OceanLotus
OceanLotus is a cross-platform malware, exists on both Windows and macOS operating system. It is mostly targeting Chinese infrastructure. Except wide range of available commands the malware uses also Anti-Debug and Anti-VM techniques in order to make its detection harder. When executed, the malware will collect the following information from the system:
- Product Nae and Version
- Machine name
- Is the user is root
- User’s name
- Username
- IOPlatformUUID that will be used as unique infection_id
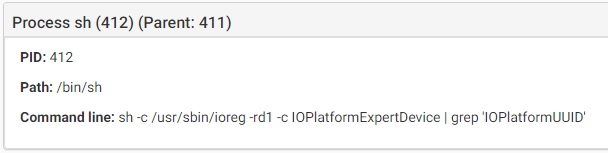
Source: CheckPoint
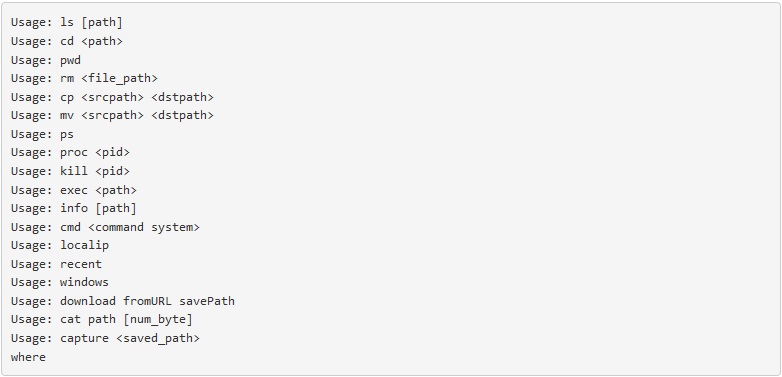
The malware will create a LaunchAgent in order to persist on the system. Below is available command the malware can receive from the C2, for different OceanLotus variants:
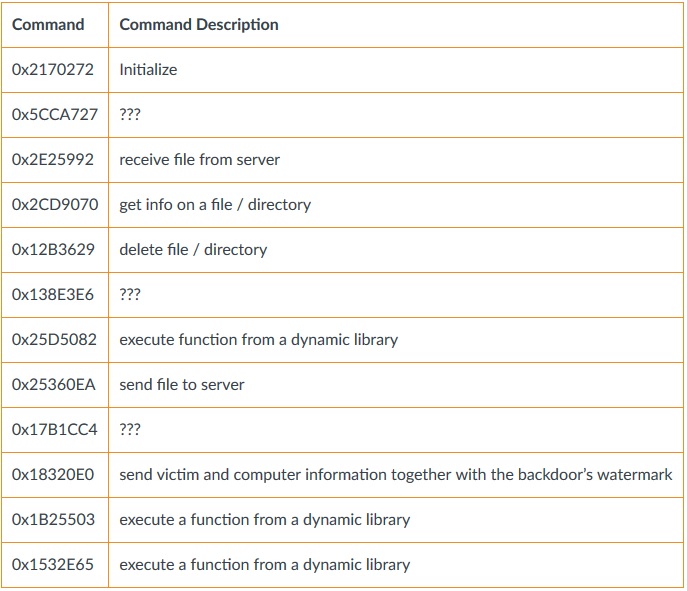
Source: PaloAlto
Links:
- OceanLotus for OS X – an Application Bundle Pretending to be an Adobe Flash Update
- The New and Improved macOS Backdoor from OceanLotus
- OceanLotus: macOS malware update
Samples:
12f941f43b5aba416cbccabf71bce2488a7e642b90a3a1cb0e4c75525abb2888
83cd03d4190ad7dd122de96d2cc1e29642ffc34c2a836dbc0e1b03e3b3b55cff
26e3bd5f1362d8d219a8db745087b6dccc60d6f085f808ff2bd6215058839a75