Systemd_Demsty
Another macOS backdoor discovered on 2017, which was mostly targeting university researchers in Hong Kong.When executed the malware will copy itself as “~/.local/bin/sysetmd”. Then to persist on an infected machine it will create the LaunchAgent “~/Library/LaunchAgents/com.appule.sysetmd.plist” to start the binary.The malware collect and send following information to the C&C:
- OS info (name, version)
- User info (ID, login)
- Computer info (CPU, memory, MAC address)
- IP address
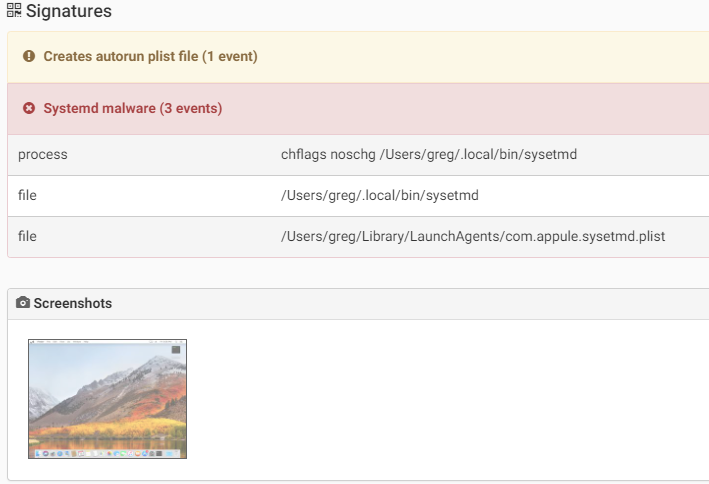
Source: CheckPoint
Below is the list of commands the malware can receive from the attacker:
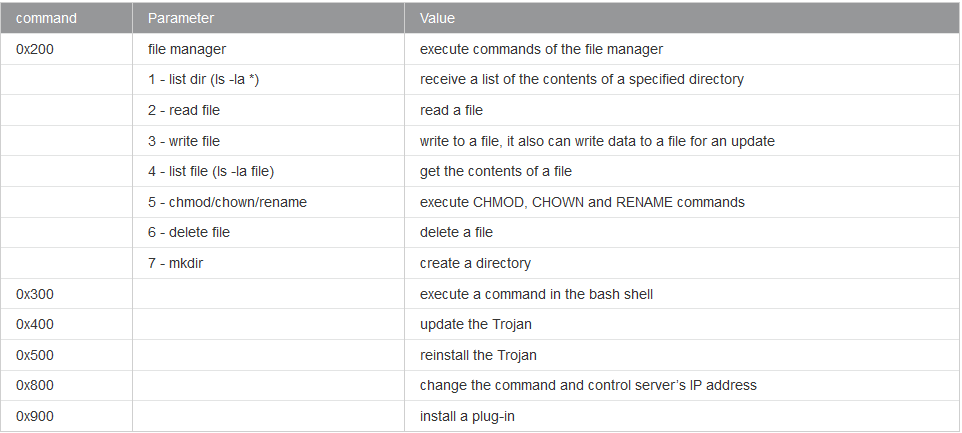
Source: Dr.WEB
Links:
Samples:
3cb1cfa072dbd28f02bd4a6162ba0a69f06f33f0