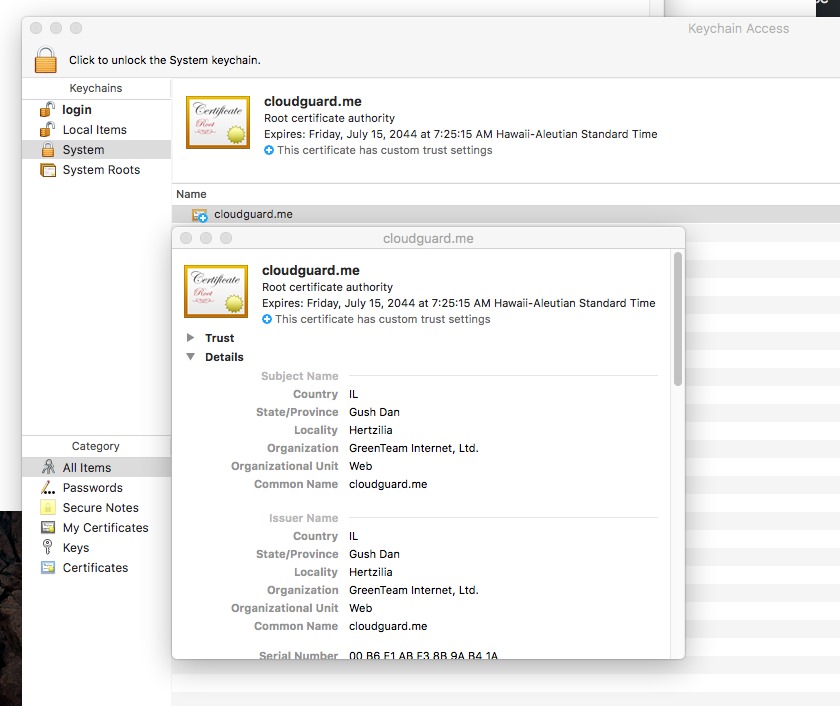
Source: Objective-See
Another interesting fact about the malware are similarities to Windows malware from 2015 which (second link) hijacks the same DNS addresses used in osx/MaMi. Another suspicious thing that points to the similarity is that both the Windows and MacOS malwares certificates have the same fingerprint:
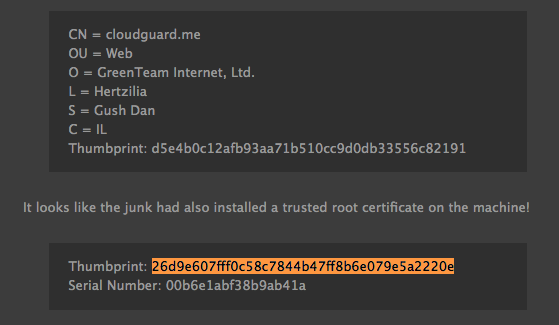
Source: thecomputerperson
Links: